Key Takeaways
Kubernetes DNSpolicy is crucial for service discovery within your cluster.
The most common DNS policies include ‘Default’, ‘ClusterFirst’, and ‘ClusterFirstWithHostNet’.
‘dnsConfig’ allows for advanced customization of DNS settings in Pods.
CoreDNS plays a pivotal role in managing cluster DNS services.
Understanding and configuring DNS correctly can prevent common issues in Kubernetes deployments.
Unlocking the Potential of Kubernetes DNSPolicy
Imagine you’re in a city where every building is constantly moving. Finding your way around would be a nightmare, right? Well, that’s what it’s like in a Kubernetes cluster without a proper DNS policy. DNSpolicy in Kubernetes is like a map that helps your applications find each other and communicate in the ever-changing landscape of a cluster.
What is Kubernetes DNSPolicy?
Kubernetes DNSpolicy defines how DNS (Domain Name System) queries are resolved within your Pods. It’s like setting up rules for how your children’s phones should find contact information: either use the contacts saved on their phones or look it up in the family’s shared directory. In Kubernetes, this ‘family directory’ is the internal DNS service that resolves service names to IP addresses, making sure your applications can find and talk to each other efficiently.
Why DNS Matters for Your Kubernetes Workloads
DNS matters because it’s all about communication. Just as you wouldn’t want your mail delivered to the wrong address, you don’t want your services sending data to the wrong place. By setting up DNS policies, you’re making sure that your services can reliably discover and connect to the resources they need to function correctly.
And here’s the kicker: without DNS, you’d be stuck using IP addresses directly, which is not only cumbersome but also a recipe for disaster in a dynamic environment like Kubernetes where IPs can change frequently.
The Cornerstones of Kubernetes DNS: Pods, Clusters, and Services
Think of Pods, Clusters, and Services as the fundamental building blocks of your Kubernetes city. Pods are like individual houses, Clusters are the entire neighborhood, and Services are like the public utilities that every house connects to. DNS ties all these together, ensuring that everyone knows how to find each other.
“docker – Kubernetes dns external …” from stackoverflow.com and used with no modifications.
Pods and Their DNS Policy
Let’s dive into Pods. Each Pod in Kubernetes can have a DNS policy set, which dictates how the DNS resolution will work within that Pod. It’s a bit like deciding if a phone in your house should use only the contacts saved on it or also look up numbers in the cloud.
DNS Policy Types for Pods: Default vs. ClusterFirst
There are a few different flavors of DNS policies you can apply to your Pods:
Default: The Pod inherits the DNS configuration from the node it’s running on. This is like using the phone’s contacts without any cloud backup.
ClusterFirst: Any DNS query that doesn’t match the cluster’s domain is forwarded to the upstream nameserver inherited from the node. This is like using the phone’s contacts first, then checking the cloud if the number isn’t there.
ClusterFirstWithHostNet: This is a special case used when a Pod is using the host’s network namespace. It’s like a guest in your house using your phone; they get the same rules as your family.
Most Pods should use the ClusterFirst policy because it ensures that services within the cluster are prioritized over external ones, keeping traffic local and fast.
Customizing Pod DNS Settings with dnsConfig
Sometimes you need more control over DNS than what the default policies offer. That’s where dnsConfig comes into play. It’s like setting up speed dials on your phone for the numbers you call most often. With dnsConfig, you can set custom DNS options for your Pods, such as how to describe a Kubernetes pod with kubectl, ensuring that your applications have the necessary DNS settings they require.
Nameservers: The DNS servers your Pod should use.
Searches: A list of domain names that should be searched when resolving DNS queries.
Options: Fine-tune DNS querying behavior with options like
ndots, which defines how many dots must appear in a name before an initial absolute query will be made.
Customizing DNS settings can drastically improve the efficiency of name resolution in your applications, especially if you’re running a complex microservices architecture. For more details on how DNS settings are configured in Kubernetes, you might want to read about how to describe a Kubernetes Pod with kubectl.
Host Networking and DNS: Understanding ClusterFirstWithHostNet
When a Pod is configured with hostNetwork: true, it shares the network namespace with the node it’s running on. This means it sees the network exactly as the node does. The ClusterFirstWithHostNet policy is used in this scenario to ensure that, despite sharing the network, the Pod can still resolve cluster DNS names correctly.
It’s a bit like having a VIP pass in a crowded event. You’re in the same space as everyone else, but you get to bypass the queues and access areas that are off-limits to regular attendees.
Clusters: Ensuring Smooth Service Discovery
Now, let’s zoom out a bit and look at the cluster level. Clusters are like the backbone of your Kubernetes city, providing the infrastructure that Pods and Services build upon. Ensuring smooth service discovery at this level is like making sure all roads and signs are in place so that everyone can find their way around without getting lost.
