Key Takeaways
Kubernetes Secrets store sensitive information like passwords, API keys, and certificates securely.
Types of sensitive data include database credentials, encryption keys, and SSL/TLS certificates.
Best practices involve encrypting secrets at rest and in transit, rotating them regularly, and monitoring access.
Various tools like HashiCorp Vault and AWS Secrets Manager can help manage Kubernetes Secrets effectively.
Proper secret management ensures enhanced security and compliance with regulatory requirements.
Overview of Kubernetes Secrets
Kubernetes Secrets are a built-in feature designed to store and manage sensitive information securely. They help ensure that confidential data, such as passwords, OAuth tokens, and SSH keys, remains protected within your Kubernetes clusters.
Storing this sensitive data in Kubernetes Secrets is crucial because it prevents accidental exposure and unauthorized access. Without proper management, these secrets could be compromised, leading to potential security breaches.
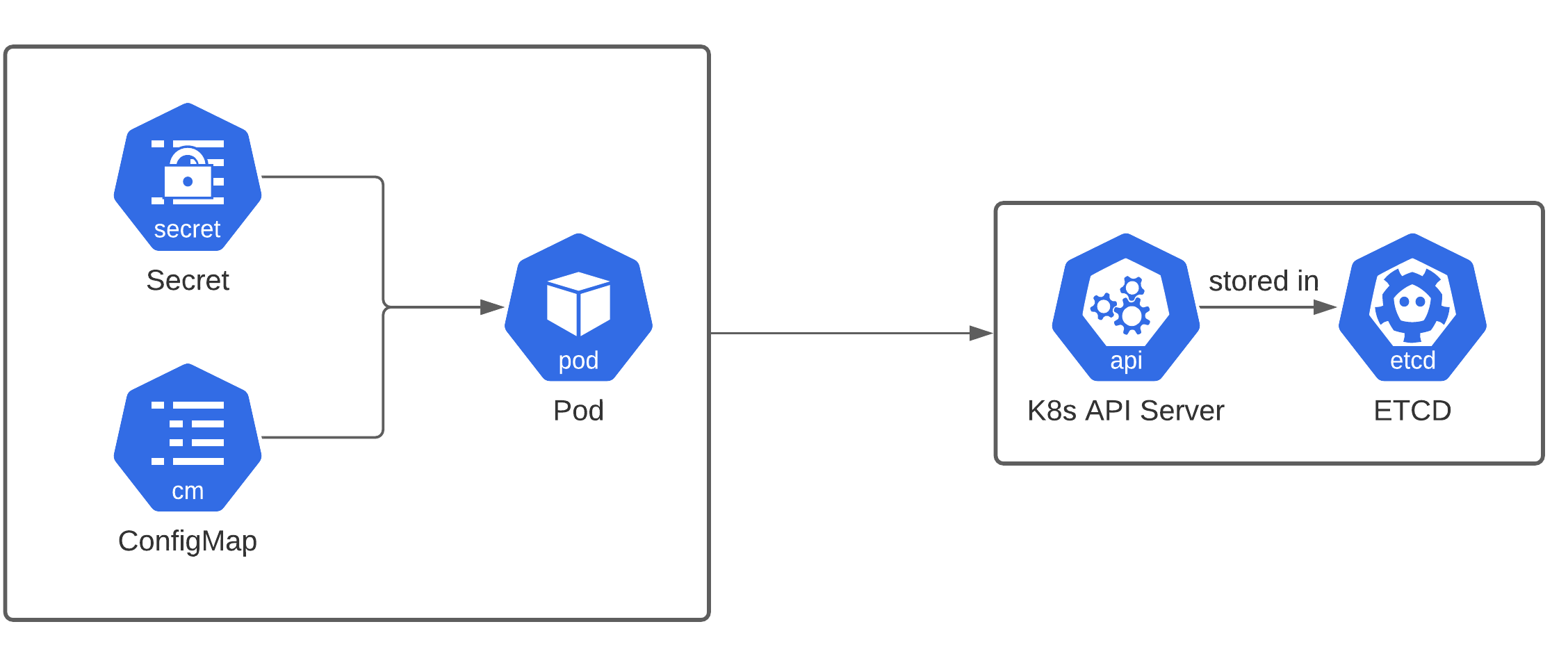
“Kubernetes Secrets Management – IN4IT …” from in4it.com and used with no modifications.
