Key Takeaways
SecurityContext is a Kubernetes feature that configures permissions and security settings for pods and containers.
Implementing SecurityContext is critical for enforcing the principle of least privilege and enhancing cluster security.
Key configurations include setting user and group IDs, defining capabilities, and establishing read-only root filesystems.
SecurityContext works at both the pod and container level, allowing for granular security controls.
Understanding and properly configuring SecurityContext settings is essential for any Kubernetes administrator.
Unlocking the Power of Kubernetes SecurityContext
When you’re steering the ship of a Kubernetes cluster, you’re not just managing a fleet of containers; you’re also in charge of keeping the cargo—your data and applications—safe from the stormy seas of cyber threats. This is where Kubernetes SecurityContext comes into play. It’s like the lifejacket for your pods and containers, ensuring they operate under the right conditions to stay afloat even when security risks are trying to pull them under.
Defining SecurityContext
Let’s get down to brass tacks. In Kubernetes, a SecurityContext is part of your pod’s or container’s manifesto—it’s the set of directives that tell your pods how to behave in the digital world. Just like you wouldn’t give a stranger unrestricted access to your home, you shouldn’t let your containers run wild without any rules. SecurityContext helps you set these rules, and it’s all about making sure your containers play by the safety book.
Why It’s Essential for Pod and Container Security
Most importantly, SecurityContext keeps your containers in check. Without it, your pods could potentially run with more privileges than they need, and in the cybersecurity world, that’s like leaving your front door wide open with a neon ‘Welcome’ sign for hackers. By fine-tuning the SecurityContext, you ensure that each container has just enough privileges to do its job—nothing more, nothing less. This isn’t just good practice; it’s a fortress-building strategy in the land of Kubernetes.
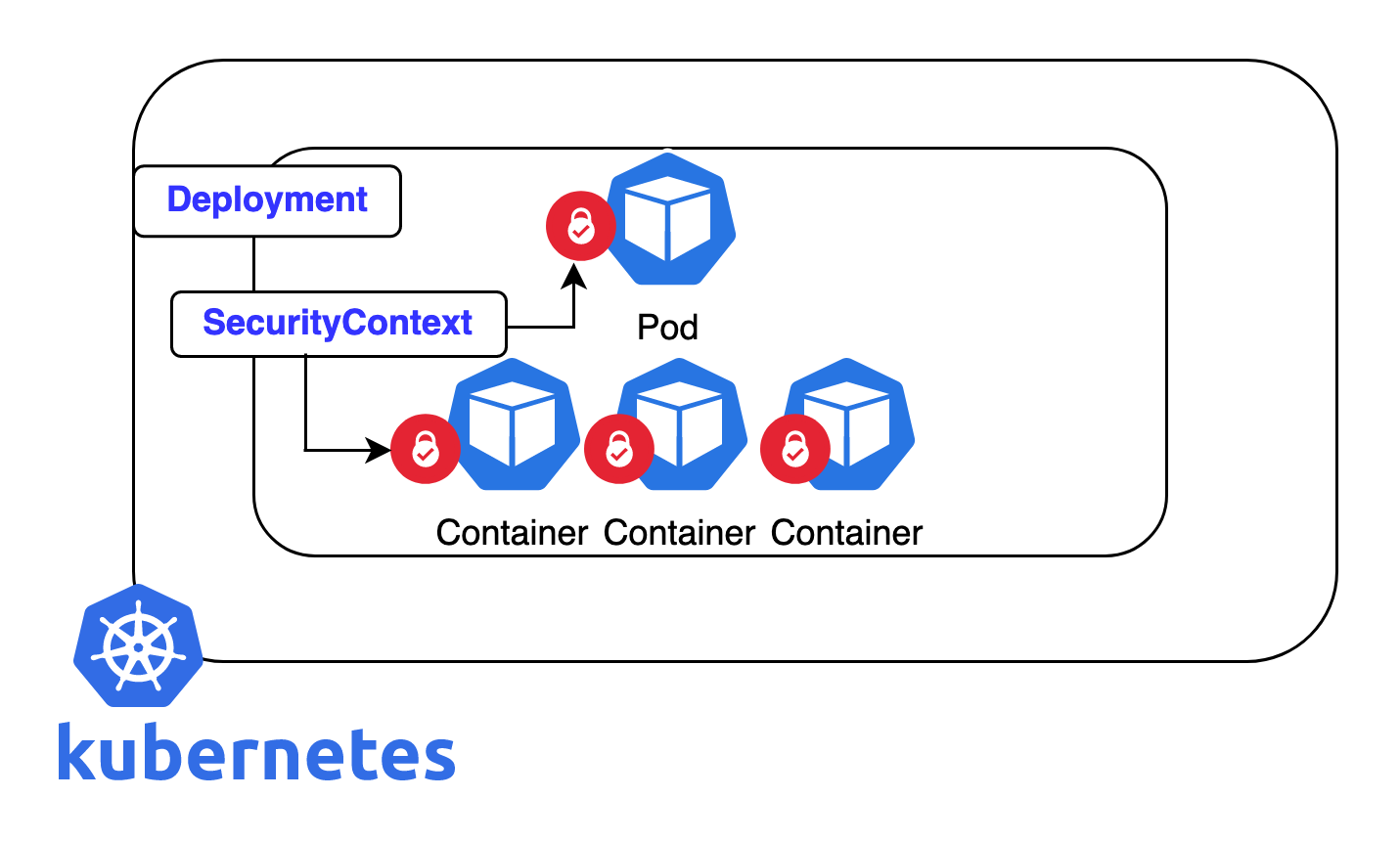
“Harden Kubernetes cluster with pod and …” from earthly.dev and used with no modifications.