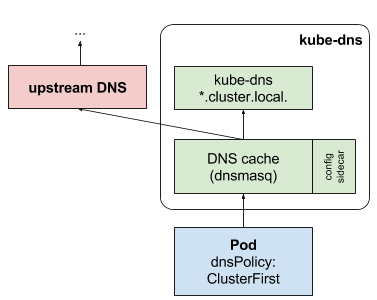
The Role of CoreDNS in Kubernetes Clusters
At the heart of Kubernetes service discovery is CoreDNS, the default DNS server used in recent versions of Kubernetes. Think of CoreDNS as the town hall’s information desk—it’s where all queries about locations go. CoreDNS takes the role of translating service names to IP addresses, so when one service needs to talk to another, it knows exactly where to send the message.
CoreDNS is configured out-of-the-box to work seamlessly within your Kubernetes cluster, but it’s also highly customizable. You can tweak its ConfigMap if you need to change how DNS queries are processed, similar to updating the directory at the town hall for new services or relocations.
Configuring DNS for Multiple Clusters with Federation
For those of you managing multiple Kubernetes clusters, you’ll want to know about Kubernetes Federation. Federation allows you to keep a unified service discovery mechanism across all your clusters, no matter where they’re located. It’s like having a single address book for multiple branches of your family, regardless of where they live.
By using Federation, you can ensure that a service in one cluster can discover and communicate with services in another cluster using a common DNS name. This is particularly useful for failover scenarios, where workloads can be shifted between clusters without any disruption to the service.
For example, if you have clusters across different regions, Federation allows a service in the US cluster to find and communicate with a service in the EU cluster just by using its DNS name, without needing to know the exact location.
Setting up Federation requires some additional configuration, but it’s worth it for the seamless cross-cluster communication it enables.
Services: Navigating DNS Naming Conventions
Services in Kubernetes are like the public utilities in our city analogy—they provide a stable way for Pods to access the resources they need. Understanding how these services get their DNS names is key to making sure your applications can reliably connect to them.
How Services Get Their DNS Names
Each service in Kubernetes is automatically assigned a DNS name when it’s created. This name follows a standard pattern: service-name.namespace.svc.cluster.local. It’s like assigning a street address to a new building so that everyone knows where it is.
This DNS naming convention ensures that every service can be uniquely identified and accessed from anywhere within the cluster. You don’t have to worry about IP addresses; just use the service’s DNS name, and Kubernetes will handle the rest.
Headless Services and Their Impact on DNS
Headless services are a special type of service that, unlike regular services, don’t have a single IP address. Instead, they allow you to connect directly to the Pods behind the service. This is useful for stateful applications that need a stable network identity.
When you create a headless service, DNS will return the individual Pod IPs instead of a single service IP. It’s like having a directory that lists all the apartment numbers in a building rather than just the building’s main address.
Using headless services requires a solid understanding of your application’s networking needs, but they can be incredibly powerful when used correctly.
Best Practices in DNS Configuration
Now that we’ve covered the basics, let’s talk about some best practices for DNS configuration in Kubernetes. These tips will help you avoid common pitfalls and keep your cluster running smoothly.
Allocating Stable IP Addresses to Services
One of the key best practices is to allocate stable IP addresses to your services. While DNS takes care of name resolution, having a stable IP address ensures that any DNS caching mechanisms won’t lead to connectivity issues if a service’s IP changes.
This is like making sure that your building’s address doesn’t change even if the building gets renovated. You can achieve this stability by using static IPs for your services or relying on service objects that maintain their IP addresses throughout their lifecycle.
Keeping DNS Resolution Efficient with Caching
Caching is another important aspect of DNS resolution. Just as you might keep a list of frequently called numbers on your fridge to avoid looking them up every time, Kubernetes can cache DNS queries to speed up resolution times. However, you need to be careful with caching settings to avoid stale records, which can happen if services change frequently.
Configuring DNS caching correctly can significantly reduce latency and improve the performance of your services. It’s all about finding the right balance between freshness and efficiency.
Handling DNS for Stateful Workloads and Sets
Stateful workloads, like databases that need to maintain their identity across restarts, have unique DNS requirements. Kubernetes StatefulSets can help here, providing each Pod in the set with a stable hostname and ordinal index. It’s like assigning a permanent room number to each member of your family in a large house.
When you use StatefulSets, each Pod gets a unique DNS subdomain, which remains consistent no matter where the Pod is rescheduled. This is critical for applications that rely on stable network identifiers.
Remember, the key to simplifying Kubernetes deployments is understanding how the different pieces fit together. By mastering DNS policies, service discovery, and best practices, you’re well on your way to becoming a Kubernetes maestro, orchestrating your services and Pods with ease.