Types of Sensitive Data in Kubernetes
Kubernetes Secrets can store various types of sensitive data. Knowing what kind of information you can secure is the first step towards effective secret management.
Database Credentials
Database credentials, such as usernames and passwords, are commonly stored in Kubernetes Secrets. This ensures that applications can securely access the database without exposing sensitive information in the application code.
Encryption Keys
Encryption keys are another critical type of data that can be stored in Kubernetes Secrets. These keys are essential for encrypting and decrypting data, ensuring that sensitive information remains secure during storage and transmission.
API Tokens
API tokens are used to authenticate and authorize API requests. Storing these tokens in Kubernetes Secrets helps prevent unauthorized access to APIs, protecting your applications from potential security threats.
SSL/TLS Certificates
SSL/TLS certificates are crucial for establishing secure communication channels between clients and servers. By storing these certificates in Kubernetes Secrets, you can ensure that your applications maintain secure connections without exposing sensitive certificate data.
Configuration Files
Configuration files often contain sensitive information, such as environment-specific settings and credentials. Storing these files in Kubernetes Secrets helps keep your application’s configuration secure and manageable.
Methods for Managing Secrets in Kubernetes
Managing secrets in Kubernetes involves various methods, each with its own advantages. Understanding these methods will help you choose the best approach for your specific use case.
Using YAML Definitions
One of the most common methods for creating Kubernetes Secrets is using YAML definitions. This approach allows you to define secrets in a structured format that can be easily managed and versioned.
apiVersion: v1
kind: Secret
metadata:
name: my-secret
type: Opaque
data:
username: YWRtaW4=
password: MWYyZDFlMmU2N2Rm
Environment Variables in Pods
Another method for managing secrets is using environment variables in pods. This approach allows you to inject secrets directly into the environment variables of your containers, making them easily accessible to your applications.
Volume Mounts
Volume mounts provide another way to manage secrets in Kubernetes. By mounting secrets as files within a pod, you can ensure that sensitive data is securely stored and accessed by your applications.
Importance of Kubernetes Secret Management
Effective Kubernetes secret management is crucial for several reasons. Besides safeguarding sensitive information, it also ensures compliance with regulatory requirements and enhances overall application security. For more insights on enhancing Kubernetes productivity, consider exploring Kubernetes plugins with Krew.
Proper secret management helps you maintain control over who can access sensitive data, reducing the risk of unauthorized access and potential data breaches. By implementing best practices, you can ensure that your Kubernetes clusters remain secure and compliant with industry standards.
Importance of Kubernetes Secret Management
Effective Kubernetes secrets management is not just about securing sensitive data; it’s a fundamental aspect of maintaining a robust and secure infrastructure. By implementing proper secrets management practices, you can ensure that your applications and data remain protected from unauthorized access and potential breaches.
Safeguarding Sensitive Information
One of the primary reasons for managing Kubernetes secrets is to safeguard sensitive information. This includes passwords, API keys, and encryption keys that, if exposed, could lead to significant security vulnerabilities. By storing these secrets securely, you reduce the risk of unauthorized access and ensure that your sensitive data remains confidential.
Compliance and Regulatory Requirements
Many industries have stringent compliance and regulatory requirements regarding data protection and privacy. Properly managing Kubernetes secrets helps organizations meet these requirements by providing a framework for securely handling and controlling access to sensitive information. This not only protects your data but also ensures that your organization remains compliant with relevant laws and regulations.
For example, the General Data Protection Regulation (GDPR) requires organizations to implement appropriate technical measures to protect personal data. By managing Kubernetes secrets effectively, you can demonstrate compliance with such regulations and avoid potential fines and penalties.
Enhanced Application Security
Besides safeguarding sensitive information and ensuring compliance, effective secrets management enhances overall application security. By controlling access to secrets and regularly rotating them, you can prevent unauthorized access and reduce the risk of security breaches.
Additionally, by monitoring access and changes to secrets, you can quickly detect and respond to potential security incidents. This proactive approach helps you maintain a secure environment and protect your applications from emerging threats.
Best Practices for Kubernetes Secret Management
To effectively manage Kubernetes secrets, it’s essential to follow best practices that ensure the security and integrity of your sensitive data. Here are some key practices to consider:
Storing Secrets in a Secure Location
Always store your Kubernetes secrets in a secure location. Avoid hardcoding secrets directly into your application code or configuration files, as this can lead to accidental exposure. Instead, use Kubernetes Secrets to store and manage your sensitive data securely.
