Article-at-a-Glance
Understanding the basics of Kubernetes RBAC and its importance in cloud environments.
Step-by-step instructions on setting up RBAC with user groups in Kubernetes.
Best practices for implementing the principle of least privilege through RBAC.
Advanced strategies for managing access in complex scenarios, like multi-tenant environments.
Answers to common questions regarding RBAC in Kubernetes.
What is Kubernetes RBAC?
Imagine you’re handing out keys to a treasure chest, but not everyone should open every lock. That’s what Kubernetes Role-Based Access Control (RBAC) is all about – it’s the gatekeeper that ensures only the right people have the right keys to your cluster’s resources. In technical terms, RBAC is a method of regulating access to computer or network resources based on the roles of individual users within an organization.
Why is Access Control Critical?
Access control is like a bouncer for your Kubernetes club. It’s critical because it prevents the ‘party crashers’ – unwanted or unauthorized access – from causing havoc. If everyone had unrestricted access, it would be a security nightmare. By controlling who can do what, you protect your cluster from potential threats and ensure that operations run smoothly.
“Access to Kubernetes Cluster Using RBAC …” from faun.pub and used with no modifications.
Setting Up RBAC in Kubernetes
Let’s roll up our sleeves and get to the nuts and bolts. Setting up RBAC in Kubernetes is like organizing a team where everyone knows their role and has the tools they need – nothing more, nothing less. It’s about assigning the right level of access to the people who need it to do their jobs effectively.
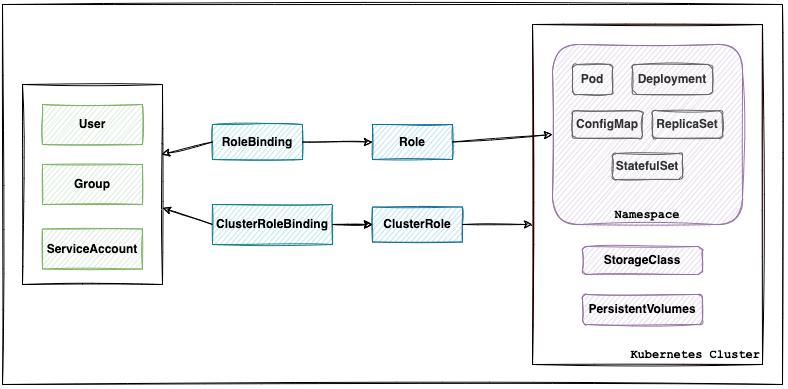
Roles: Defining Permissions for Resources
First things first, define what each member of your team can do by creating ‘Roles’. A Role in Kubernetes is a set of permissions that describe how users interact with different resources like pods, services, or secrets. These permissions include actions like ‘get’, ‘list’, ‘create’, ‘delete’, and more.
RoleBindings: Connecting Users to Roles
Now that you’ve got your Roles set, it’s time to link them to your users. That’s where RoleBindings come in. Think of RoleBindings as the moment you hand out the keys based on the Roles you’ve defined. They are the link between the user and the permissions they’re granted.
ClusterRoles and ClusterRoleBindings: Broad Permissions Across the Cluster
When you need to assign permissions that span across the entire cluster, ‘ClusterRoles’ are your go-to. ‘ClusterRoleBindings’, on the other hand, let you apply those broad permissions to users. They’re like VIP passes, granting access to all areas.
Assigning Users to Groups
Once we’ve got our Roles and RoleBindings in place, it’s time to organize our users. We do this by assigning them to groups. In Kubernetes, a group is simply a collection of users. It’s like putting together a team for a project – each member has a specific role to play. When you assign a user to a group, you’re essentially saying, “You now have the permissions that this group has been granted.”
Implementing Access Control Strategies
With the basics down, let’s talk strategy. Implementing access control is like setting up a security system for your home. You want to make sure it’s strong enough to keep out intruders but flexible enough to allow your family members to move around freely.
Access control strategies in Kubernetes revolve around defining what users can and can’t do. This requires a solid understanding of your cluster’s architecture and the needs of your users. It’s a balancing act – too little access and nothing gets done, too much and you risk security breaches.
Least Privilege Principle in Actions
One of the core principles in setting up access control is the ‘least privilege’ principle. It means giving users only the access they absolutely need to do their jobs, nothing more. This principle is crucial because it minimizes the risk of an attacker gaining access to sensitive parts of your system.
Review the tasks each user performs and adjust their access accordingly.
Regularly audit user access levels and reduce permissions that are no longer needed.
Encourage users to request additional permissions only when necessary.
By sticking to the least privilege principle, you create a secure environment where the potential for damage, either through error or malicious intent, is greatly reduced.
