Primary Points
- Terraform uses HashiCorp Configuration Language (HCL) and a declarative approach, while Pulumi offers flexibility with multiple programming languages, such as Python, TypeScript, Go, and C#.
- State management varies greatly between the tools, with Terraform using state files and Pulumi providing automated state management through its service.
- Terraform has a more mature ecosystem with extensive provider support, while Pulumi leverages existing programming language ecosystems for testing, packaging, and reusability.
- Teams with existing programming expertise may find Pulumi’s learning curve easier, while those who prefer a dedicated infrastructure language often lean toward Terraform.
Terraform vs Pulumi: The IaC Battle You Need to Know
Infrastructure as Code (IaC) has completely transformed how we build and manage cloud resources, turning what was once a manual, error-prone process into programmatic, version-controlled deployments. Leading this revolution are Terraform and Pulumi, two powerful tools that enable teams to define infrastructure using code. While they share the same fundamental goal, their approaches vary greatly in ways that can impact your team’s productivity and success. This comprehensive comparison will help you navigate the nuances of both platforms to determine which best aligns with your organization’s needs.
When it comes to choosing between Terraform and Pulumi, it’s not just about what each tool can technically do. It’s about what works best for your team’s workflow, your team’s skills, and your long-term infrastructure goals. SlickFinch supports both tools because we understand that the infrastructure landscape is complex and different use cases require different solutions. Whether you’re building out a startup’s first cloud infrastructure or managing resources across multiple providers at enterprise scale, understanding the strengths and limitations of each tool is key to making the right choice.
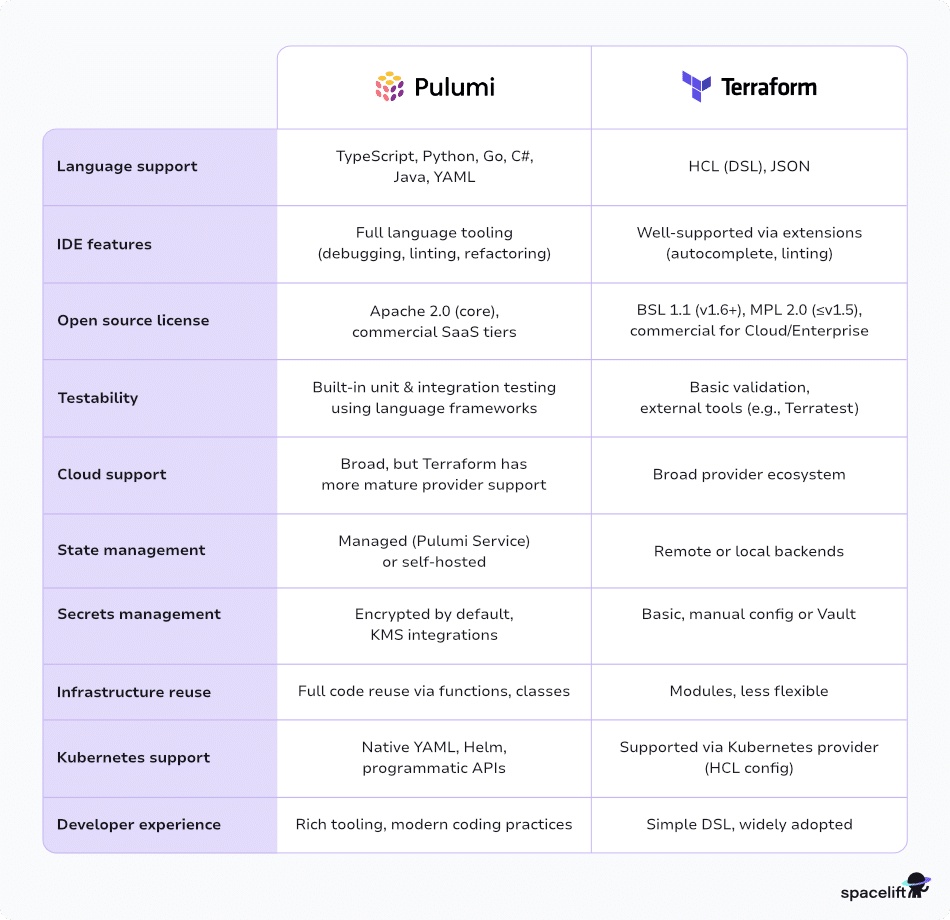
“Pulumi vs. Terraform : Key Differences …” from spacelift.io and used with no modifications.
The Transformation of Infrastructure Management with These Tools
Terraform and Pulumi are both tools that transform infrastructure management by doing away with manual configuration processes and replacing them with code-defined resources. This shift brings numerous benefits such as reproducibility, version control, automated testing, and consistent deployments across environments. Both tools follow a desired state model where you define what you want your infrastructure to look like, and the tools calculate and execute the necessary changes to achieve that state. This approach greatly reduces the risk of configuration drift and improves the auditability of infrastructure changes.
The Main Differences Summarized
The biggest difference between these tools is how they handle code. Terraform uses its own HashiCorp Configuration Language (HCL), which is a declarative language made specifically for defining infrastructure. On the other hand, Pulumi lets you use general-purpose programming languages like Python, TypeScript, Go, and C#. This difference affects everything from how development workflows and testing approaches are handled to team adoption and integration patterns. Terraform focuses on infrastructure-specific constructs and patterns, while Pulumi allows developers to use their existing programming knowledge, libraries, and tools.
Why Manual Infrastructure Management Is Slowing You Down
Before we go further into Terraform vs Pulumi, let’s first understand why infrastructure as code has become so crucial. Managing infrastructure manually via web consoles or CLI commands presents many challenges that only get worse as your organization grows. While point-and-click methods might seem easier at first, they quickly become roadblocks that reduce flexibility and increase risk.