For example, you can create a secret using the Kubernetes CLI:
kubectl create secret generic my-secret --from-literal=username=admin --from-literal=password=secret
Encrypting Secrets at Rest and in Transit
Encrypting secrets both at rest and in transit is crucial for protecting your sensitive data. Kubernetes provides built-in mechanisms for encrypting secrets at rest using the EncryptionConfig feature. Additionally, you should use secure communication channels, such as TLS, to encrypt secrets in transit.
Enable encryption at rest by configuring EncryptionConfig in your Kubernetes cluster.
Use TLS to secure communication between your applications and the Kubernetes API server.
By encrypting secrets, you ensure that even if an attacker gains access to your storage or communication channels, they cannot read the sensitive data without the encryption keys.
Encrypting Secrets at Rest with EncryptionConfig
To encrypt secrets at rest, you can configure EncryptionConfig in your Kubernetes cluster. This feature allows you to specify encryption providers and key management systems for encrypting your secrets.
Here’s an example of an EncryptionConfig file:
apiVersion: apiserver.config.k8s.io/v1
kind: EncryptionConfiguration
resources:
- resources:
- secrets
providers:
- aescbc:
keys:
- name: key1
secret: c2VjcmV0a2V5MQ==
- identity: {}
By configuring EncryptionConfig, you ensure that your secrets are encrypted before being stored in etcd, providing an additional layer of security for your sensitive data.
Rotating Secrets Regularly
Regularly rotating secrets is a crucial practice for maintaining the security of your Kubernetes cluster. By changing secrets periodically, you minimize the risk of unauthorized access due to compromised credentials.
To rotate secrets, follow these steps:
Create a new secret with updated credentials.
Update your applications to use the new secret.
Delete the old secret to prevent unauthorized access.
Regular secret rotation helps ensure that even if a secret is compromised, the exposure is limited to a short period.
Monitoring Access and Changes
Monitoring access to and changes in Kubernetes secrets is essential for detecting potential security incidents. By keeping an eye on who accesses your secrets and when changes are made, you can quickly identify and respond to suspicious activities.
Consider using tools like Kubernetes Audit Logs and third-party monitoring solutions to track access and changes to your secrets. This proactive approach helps you maintain a secure environment and protect your sensitive data from unauthorized access.
Enable Kubernetes Audit Logs to track access and changes to secrets.
Use third-party monitoring solutions for enhanced visibility and alerting.
Implementing Role-Based Access Control (RBAC)
Implementing Role-Based Access Control (RBAC) is a best practice for managing access to Kubernetes secrets. RBAC allows you to define roles and permissions for users and applications, ensuring that only authorized entities can access sensitive data.
To implement RBAC, follow these steps:
Define roles and permissions for accessing secrets.
Assign roles to users and applications based on their responsibilities.
Regularly review and update roles and permissions to ensure they align with your security policies.
By implementing RBAC, you can control access to your secrets and reduce the risk of unauthorized access and potential security breaches.
Tools for Managing Kubernetes Secrets
Several tools can help you manage Kubernetes secrets effectively. These tools provide additional features and capabilities for securely storing, managing, and accessing sensitive data within your Kubernetes clusters.
Built-In Kubernetes Secrets
Kubernetes provides built-in support for managing secrets. This feature allows you to create, store, and manage secrets directly within your Kubernetes cluster, providing a secure and convenient way to handle sensitive data.
For example, you can create a secret using the Kubernetes CLI:
To securely manage sensitive data in Kubernetes, you can use the command
kubectl create secret generic my-secret --from-literal=username=admin --from-literal=password=secret.
This command creates a secret named “my-secret” with the specified username and password, which can then be used by your applications.
HashiCorp Vault
HashiCorp Vault is a popular tool for managing secrets and protecting sensitive data. Vault provides advanced features, such as dynamic secrets, secret rotation, and access control, making it an excellent choice for managing Kubernetes secrets.
By integrating Vault with Kubernetes, you can securely store and manage your secrets while leveraging Vault’s robust security features.
AWS Secrets Manager
AWS Secrets Manager is a managed service that helps you store and manage secrets securely. With Secrets Manager, you can easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle.
Integrating AWS Secrets Manager with Kubernetes allows you to leverage AWS’s security features and manage your secrets effectively within your Kubernetes clusters.
Azure Key Vault
Azure Key Vault is a cloud service that provides secure storage and management of secrets, keys, and certificates. Key Vault helps you safeguard cryptographic keys and secrets used by cloud applications and services.