Establishing Strong Security Foundations
Before we dive into the nitty-gritty of SecurityContext configurations, it’s crucial to grasp why we’re doing all this. Kubernetes clusters host a multitude of applications, and each one has different security needs. By setting up a strong SecurityContext, you’re laying down the law of the land, telling each pod and container what’s allowed and what’s off-limits. This is your first line of defense, and it’s a mighty one.
Setting the Scene: Pod and Container Isolation
Imagine your Kubernetes cluster as a high-rise apartment building. Each pod is an apartment, and each container is a room within it. Now, you wouldn’t want the plumbing in one room to cause a flood in the entire building, right? That’s why isolation is key. SecurityContext helps you isolate each container’s processes and resources from others, minimizing the blast radius if something goes awry. It’s like having watertight compartments on a ship to keep it afloat even if one part is leaking.
Practical Steps to Secure Your Kubernetes Pods
So, how do you get started with setting up a SecurityContext? Here are some simple, actionable steps:
Identify your security requirements: What does each pod and container need in terms of permissions? What should be off-limits?
Define SecurityContext in your YAML files: This is where you specify the rules for your pods and containers, like who can run them and what resources they can access.
Apply the principle of least privilege: Only give your containers the minimum permissions they need to function. This limits potential damage in case of a security breach.
Test and iterate: Security isn’t a one-and-done deal. Apply your settings, test them, and refine as needed. Your future self will thank you for this diligence.
By following these steps, you’ll be well on your way to creating a secure Kubernetes environment where your applications can thrive without the constant threat of security breaches.
User and Group Permissions in Detail
Now, let’s zoom in on user and group permissions. In the Kubernetes world, every container can have its own user ID (UID) and group ID (GID), just like every person has their own identity. By default, containers run as the root user, but that’s like giving a toddler the keys to a sports car—risky business! Instead, you want to assign specific UIDs and GIDs to your containers, so they have only the access they need.
Here’s how you set user and group permissions:
Specify the
runAsUserfield: This tells Kubernetes which UID to use when running the container processes.Use the
runAsGroupfield: This indicates the GID for the process.Implement the
fsGroupfield: This defines the GID for any files created within the container, ensuring the correct file permissions.
By tailoring these settings, you’re essentially giving each container its own identity card, outlining what it can and cannot do within your Kubernetes environment.
Understanding and Setting Linux Capabilities
Let’s talk capabilities. In Linux, capabilities are like superpowers that you can bestow upon your containers. They’re a way to break down the all-or-nothing power of the root user into more manageable, specific privileges. For example, you might want a container to be able to bind to well-known ports but not to access other users’ files.
Here’s how to wield these Kubernetes security best practices wisely:
Define
capabilitiesin your SecurityContext: Add specific capabilities your container needs and drop the ones it doesn’t.Be selective: Only grant the capabilities essential for your container’s functionality.
Regularly review: Periodically check your capabilities settings to ensure they’re still appropriate and secure.
By doing this, you’re not only minimizing risk but also ensuring that your containers have the tools they need to perform their tasks effectively.
Advanced SecurityContext Features
For those looking to go the extra mile in securing their Kubernetes containers, there are advanced features in SecurityContext that can be game-changers. These settings give you more fine-grained control over how your containers interact with the underlying system and resources.
Let’s dive into some of these advanced features:
Seccomp profiles: Define a set of allowed system calls to reduce the surface area for attacks.
SELinux labels: Leverage Security-Enhanced Linux to enforce access control policies.
AppArmor profiles: Use these Linux kernel security modules to restrict programs’ capabilities.
By incorporating these advanced settings, you’re not just locking the doors; you’re adding surveillance cameras and a top-notch alarm system to your container security setup.
Read-Only Root Filesystem: How and When to Use It
One of the advanced features you can set is making the root filesystem read-only. This is like deciding that no one can write on the walls of your house—whatever is there when you move in stays put. This feature is incredibly useful for preventing unauthorized changes or tampering with your container’s filesystem.
To set a read-only root filesystem, use the readOnlyRootFilesystem flag in your SecurityContext. It’s a simple switch, but it can have a profound impact on your container’s security. However, remember that some applications need to write to the root filesystem to function. In those cases, you can define specific volumes that the application can write to.
Controlling Privilege Escalation in Containers
Privilege escalation is like giving a mouse a cookie—once it gets a taste, it’ll want more. In containers, if a process can gain higher privileges than it started with, it could lead to a full-blown security breach. To prevent this, Kubernetes SecurityContext provides the allowPrivilegeEscalation flag.