The Unseen Expenses of Manual Infrastructure Provisioning
There are numerous hidden costs associated with manual infrastructure provisioning that go beyond simply clicking buttons. When infrastructure is not codified, the knowledge becomes concentrated within certain team members, creating risky dependencies and restricting your ability to scale operations. Documentation becomes outdated, and the actual state of your infrastructure becomes more and more unclear. Perhaps the most expensive issue is the inability to consistently recreate environments, which leads to the infamous “it works on my machine” problems that development teams often face. These problems grow with each new resource added, creating an unsustainable method for managing infrastructure.
Scaling Challenges That Require Automation
As your cloud infrastructure expands, manual management becomes significantly more complex and prone to errors. A few resources can quickly grow into hundreds or thousands, spanning multiple regions, accounts, and providers. At this level, tracking dependencies, ensuring security compliance, and maintaining consistency is virtually impossible without code-based automation. Performance optimization, cost management, and resource organization all need systematic methods that only infrastructure as code can offer. Without automation, teams often find themselves constantly putting out fires instead of focusing on innovation and delivering value.
Version Control Shortcomings in Conventional Methods
Manual changes to infrastructure do not have the strong version control that contemporary engineering teams depend on. Without infrastructure based on code, there is no clear record of who made which changes, when, or why. Rollbacks become operations with a high level of risk, often impossible without causing disruptions to the service. The inability to track changes means that security vulnerabilities can go unnoticed, and compliance audits become nightmarish exercises in forensic investigation. Infrastructure as Code addresses these issues by offering the same benefits of version control to infrastructure that developers have had with application code for decades.
Why Infrastructure as Code is a Game Changer
Infrastructure as Code is a transformative approach to managing cloud resources. Instead of getting lost in console UIs or running individual CLI commands, teams can express their desired infrastructure state in code files. This method brings the best practices of software development into the realm of infrastructure management, resulting in a reliable, repeatable process that can be automated, tested, and reviewed in the same way as application code.
Terraform and Pulumi both implement the IaC philosophy, but they do it in different ways that reflect their design philosophies. Understanding these differences is crucial to making an informed decision that will best suit your organization’s needs.
Comparing Terraform and Pulumi’s Approaches to Infrastructure Code Management
Both Terraform and Pulumi provide solutions to the main issues of manual infrastructure management, but they do so in distinct ways. Terraform utilizes a specific infrastructure language that has clear patterns for defining resources and managing dependencies. In contrast, Pulumi integrates infrastructure management into the general software development ecosystem, enabling teams to manage infrastructure using the same languages and tools they use for application development. These differing philosophies result in practical differences in how teams adopt, use, and maintain infrastructure code bases over time.
Terraform: Infrastructure Management Powered by HCL
Since its launch in 2014, Terraform has led the Infrastructure as Code scene, offering a specialized method for defining cloud resources. Its unique HashiCorp Configuration Language (HCL) was specifically created for infrastructure definition, with syntax and patterns fine-tuned for resource declarations and their connections. This focused approach has made Terraform popular among infrastructure teams looking for a dedicated tool with consistent patterns across all providers.
The architecture of Terraform is designed around a central engine that handles HCL configurations, manages state, and works with provider plugins to create, update, or delete resources. This division of responsibilities has allowed Terraform to keep a consistent user experience while supporting a continually expanding ecosystem of infrastructure providers.
Using HashiCorp Configuration Language for Declarative Configuration
HashiCorp Configuration Language (HCL) is a declarative language that describes the infrastructure resources and their desired state. Instead of defining step-by-step procedures like imperative programming languages, HCL declares the resources that should exist and their configurations. The Terraform engine then determines the necessary actions to make the real world match this declaration. This method reduces complexity by abstracting the implementation details and API calls, allowing engineers to focus on the infrastructure they need, not how to create it.
Terraform’s Human-Friendly Configuration Language (HCL) has a syntax that is easy to read and requires very little boilerplate. It uses blocks to define resources, data sources, variables, and outputs. Even if you have limited programming experience, you should be able to understand a Terraform configuration. But don’t let its simplicity fool you; it’s also powerful enough to handle complex infrastructure needs.
Managing State
Terraform’s state management system is a key part of its functionality. It uses a state file to keep track of all the resources it manages, their current configurations, and metadata about dependencies. This state file is Terraform’s way of knowing what’s really going on, and it uses it to plan changes by comparing the desired configuration with the current state. This approach is powerful, but it does require careful management of the state file, particularly in team environments where there might be changes happening at the same time.
Module Ecosystem
Terraform’s module system allows for code to be reused by creating composable, shareable infrastructure components. Modules encapsulate resources that are related into functional units. These can be versioned, shared, and reused across projects. The Terraform Registry acts as a central repository for public modules, offering pre-built solutions for common infrastructure patterns from database clusters to networking configurations. This ecosystem has grown to include thousands of modules covering virtually every major cloud service, dramatically reducing the code teams need to write from scratch.
Features of Terraform Cloud and Enterprise
HashiCorp provides Terraform Cloud and Terraform Enterprise as managed solutions for teams who are using Terraform on a large scale. These platforms offer workflows for collaboration, secure management of state, enforcement of policy, and integration with systems for version control. Advanced features such as Sentinel policy as code allow organizations to enforce standards for security, compliance, and architecture across all deployments of infrastructure. For organizations at the enterprise level with strict requirements for governance, these offerings provide capabilities that are valuable and go beyond the open-source core of Terraform.