Restricting Access Using Namespaces
Think of namespaces like rooms in a house. Just as you wouldn’t give every visitor access to your bedroom, you don’t want every user in your Kubernetes cluster to have access to all namespaces. Namespaces are a way to divide your cluster into separate areas, each with its own set of permissions.
When you restrict access using namespaces, you’re ensuring that users can only interact with the resources they need. It’s an effective way to organize and secure your cluster, especially as it grows in size and complexity.
RBAC Best Practices for Enhanced Security
Regularly review and update RBAC policies to keep them aligned with current roles and responsibilities.
Use naming conventions for roles and rolebindings that clearly indicate their purpose and scope.
Employ automation tools to manage RBAC policies across multiple clusters or environments.
Adhering to best practices isn’t just about following rules – it’s about fostering a culture of security within your organization.
Regularly Revise and Update Role Permissions
Roles and responsibilities can change over time, and your RBAC policies need to keep up. Regularly revising and updating role permissions ensures that users have access to the resources they need today, not what they needed last year. It’s like updating your wardrobe – what worked for you last season may not be suitable now. For more insights, read our Kubernetes deployment guide which includes strategies and tips for maintaining an effective Kubernetes environment.
Avoid Common Pitfalls in RBAC Policy Definitions
When defining RBAC policies, common pitfalls can trip you up. Here are a couple to watch out for: To ensure you’re on the right track, consider reviewing the core elements of Kubernetes to better understand how RBAC fits into the broader architecture.
First, avoid overly broad permissions. It’s tempting to give a user more access than necessary ‘just in case’ they need it, but this goes against the least privilege principle. Second, don’t forget to remove access when it’s no longer needed. When someone leaves a project or the company, their access should leave with them.
Advanced RBAC Scenarios
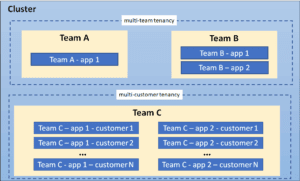
As your organization grows, you’ll encounter more complex scenarios that require advanced RBAC strategies. For example, you might have a multi-tenant environment where multiple teams or companies share the same cluster.
Dealing with Multi-tenant Environments
In multi-tenant environments, where isolation and security are paramount, RBAC plays a crucial role. You’ll need to be meticulous in defining Roles and RoleBindings to ensure that each tenant has access only to their own resources. It’s like having several different businesses operating under one roof, with each needing their own secure space.
Integrating Cloud Provider IAM with Kubernetes RBAC
For those of you already using cloud providers like AWS, Azure, or Google Cloud, integrating their Identity and Access Management (IAM) with Kubernetes RBAC can tighten security even further. This integration allows you to manage user access at both the cloud provider level and within Kubernetes, providing a double layer of protection. It’s like having a security guard at the gate and a lock on your front door.
FAQs
Let’s tackle some frequently asked questions to ensure you’re fully equipped to manage user groups and access control in Kubernetes.
How Do I Begin with Kubernetes RBAC?
To start with Kubernetes RBAC, first ensure your Kubernetes cluster is running version 1.6 or later, where RBAC is enabled by default. Begin by familiarizing yourself with the core concepts: Roles, RoleBindings, ClusterRoles, and ClusterRoleBindings. Next, identify the resources in your cluster and decide who needs access to what. From there, you can start crafting your Roles and RoleBindings to suit your needs.
What Are the Differences Between Roles and ClusterRoles?
Roles are permissions tied to a specific namespace within Kubernetes, whereas ClusterRoles are not limited to a particular namespace and apply to the entire cluster. You can think of Roles as local permissions and ClusterRoles as global permissions.
Roles:
Scoped to a specific namespace
Manage permissions within that namespace
ClusterRoles:
Cluster-wide scope
Manage permissions across all namespaces
Can I Simulate RBAC Policies Before Applying Them?
Yes, you can simulate RBAC policies using tools like ‘kubectl auth can-i’ to check whether a user can perform a specific action. This is like doing a ‘dry run’ to ensure that your policies work as intended before they go live.
How Do Service Accounts Fit Into RBAC Configurations?
Service accounts are special user accounts that are tied to applications or services rather than an individual person. In RBAC configurations, you can assign permissions to service accounts just like you would for regular users. This allows applications running on your Kubernetes cluster to interact with the Kubernetes API securely.
What Methods Can I Employ to Audit RBAC Policies Effectively?
Auditing RBAC policies is crucial for maintaining security. You can use the Kubernetes Audit Log to track changes to Roles and RoleBindings. Tools like ‘kubectl auth reconcile’ can help ensure your RBAC policies match your specifications. Regular audits help you stay on top of any inadvertent changes or drift from your intended access controls.