By setting this flag to false, you’re telling Kubernetes to prevent any process within the container from gaining additional privileges beyond those it was initially granted. It’s a critical setting for maintaining a secure and stable environment.
Crafting a Robust Security Strategy
Having strong security settings is great, but they’re only as good as the strategy behind them. A robust security strategy is like a treasure map—it guides you to make the right decisions and avoid potential pitfalls.
Here’s how to craft a strategy that stands the test of time:
Assess regularly: Security isn’t static. Regularly assess your cluster’s security posture and adapt as needed.
Automate: Use tools to automate security checks and updates. This ensures consistency and helps you stay ahead of threats.
Document: Keep clear records of your security configurations and rationales. This is invaluable for troubleshooting and compliance.
With a well-thought-out strategy, you’re not just responding to threats—you’re anticipating them and staying two steps ahead.
SecurityContext Best Practices
As with any aspect of Kubernetes, there are best practices to follow when it comes to SecurityContext. These are the tried-and-true methods that keep your cluster secure:
Minimize root usage: Avoid running containers as root whenever possible.
Implement least privilege: Only grant permissions that are absolutely necessary for operation.
Use security policies: Enforce SecurityContext configurations with Pod Security Policies or their successors, like OPA/Gatekeeper.
Stick to these best practices, and you’ll build a strong, secure foundation for your Kubernetes deployments.
Integrating SecurityContext with Cluster Policies
Besides that, integrating SecurityContext with your cluster policies isn’t just smart—it’s essential. Cluster policies act as the rulebook for your entire Kubernetes environment, and SecurityContext is a key chapter in that book.
Here’s how to integrate effectively:
Define clear policies: Establish what’s allowed and what’s not within your cluster at a high level.
Align SecurityContext settings: Make sure your SecurityContext configurations adhere to these overarching policies.
Enforce consistently: Use tools like admission controllers to enforce your policies across the board, ensuring uniform security practices.
With SecurityContext and cluster policies working hand in hand, you create a cohesive, secure environment that’s resilient against threats.
Frequently Asked Questions
Now that we’ve covered the ins and outs of Kubernetes SecurityContext, you might still have some questions. Let’s address some of the most common ones to ensure you have a solid grasp of how to enhance pod and container safety in your Kubernetes environment.
What Exactly Does SecurityContext Control in Kubernetes?
SecurityContext in Kubernetes gives you the power to dictate how your pods and containers live their digital lives. It controls:
The user and group IDs under which the container processes run.
What privileges the container has, including Linux capabilities.
Whether the container’s root filesystem is read-only or writable.
Whether a process can gain more privileges than it started with.
Think of it as the personal bodyguard for your containers, setting boundaries and enforcing rules to keep them safe.
How Does SecurityContext Interact with RBAC?
Role-Based Access Control (RBAC) is like the bouncer at the club, deciding who gets in and who doesn’t. SecurityContext, on the other hand, is more like the rules inside the club—once you’re in, it tells you what you can and can’t do. While RBAC controls access to Kubernetes resources, SecurityContext controls how those resources behave once they’re being used. They work together to ensure a secure and orderly environment in your Kubernetes cluster.
Can a Container’s SecurityContext Override Pod-Level Settings?
Yes, it can. If you’ve set certain rules at the pod level but need a specific container to follow a different set of rules, you can define a SecurityContext for that container. It’s like having a general set of house rules but allowing a particular room to have its own set of guidelines. This level of granularity ensures that each container can operate with the permissions and settings it uniquely requires.
What Are the Limitations of Kubernetes SecurityContext?
While SecurityContext is powerful, it’s not all-powerful. Here are some limitations:
Not all SecurityContext settings are supported on every container runtime or operating system.
Some applications may require additional privileges, which could limit how restrictive you can be.
SecurityContext cannot prevent all types of attacks, so it should be part of a layered security approach.
Therefore, while SecurityContext is a vital tool, it’s just one part of a broader security strategy.
How to Test SecurityContext Configurations for Effectiveness?
Testing your SecurityContext settings is like running a fire drill—it ensures that in case of an actual emergency, everything works as it should. Here’s how to test your configurations:
Use automated tools: Tools like kube-bench or kubeaudit can help you check for common misconfigurations and security risks.
Simulate attacks: Employ chaos engineering practices to simulate attacks and see how your configurations hold up.
Review logs: Regularly review your container and Kubernetes system logs for any signs of security issues or unexpected behavior.
By thoroughly testing, you can trust that your SecurityContext settings will stand up to real-world challenges.
In conclusion, Kubernetes SecurityContext is a fundamental feature for securing your pods and containers. By understanding and applying the configurations we’ve discussed, you can significantly enhance the safety of your Kubernetes environment. Remember, security is an ongoing process, and it’s essential to stay informed, vigilant, and proactive. Keep refining your security strategies, and you’ll be well-equipped to navigate the ever-evolving landscape of cybersecurity threats.