Pulumi: Infrastructure Programming in Multiple Languages
Pulumi offers a fundamentally different approach to Infrastructure as Code by allowing developers to use the programming languages they are already familiar with, rather than a domain-specific language. This approach brings the full power and flexibility of general-purpose programming to infrastructure definition, allowing teams to leverage their existing language expertise and tooling. Since its launch in 2018, Pulumi has gained significant traction, particularly among organizations with strong software development cultures.
Pulumi doesn’t create a new language. Instead, it offers SDKs for well-known languages like TypeScript/JavaScript, Python, Go, C#, and Java. These SDKs offer consistent patterns for defining infrastructure. At the same time, they let developers use language features like loops, conditionals, functions, and classes. This helps create more dynamic, flexible infrastructure code.
Utilising Preferred Languages (Python, TypeScript, Go, etc.)
Pulumi’s multi-language support gives teams the freedom to pick the language that aligns best with their current skill sets and preferences. Python developers can use Python to define infrastructure, JavaScript teams can utilise TypeScript, and Go aficionados can continue using Go. This adaptability removes the requirement to learn a new syntax and conceptual model, potentially lessening the learning curve for teams already proficient in these languages. More importantly, it lets teams use the same language for both application and infrastructure code, creating a more cohesive development experience.
Aside from the comfort of syntax, using general-purpose languages also gives you the advantage of using each language’s suite of libraries, testing frameworks, and development tools. TypeScript users will appreciate the strong typing and IDE integrations, Python users will love the simplicity and extensive package library, and Go users will appreciate the strong performance and compile-time checks. This ecosystem advantage also extends to the documentation tooling, formatting utilities, and static analysis capabilities that are already established for each language.
Infrastructure Design with an Object-Oriented Approach
With Pulumi, you can use programming languages to design your infrastructure in an object-oriented way. This is something you can’t do with declarative configuration languages. You can make classes that represent components of your infrastructure. You can also use inheritance and composition patterns to create clean abstractions and reuse your code. This approach lets you create high-level constructs that can handle complex infrastructure patterns and present simple interfaces. If your organization has complex infrastructure needs, this ability to create rich abstractions can greatly simplify things and make it easier to maintain your infrastructure.
The object-oriented approach is not only limited to infrastructure components but also extends to the interaction between these components. Unlike Terraform, which relies solely on string interpolation for referencing other resources, Pulumi allows the passing of complete objects between resources. This is done with type checking to ensure compatibility. This makes the code more robust, reduces runtime errors, and makes the intent clearer.
Integrated Testing Features
Pulumi’s seamless integration with conventional software testing frameworks sets it apart from the rest. Your infrastructure is defined using common programming languages, which allows you to take advantage of pre-existing unit testing frameworks such as Jest, pytest, or Go’s testing package to validate your infrastructure code. This makes it possible to use test-driven development for infrastructure, including the capability to mock cloud provider APIs and confirm that your code generates the expected resources with the right configurations. For teams that already use test-driven development, this smooth extension to infrastructure code can greatly enhance quality and assurance, especially when considering public cloud vs private cloud environments.
What Pulumi Service and Team Features Offer
Pulumi Service offers collaboration features, state management, and deployment history for teams using Pulumi. It is similar to Terraform Cloud in that it provides secure state storage, team management, and integration with CI/CD systems. The service includes policy enforcement through Pulumi CrossGuard, which allows teams to define custom policies in their preferred programming language rather than a separate policy language. For organizations that prefer consistent tooling across application and infrastructure domains, Pulumi’s approach offers a more unified experience with fewer context switches.
How Language Choice and Developer Experience Differ
The most significant difference between Terraform’s HCL and Pulumi’s programming language approach is the language choice. This choice doesn’t just influence syntax preferences. It also has a profound impact on developer workflows, testing strategies, and team collaboration patterns. Understanding these experiential differences is key to making an informed decision that suits your team’s strengths and working style.
Which is Better for Your Team: HCL or Programming Languages?
For infrastructure, Terraform’s HCL is a dedicated language that has a streamlined feature set and consistent patterns across providers. It is excellent at expressing infrastructure resources clearly with minimal syntax noise. This makes configurations easily readable, even for those who are new to the language. The constrained nature of HCL is designed to limit complexity, preventing elaborate programming patterns that might obscure the infrastructure intent. For infrastructure-focused teams that value clarity and consistency over programmatic flexibility, HCL provides a straightforward, accessible approach.
By using a programming language approach, Pulumi allows for the full power and flexibility of languages such as TypeScript, Python, and Go in infrastructure definition. This approach allows for more dynamic code generation, stronger abstractions, and integration with existing development toolchains. Teams can use conditional logic, loops, functions, and classes to create more adaptable infrastructure code that can react to different conditions or requirements. For teams that are development-focused and already proficient in these languages, Pulumi can feel like a natural extension of their existing skills rather than having to learn a separate configuration language. For more insights on infrastructure tools, check out this comparison of Consul vs Etcd.
Comparing the Learning Curve
If your team is new to Infrastructure as Code, you might find that Terraform has a slightly less steep learning curve. This is because HCL has a focused scope and straightforward syntax. The declarative nature of HCL aligns well with infrastructure concepts, and there is a clear mapping between code blocks and resulting resources. The documentation and community resources for Terraform are extensive, providing abundant examples for common scenarios across all major providers. This accessibility makes Terraform particularly suitable for teams transitioning from manual infrastructure management to code-based approaches.
The learning curve for Pulumi is heavily dependent on the team’s existing programming language expertise. For developers who are already proficient in the supported languages, Pulumi may actually present a lower barrier to entry than learning HCL from scratch. However, Pulumi introduces cloud infrastructure concepts within a programming context, which can sometimes create confusion about the boundary between build-time and runtime execution. Teams must understand how Pulumi’s programming model differs from traditional application development, particularly regarding how resource dependencies are tracked and managed.