Overcoming Common DNS Issues
Even in the most carefully managed Kubernetes environments, issues can arise. Common DNS problems can disrupt service discovery and communication, but with the right knowledge, you can troubleshoot and resolve these issues swiftly.
Some of the most frequent challenges include DNS lookup failures, which can result from misconfigurations, and DNS latency, which can slow down your applications. It’s like when your internet is slow, and web pages take forever to load; every second counts, especially in a busy cluster.
Additionally, you might encounter issues with DNS caching. Sometimes, a Pod might cache an outdated DNS record, leading to connection errors. It’s like trying to call a friend after they’ve changed their phone number; if you haven’t updated your contacts, you won’t reach them.
Debugging DNS Resolution Problems in Pods
To debug DNS resolution problems, start by checking the DNS configuration inside your Pod. You can do this by executing a shell inside the Pod and using tools like nslookup or dig to test DNS resolution. It’s similar to using a map to trace your route when you suspect you might be lost.
If DNS queries are failing, check the CoreDNS logs for any obvious errors. CoreDNS is your cluster’s DNS server, and its logs can provide clues as to what’s going wrong. It’s like checking the town hall’s visitor log to see who’s been asking for directions.
Remember to also verify your dnsPolicy and dnsConfig settings. Incorrect settings here can lead to unexpected behavior. It’s like ensuring the GPS in your car is set to the correct country; otherwise, the directions it gives won’t make much sense.
Addressing DNS Policy Misconfigurations
When you suspect a misconfiguration, the first step is to review the dnsPolicy and dnsConfig of your Pods. Make sure that they align with the needs of your applications. For instance, if you’re using a headless service for stateful applications, ensure that your Pods are configured to resolve DNS names to the individual Pod IPs.
If you’ve customized your CoreDNS ConfigMap, revert to the default configuration and incrementally apply your changes to identify what’s causing the issue. It’s like retracing your steps when you think you’ve dropped your keys somewhere along your path.
Frequently Asked Questions (FAQ)
In the world of Kubernetes, questions abound. Here are some of the most frequently asked questions about Kubernetes DNSpolicy, answered in a straightforward and practical manner.
Whether you’re curious about overriding DNS settings or what happens when a service is deleted, understanding these aspects is crucial for maintaining a healthy and efficient Kubernetes environment.
Can I override the DNS settings of a Pod?
Yes, you can override the DNS settings of a Pod using the dnsConfig field. This allows you to specify custom nameservers, search domains, and other DNS parameters. However, use this feature with caution, as incorrect settings can lead to connectivity issues.
How does DNS work in clusters with network policies?
DNS works in conjunction with network policies to control the flow of traffic within your cluster. Network policies are like traffic rules, determining which Pods can communicate with each other. DNS resolution will still function, but the actual traffic will be subject to the network policies in place.
Therefore, even if a Pod can resolve the DNS name of another service, network policies may prevent it from establishing a connection if the policies don’t allow it. It’s like knowing the address of a shop but finding the road blocked; you know where it is, but you can’t get there.
What happens to DNS when a Service is deleted?
When a service is deleted, its DNS record is also removed from the DNS server. This means that any attempts to resolve the service’s DNS name will fail, leading to connection errors. It’s as if a business closed down; you can no longer visit it or call it up.
However, there might be a brief period where the DNS record is still cached by clients or within the DNS server itself. During this time, the DNS name may still resolve, but the service will be unreachable since it no longer exists.
How do StatefulSets interact with DNS policies?
StatefulSets work closely with DNS policies to provide stable and unique DNS entries for each Pod. Each Pod in a StatefulSet has a consistent identifier based on its ordinal index, and this is reflected in its DNS subdomain. It’s like assigning a permanent phone extension to each employee in a large office.
This ensures that even if a Pod is rescheduled, it retains its identity, making it easier for other applications to maintain stable connections. It’s particularly useful for distributed systems that require persistent identities, such as databases.
Does Kubernetes support external name resolution?
Kubernetes does support external name resolution. By default, Pods can resolve external DNS names, allowing them to communicate with services outside the cluster. This is handled by the ClusterFirst DNS policy, which forwards queries for non-cluster domains to the upstream nameserver.
If you need more control over external DNS resolution, you can use ExternalName services or customize your CoreDNS configuration to integrate with external DNS providers. This flexibility is one of the many reasons Kubernetes is such a powerful tool for modern application deployment.
In conclusion, understanding Kubernetes DNS policy is essential for ensuring that your applications can find and communicate with each other effectively. By mastering DNS policies, service discovery, and best practices, you can avoid common issues and maintain a robust Kubernetes environment. Remember, DNS in Kubernetes isn’t just about connecting services; it’s about creating a reliable network for your applications to thrive.