Approaches to Code Reusability
Both Terraform and Pulumi offer ways to reuse code, but they do so in different ways and with different capabilities. Terraform’s module system is a structured way to package reusable components of infrastructure, with clearly defined input variables and outputs. These modules can be shared via version control or the Terraform Registry, allowing teams to build up libraries of patterns for infrastructure. However, there are limitations to Terraform modules in terms of how they can be parameterized and combined, and sometimes they require code to be duplicated when the variations needed don’t fit with the design of the module.
Pulumi utilizes native language constructs for code reusability, such as functions, classes, and packages. This provides more flexible composition patterns and higher-level abstractions than the typical Terraform modules. Developers have the ability to create truly parameterized components with complex logic determining their configuration, or construct class hierarchies that share common functionality while specializing for different use cases. This flexibility does require more discipline to maintain consistent patterns across a codebase, as the freedom of general-purpose programming languages can lead to divergent approaches if not carefully managed.
Comparing State Management
Both Terraform and Pulumi must keep track of the current state of infrastructure to figure out what changes need to be made during deployments. Their methods of managing the state reveal their overall philosophies and have a significant impact on team workflows, security considerations, and operational practices. It’s crucial to understand these differences when determining which model is the best fit for your organization’s needs and limitations.
How Terraform Manages State
At the heart of Terraform’s state management are state files. These files keep a meticulous record of all managed resources, their attributes, and metadata. By default, Terraform stores this state in a local file. However, for team environments, it is recommended to use remote backends like S3, Azure Blob Storage, or Terraform Cloud. The state file is Terraform’s source of truth about the real world. It uses it to plan changes by comparing the desired configuration with the current state. This explicit state management gives teams direct visibility and control over the state data. However, it also makes them responsible for securing and managing access to this sensitive information.
When you work with Terraform state, you need to understand concepts like state locking (which prevents concurrent modifications) and state refreshing (which syncs with reality). More advanced scenarios might require state manipulation using commands like terraform state mv or terraform import to handle edge cases or migrations. While this direct interaction with state is powerful, it can also be complex and requires careful attention to avoid errors that could affect the integrity of your infrastructure.
State Storage Options in Pulumi
Pulumi provides a more abstract approach to state management, with state data usually stored in the Pulumi Service by default. This managed approach makes the user experience more straightforward by managing state locking, concurrent access, and secure storage in the background. For teams who cannot use the Pulumi Service or prefer not to, alternative backends such as AWS S3, Azure Blob Storage, Google Cloud Storage, or even local file storage are available. This flexibility meets different security and compliance requirements while keeping a consistent workflow regardless of the backend.
Compared to Terraform, Pulumi’s state management is more automated, so users don’t have to manually control as many state manipulation commands in their regular workflows. This reduces the mental effort required by operators, but it may occasionally require help from Pulumi when complex state situations arise. For teams that value ease of operations over direct control of state, Pulumi’s model can help alleviate daily concerns about state management.
Security Factors for Both Methods
State files usually hold confidential data such as resource IDs, connection strings, and occasionally even login information, making their security crucial. Terraform’s method obliges teams to meticulously set up backend authentication, encryption, and access controls to safeguard state data. Companies need to put in place explicit procedures for state access and think about extra encryption for extremely sensitive environments. The visibility of state in Terraform makes security a more overt factor in workflow design and access control.
By default, Pulumi’s Pulumi Service offers built-in encryption, access controls, and audit logging. In the case of self-managed backends, Pulumi’s design encourages the separation of configuration from state through features like configuration encryption, similar to the security considerations of Terraform. Both tools support the encryption of sensitive values in state, but the way they implement these capabilities differs, reflecting their overall approach to managing infrastructure secrets.
Support for Providers and Resources
How many infrastructure providers a tool supports and how deeply it supports them is a big deal. Both Terraform and Pulumi have a lot of providers, but they handle how they develop, maintain, and integrate them differently. Knowing these differences can help you decide which tool is a better fit for what you need to do now and later.
Leading Cloud Service Providers (AWS, Azure, GCP)
Terraform and Pulumi both provide extensive support for leading cloud service providers, such as AWS, Azure, Google Cloud, and others. Historically, Terraform has had a slight advantage in the scope of resources supported due to its longer presence in the market and dedicated provider teams at HashiCorp. However, Pulumi has quickly bridged this gap by utilizing Terraform’s provider ecosystem through its provider bridging technology. For most common cloud services, both tools offer similar resource coverage, with any differences generally confined to newer or more specialized services.
Both tools have their own unique speed when it comes to adapting to new cloud services and features. Terraform’s provider development process is more centralized, with HashiCorp maintaining core providers, while Pulumi can sometimes move faster by generating providers from cloud provider APIs. Both approaches have advantages – Terraform’s process may produce more thoroughly tested integrations, while Pulumi’s can deliver access to new cloud features more quickly in some cases.
Support for Various Providers
Aside from the big cloud providers, both Terraform and Pulumi support a wide array of other infrastructure providers for services such as Cloudflare, MongoDB Atlas, Datadog, and many others. Due to Terraform’s longer existence, it has a larger ecosystem of providers contributed by the community, especially for niche or specialized services. Its provider registry includes hundreds of providers that cover everything from major SaaS platforms to specialized networking equipment. Pulumi takes advantage of this ecosystem through provider bridging and also offers native providers for many popular services.
If your organization uses multiple specialty providers, it’s a good idea to check the specific support status and maturity for each tool. Some providers might have better support in one ecosystem than the other, especially for less common or newer services. Both communities are actively contributing to expanding provider coverage, but Terraform’s larger user base often means there are more community-developed integrations for specialized tools.
Developing Custom Providers: A Comparison between Terraform and Pulumi
If you’re an organization that needs to manage custom or internal infrastructure services, both tools provide ways to develop custom providers. To develop a provider with Terraform, you need to know how to program in Go and understand Terraform’s plugin protocol. The development process includes creating resource schemas, implementing CRUD operations, and managing state conversions. This is not a simple task and requires dedicated engineering resources. However, once you’ve developed a custom Terraform provider, it integrates perfectly with the standard workflow and can be shared internally or with the public.
Pulumi provides several methods for developing custom providers, including a dynamic providers feature that allows for direct resource creation and requires less boilerplate than Terraform provider development. For more complex needs, Pulumi allows for the creation of full-featured providers, with the option to generate them from OpenAPI specifications or build them from scratch using TypeScript or Go. This flexibility provides teams with multiple ways to support custom infrastructure, with the level of investment varying depending on the complexity and reusability requirements.
Deployment Patterns in Practice
While the technical features of these tools are important, how they fit into actual engineering workflows is crucial to their practical value. Both Terraform and Pulumi support modern deployment patterns, but they do so in different ways that reflect their design philosophies and target users. Understanding these practical differences can help you decide which tool is a better fit for your organization’s operational practices.
Approaches to CI/CD Integration
Terraform is integrated into CI/CD pipelines via command-line operations that can be included in any workflow system. Common patterns include running terraform plan in pull request checks to validate changes and terraform apply in deployment stages after approval. HashiCorp provides official GitHub Actions and other CI integrations, while the wider community has created plugins for almost every CI/CD system. Terraform Cloud and Enterprise offer more integration options including API-triggered runs, policy checks, and notifications.
Pulumi’s CI/CD integration works in a similar way, but it uses its programming language to provide more in-depth integration options. The Pulumi CLI includes commands such as pulumi preview and pulumi up, which are similar to Terraform’s plan and apply commands. Pulumi also provides language-specific SDKs for automation, which allow for more than just simple CLI calls to control deployments. This Automation API allows you to build custom deployment workflows in your preferred language and integrate Pulumi operations directly into existing applications or services, rather than just calling them from shell scripts.
Managing Drift and Compliance
Drift in infrastructure happens when actual resources differ from their coded definitions, often due to manual changes or modifications from external sources. Terraform handles drift through its plan and refresh operations, which compare the current state of a resource with the expected configuration and can identify any differences. For compliance requirements, Terraform provides Sentinel (in Enterprise) for policy-as-code enforcement during the planning stage, preventing changes that are not compliant from being implemented. These features offer crucial safeguards for maintaining the integrity of the infrastructure and compliance with security.
Pulumi uses its preview and refresh commands to detect drift, much like Terraform. When it comes to enforcing compliance, Pulumi CrossGuard allows you to use policy-as-code in the same programming languages you use to define your infrastructure, instead of a separate policy language. This uniformity means teams can use the same development practices for policy code as they do for infrastructure code, including testing and version control. Both tools allow for automated drift detection through scheduled runs, but the specifics of how this is done differ based on their respective platforms.
Managing Multiple Environments
In many organizations, they will have multiple environments such as development, staging, and production. Each of these environments will have similar but distinct infrastructure configurations. Terraform handles this through workspaces and variable files. This allows the same code to be deployed with different parameters across different environments. Teams will typically organize multi-environment deployments using either workspace-based patterns (single codebase with environment-specific state) or directory-based patterns (separate configuration directories for each environment sharing common modules). Both of these patterns have their advantages depending on the size of the team and the complexity of the infrastructure.
Pulumi manages deployments across multiple environments using its stacks concept, which are separate infrastructure instances that each have their own state and configuration. Stacks can use the same code but have different configuration values for each environment, similar to Terraform workspaces. Pulumi’s use of a programming language allows for more dynamic handling of configurations, including the ability to generate settings specific to each environment programmatically or pull configuration from external systems. This adaptability can make it easier to manage complex deployments across multiple environments with many configuration variations.
How Performance and Scale Affect Infrastructure
As your infrastructure deployments become larger and more complex, performance becomes a bigger concern. Both Terraform and Pulumi need to efficiently manage large resource graphs, complex dependencies, and concurrent operations. The way they approach these challenges is a reflection of their different architectures and can affect how long deployments take, how many resources they require, and how well they scale in practice.
Handling Large Infrastructure
When it comes to large deployments, Terraform’s performance is affected by its execution model. The model processes the entire resource graph in memory, and for infrastructures with thousands of resources, this could mean more memory usage and longer planning times as the state file and resource graph get bigger. But Terraform has made several optimizations over the years to improve performance with large state files, such as better caching and more efficient graph algorithms. Organizations that manage large-scale infrastructure with Terraform usually adopt patterns like state splitting (using multiple smaller state files) and module composition to maintain performance as scale increases.
Due to its programming language roots, Pulumi’s execution model is a bit different, but it faces similar basic problems with large infrastructure graphs. Its performance characteristics vary somewhat by language runtime – Go programs may run faster than Python or Node.js due to differences in language performance. Pulumi offers parallel resource processing for very large deployments, which can speed up deployments when many resources can be created at the same time. Like Terraform, Pulumi deployments benefit from logical separation into multiple stacks when the resource count becomes very large.
Comparing Execution Times
There are many variables that affect the deployment execution time, such as the number of resources, their types, provider API rate limits, and dependency chains. Both Terraform and Pulumi build dependency graphs and execute operations in the best order, but they do so in slightly different ways. Terraform’s execution is highly optimized for its declarative model, with efficient change detection that minimizes unnecessary operations. Its mature provider implementations often include optimizations for common scenarios, which can reduce execution time for standard patterns.
The execution time of Pulumi is affected by both its infrastructure operations and the overhead of the language runtime. The initial startup cost for language runtimes such as Node.js or Python may add a slight overhead compared to Terraform’s purpose-built executor, especially noticeable in smaller deployments. However, Pulumi’s support for parallel operations can provide performance benefits in deployments with many independent resources. In practice, for most deployments, the latency and rate limits of the provider API tend to dominate the execution time rather than the differences specific to the tool.
Patterns of Memory Usage
Memory usage during infrastructure operations influences both the local development experience and the resource requirements for CI/CD. The memory footprint of Terraform is mainly determined by the size of the state and the complexity of the resource graph. For most deployments, memory usage stays within reasonable limits, but very large states (thousands of resources) can require a lot of memory during the planning and application phases. The explicit state file model provides teams with visibility into this growth and opportunities to optimize through state splitting when necessary.
The memory usage of Pulumi is a combination of the requirements of the infrastructure state and the characteristics of the language runtime. The memory patterns can be affected by different language choices. For example, Go usually uses less memory than Node.js or Python for the same operations. For deployments that are very large, optimizing memory may involve both the organization of the infrastructure (dividing it into multiple stacks) and best practices specific to the language. Both tools are continually optimizing to improve their memory efficiency. However, regardless of the tool you choose, very large deployments will always require careful management of resource use.
How to Choose the Right Tool for Your Needs
Now that you have a good grasp of what each tool can do and how they work, you need to decide which one is the best fit for your organization. You’ll need to consider the skills of your team, the requirements of your project, and the factors specific to your organization to figure out which tool will be the best for managing your infrastructure.
When Terraform Is the Preferred Option
Terraform often excels in infrastructure-focused teams with dedicated operations personnel who appreciate its specialized approach and extensive provider ecosystem. Organizations with substantial investments in existing Terraform modules and workflows may find the consistency and reliability of Terraform compelling, particularly if they’re already using Terraform Cloud or Enterprise capabilities. The simplicity and limitations of HCL can be beneficial for teams looking to uphold consistent infrastructure practices across multiple groups with varying skill levels.
When there is a strict separation between the application and infrastructure teams, with dedicated personnel responsible for defining and managing the infrastructure, Terraform can be a better choice. It has a mature ecosystem, with plenty of community resources, third-party tools, and established best practices that can help speed up adoption and reduce the risks of implementation. For organizations that value operational stability over programming flexibility, Terraform’s focused approach and slow and steady feature evolution are a good fit.
Why Pulumi is Sometimes the Better Choice
Pulumi is often the better choice for organizations that focus on development, where engineers are responsible for both the code of the application and the infrastructure. This is because Pulumi allows teams to use the same languages and tools for both. If a team is already skilled in TypeScript, Python, Go, or any of the other languages that Pulumi supports, they can use those same skills for their infrastructure. This could reduce the time it takes to learn new skills and allow for more complex programming patterns. Plus, the ability to use standard testing frameworks, package managers, and development tools can create a more unified experience for engineers. This could lead to increased productivity for teams that handle everything from the application to the infrastructure.
Switching Between the Two
Companies are not permanently stuck with either tool, as there are ways to switch between the two. If you want to switch from Terraform to Pulumi, you can use Pulumi’s tf2pulumi converter to translate HCL configurations into Pulumi code in your chosen language. This tool can handle most standard Terraform configurations, but if you have a complex or highly customized setup, you may need to make some manual adjustments. If you want to switch from Pulumi to Terraform, the process is less automated but still doable. You would need to manually recreate the infrastructure definitions in HCL, potentially using Pulumi’s ability to export its state for import into Terraform.
First Steps: Your Initial Project
If your team is considering these tools, there’s no substitute for practical experience with a real-world project. By setting up a basic cloud infrastructure project using both tools, you can get a feel for their workflows, syntaxes, and how they operate. This hands-on comparison often uncovers subtle distinctions in the developer experience that you wouldn’t notice just by reading the documentation, especially when dealing with hybrid cloud vs multi-cloud environments.
A great beginner project could include basic infrastructure elements such as a virtual network, compute instances, and managed services that show resource dependencies and configuration complexity. By creating the same infrastructure with both tools, teams can decide which method best fits their work style and needs.
Getting Terraform Ready for AWS Deployment
To get started with Terraform, you need to install the CLI, set up AWS credentials, and create initial configuration files. The standard project structure includes a main.tf file to define resources, variables.tf for input parameters, outputs.tf for values to extract, and possibly a providers.tf to set up the AWS provider. Terraform’s workflow is consistent: write configuration, initialize the working directory with terraform init, check syntax with terraform validate, preview changes with terraform plan, and implement them with terraform apply. This consistent workflow makes it simple to understand what’s happening at each stage, with clear visibility into planned changes before they’re implemented.
Building the Same Infrastructure with Pulumi
When it comes to creating the same project in Pulumi, you start by installing the Pulumi CLI and selecting your preferred programming language. You then initialize a new project with pulumi new aws-typescript (or whatever language you choose) and create resource definitions in your main program file (for example, index.ts for TypeScript). The workflow in Pulumi is similar to Terraform’s in concept, but the commands are different: pulumi preview to view the planned changes and pulumi up to implement them. The main difference is in how you define your infrastructure – you use programming constructs instead of configuration blocks.
- Resource definitions use constructors rather than blocks (e.g., new aws.ec2.Instance() vs resource “aws_instance”)
- Dependencies are handled through variables and object references rather than string interpolation
- Configuration uses both Pulumi’s config system and native language mechanisms like environment variables
- Code organization follows language conventions (modules, classes, functions) rather than Terraform’s block structure
These differences highlight the fundamental contrast in approach between the two tools – Terraform’s infrastructure-specific configuration language versus Pulumi’s programming language foundation. Which feels more natural depends largely on your team’s background and preferences.
While both tools achieve the same infrastructure provisioning tasks, they offer vastly different development experiences. Terraform might be more appealing to those with an infrastructure background but limited programming experience. On the other hand, Pulumi might be more appealing to software developers already familiar with programming concepts and tools.
Development Experience Comparison
Once the initial setup is complete, the daily development experience shows some key differences between Terraform and Pulumi. Terraform’s development cycle is based on the HCL syntax, and the editing and validation cycles are pretty straightforward. The constraints of the language make it easy to understand what can be done and how to set up configurations. However, these same constraints can sometimes necessitate workarounds for complex logic. The HashiCorp Terraform extension provides IDE support, which includes syntax highlighting and basic validation. However, it does not have some of the advanced features that developers might expect from full-fledged programming language tools.
Common Advanced Techniques
Even though Terraform and Pulumi have different ways of doing things, they both have many advanced features that are crucial for managing enterprise infrastructure. Both tools have complex methods for managing secrets, enforcing company policies, and managing deployments across multiple accounts. By understanding these common features, you can compare the tools based on how they implement these features instead of whether or not they have them.
Managing Secrets
When it comes to infrastructure management, securely handling sensitive values such as API keys, passwords, and certificates is of utmost importance. Terraform achieves this through its encrypted sensitive variables feature. This feature allows certain values to be marked as sensitive to prevent them from appearing in logs and console output. For external secret storage, Terraform can integrate with vault providers and pull secrets from systems like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault during deployment. By separating secrets from configuration code, security is maintained while keeping infrastructure definitions version-controlled.
Like Terraform, Pulumi has a built-in secrets management system that encrypts sensitive values in configuration and state storage. This prevents these values from appearing in logs and console output, which reduces the risk of accidental exposure. For larger business needs, Pulumi integrates with external secret management systems through its Pulumi ESC (Environments, Secrets, and Configuration) feature. This provides a unified interface to various backend secret stores.
Both tools offer the ability to define custom secrets encryption for organizations with specific security requirements. The decision between the two often comes down to integration preferences and existing organizational patterns rather than fundamental differences in capability.
- Both support marking values as sensitive/secret to prevent exposure in logs
- Both integrate with external secret management systems
- Both encrypt sensitive values in state storage
- Both support rotation and versioning of secrets through their respective platforms
Policy as Code Implementation
As infrastructure deployments scale across teams, enforcing organizational standards and compliance requirements becomes essential. Terraform Enterprise addresses this through Sentinel, a policy as code framework that evaluates planned changes against defined policies before allowing them to proceed. Policies can enforce security rules, cost controls, naming conventions, or any other organizational requirements. For open-source users, third-party tools like Open Policy Agent (OPA) can provide similar capabilities, albeit with less direct integration.
Pulumi’s CrossGuard feature allows policy to be implemented as code using the same programming languages that are used for infrastructure definitions. This means that those writing policies can use languages they’re already familiar with instead of having to learn a new policy language. Policies can be applied across an entire organization through the Pulumi Service, ensuring that they’re enforced consistently across all projects and teams. CrossGuard policies can also be used for more complex requirements, such as implementing complex logic, calling external APIs, and generating detailed violation reports.
Managing Multiple Accounts and Regions
Contemporary cloud architectures often have to manage multiple accounts and regions due to reasons such as security isolation, compliance requirements, or geographic distribution. Terraform manages multi-account deployments through provider aliases that define multiple configurations of the same provider with different credentials or regions. This approach allows a single Terraform configuration to provision resources across different accounts and regions, with explicit control over where each resource is created. For more complex scenarios, organizations usually adopt module compositions that separate resources by account while maintaining coordination through outputs and remote state.
Pulumi also provides similar features through its provider initialization options, which allow multiple instances of the same provider but with different configurations. The foundation of the programming language allows more dynamic approaches to multi-account management, like iterating through a list of regions or accounts to create resources in each. Pulumi’s stack references feature makes it easier for independently deployed stacks to communicate, enabling coordinated deployments across account boundaries while maintaining separation of concerns.
Deciding Between Terraform and Pulumi
The decision to use either Terraform or Pulumi for your infrastructure code management is a big one. It’s not just about your immediate needs, but about the future of your operations. You’ll need to consider your team’s dynamics, technical requirements, and future plans. A careful evaluation of these factors will lead to the most successful adoption of either platform.
Evaluating Your Team’s Abilities
When choosing between Terraform and Pulumi, you should take a long, hard look at your team’s current skills and preferences. If your team has a strong background in software development and is already familiar with one of the languages supported by Pulumi, they may find it easier and more productive to use Pulumi. They will be able to leverage their existing programming knowledge, which can speed up adoption and enable them to use more sophisticated infrastructure patterns without needing additional training. For these teams, using Pulumi may reduce the learning curve and increase productivity from the get-go.
On the other hand, teams with a stronger background in operations and less experience in programming might find the more focused approach of Terraform easier to handle. The declarative nature of HCL works well with infrastructure concepts, providing a clear connection between code blocks and the resulting resources. The limited language of Terraform decreases the chance for overly complicated code patterns that could make maintainability more difficult, potentially leading to more consistent practices across teams with different skill levels.
Factors of Project Complexity
The tool you choose should be influenced by the complexity and nature of your infrastructure needs. If your project requires complex logic, sophisticated abstractions, or deep integration with application code, Pulumi’s programming language foundation could be beneficial. The ability to use programming constructs such as inheritance, higher-order functions, and complex data structures allows for more adaptable and dynamic infrastructure definitions. If your organization is building platform layers or infrastructure frameworks for other teams to build upon, these capabilities could be especially useful.
For those with simpler infrastructure needs or teams that value clarity and consistency over the ability to program, Terraform might be the better choice. The constrained nature of HCL can encourage more standard patterns across teams, which could lead to better maintainability and knowledge sharing. If your project’s main goal is to provide reliable, straightforward infrastructure without complex logic or abstractions, Terraform’s focused approach could lower the cognitive overhead and make implementation less complex.
Thinking About Long-Term Maintenance
Infrastructure code can last for years, often outliving the original team that developed it and changing to accommodate new needs. It’s important to think about how each tool sets you up for long-term maintenance to avoid potential issues down the line. Terraform is known for its stability and slow evolution, which means that configurations that were created years ago will typically still work with newer versions, even if they don’t take advantage of the latest features. Because Terraform is so widely used, there are a lot of people who are familiar with the tool, which could make it easier to find new team members as your team changes over time.
Pulumi’s method connects infrastructure more intimately to programming language ecosystems, complete with their evolution and best practices. This linkage can be beneficial if it matches your organization’s overall technology strategy, allowing for consistent patterns across application and infrastructure domains. However, it also implies that infrastructure code may evolve in tandem with language practices and idioms, possibly necessitating more active upkeep to stay up to date with changing standards. Assessing this trade-off necessitates considering your organization’s willingness for ongoing fine-tuning versus stable, unchanging patterns. For organizations in healthcare, understanding healthcare compliance is crucial when considering cloud migration strategies.
Common Questions
While examining both Terraform and Pulumi, a few questions repeatedly come up. By answering these recurring questions, we can give you a better idea of how to make the best decision based on your unique needs and limitations. Keep in mind that these answers are up-to-date, but both tools are constantly evolving and improving.
Scratching beneath the surface of these frequently asked questions often unearths key factors that may not be immediately obvious from simply comparing features. The real-world effects of licensing, migration routes, and specific use cases can have a major bearing on the triumph of your infrastructure automation journey.
Which is more costly to use, Terraform or Pulumi?
When comparing the costs of Terraform and Pulumi, it’s important to consider both the upfront licensing costs and the ongoing costs of implementation. Both of these tools are available as free open-source software, but they also offer paid versions that include additional features and support. Terraform’s pricing model is based on Terraform Cloud and Enterprise, with team and governance features available at higher price points. Pulumi also offers its Pulumi Service at various price points, with team collaboration and advanced security features included in the more expensive plans. For organizations that have strict compliance requirements or large teams, the enterprise versions of both of these tools can be quite expensive, although these costs are usually small compared to the cost of the infrastructure that they manage.
Aside from licensing, the costs of implementation can include training, integration, and possible migration expenses. Teams that are already familiar with the programming languages supported by Pulumi may need less training than those who are learning both infrastructure concepts and HCL. On the other hand, organizations with existing Terraform deployments will face migration costs when switching to Pulumi, even with conversion tools to help. The most accurate cost assessment requires evaluating both direct and indirect factors in your specific organizational context.
Is it possible to transfer my current Terraform code to Pulumi?
Indeed, Pulumi offers the tf2pulumi tool, which is specifically created to transform Terraform HCL configurations into equivalent Pulumi code in your preferred language. This tool can handle most standard Terraform resources and patterns, converting them into code that is idiomatic for your target language. While the conversion process generally works well for simple configurations, complex or highly customized Terraform setups may necessitate manual modifications after conversion. The tool maintains resource names and properties, allowing for a smooth transition with minimal impact on existing infrastructure.
Which tool is better for Kubernetes?
Both tools provide strong Kubernetes support, but they do so in different ways that reflect their overall philosophies. Terraform has a Kubernetes provider that can manage most Kubernetes resources, with additional providers for specific Kubernetes distributions like EKS and GKE. Its simple declarative approach is effective for managing standard Kubernetes resources, but complex templating can become verbose in HCL. If your organization already uses Terraform for other infrastructure, its Kubernetes support allows for a consistent workflow across all resource types.
Does Terraform’s BSL license change affect my decision?
HashiCorp’s decision to switch from MPL to the Business Source License (BSL) for Terraform is a significant licensing change that needs to be taken into account. The BSL restricts certain uses of Terraform, especially by competing services that use Terraform’s code. For most end users who are deploying infrastructure for their own organizations, this change has little practical impact – you can continue using Terraform as before. However, organizations that are building commercial tools that integrate with or extend Terraform should carefully review the BSL terms to ensure they comply with the new restrictions.
Can I use both tools in the same organization?
Yes, you can use both Terraform and Pulumi in the same organization. Many organizations successfully use both tools for different teams or workloads, taking advantage of the strengths of each tool where it makes the most sense. This hybrid approach can be particularly effective during migration periods or when different teams have different requirements or preferences. The tools can interoperate through outputs and data sources, with Terraform able to reference Pulumi-managed resources (and vice versa) using appropriate state queries. While this hybrid approach adds some complexity in standardization and training, it provides flexibility to choose the right tool for each specific use case.
Companies that are considering this approach should establish clear rules about when to use each tool. This will help to avoid confusion and ensure that practices are consistent. Some companies divide the use of the tools by team. For example, the development teams may use Pulumi while the infrastructure teams use Terraform. Other companies separate the use of the tools by the type of resource or the environment. If you have good governance and communication, this practical approach can give you the benefits of both tools. It can also minimize disruption to existing workflows.
Both Terraform and Pulumi are developing at a fast pace, they are continuously improving and adding new features. The best choice for your organization will depend on your specific needs, the composition of your team, and your infrastructure objectives, rather than the technical superiority of either tool.