By integrating Azure Key Vault with Kubernetes, you can securely manage your secrets and ensure that your sensitive data remains protected.
Google Cloud Secret Manager
Google Cloud Secret Manager is a secure and convenient way to store API keys, passwords, certificates, and other sensitive data. Secret Manager provides a central place to manage, access, and audit secrets across Google Cloud.
Integrating Google Cloud Secret Manager with Kubernetes allows you to leverage Google Cloud’s security features and manage your secrets effectively within your Kubernetes clusters.
Conclusion: Enhancing Kubernetes Security
Effective Kubernetes secret management is crucial for securing sensitive data and maintaining a robust and secure infrastructure. By following best practices, such as storing secrets in a secure location, encrypting them at rest and in transit, rotating them regularly, and monitoring access, you can ensure that your Kubernetes clusters remain secure and compliant with industry standards.
Leveraging tools like HashiCorp Vault, AWS Secrets Manager, Azure Key Vault, and Google Cloud Secret Manager can further enhance your secret management capabilities, providing additional features and security for your sensitive data.
By implementing these best practices and utilizing the right tools, you can empower your DevOps teams to manage Kubernetes secrets effectively, ensuring the security and integrity of your applications and data.
Frequently Asked Questions (FAQ)
What types of sensitive data can Kubernetes Secrets store?
Kubernetes Secrets can store various types of sensitive data, including database credentials, encryption keys, API tokens, SSL/TLS certificates, and configuration files.
How can I create and use Kubernetes Secrets?
You can create Kubernetes Secrets using YAML definitions, environment variables in pods, or volume mounts. The Kubernetes CLI provides commands for creating and managing secrets, making it easy to store and access sensitive data securely.
Why is encrypting Kubernetes Secrets important?
Encrypting Kubernetes Secrets is crucial for protecting sensitive data from unauthorized access. By encrypting secrets at rest and in transit, you ensure that even if an attacker gains access to your storage or communication channels, they cannot read the sensitive data without the encryption keys.
What are the best practices for managing Kubernetes Secrets?
Best practices for managing Kubernetes Secrets include storing secrets in a secure location, encrypting them at rest and in transit, rotating them regularly, monitoring access and changes, and implementing Role-Based Access Control (RBAC).
Built-In Kubernetes Secrets
Kubernetes provides built-in support for managing secrets. This feature allows you to create, store, and manage secrets directly within your Kubernetes cluster, providing a secure and convenient way to handle sensitive data.
For example, you can create a secret using the Kubernetes CLI:
kubectl create secret generic my-secret --from-literal=username=admin --from-literal=password=secret
This command creates a secret named “my-secret” with the specified username and password, which can then be used by your applications.
HashiCorp Vault
HashiCorp Vault is a popular tool for managing secrets and protecting sensitive data. Vault provides advanced features, such as dynamic secrets, secret rotation, and access control, making it an excellent choice for managing Kubernetes secrets.
By integrating Vault with Kubernetes, you can securely store and manage your secrets while leveraging Vault’s robust security features.
AWS Secrets Manager
AWS Secrets Manager is a managed service that helps you store and manage secrets securely. With Secrets Manager, you can easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle.
Integrating AWS Secrets Manager with Kubernetes allows you to leverage AWS’s security features and manage your secrets effectively within your Kubernetes clusters.
Azure Key Vault
Azure Key Vault is a cloud service that provides secure storage and management of secrets, keys, and certificates. Key Vault helps you safeguard cryptographic keys and secrets used by cloud applications and services.
By integrating Azure Key Vault with Kubernetes, you can securely manage your secrets and ensure that your sensitive data remains protected.
Google Cloud Secret Manager
Google Cloud Secret Manager is a secure and convenient way to store API keys, passwords, certificates, and other sensitive data. Secret Manager provides a central place to manage, access, and audit secrets across Google Cloud.
Integrating Google Cloud Secret Manager with Kubernetes allows you to leverage Google Cloud’s security features and manage your secrets effectively within your Kubernetes clusters.
Conclusion: Enhancing Kubernetes Security
Effective Kubernetes secret management is crucial for securing sensitive data and maintaining a robust and secure infrastructure. By following best practices, such as storing secrets in a secure location, encrypting them at rest and in transit, rotating them regularly, and monitoring access, you can ensure that your Kubernetes clusters remain secure and compliant with industry standards.
Leveraging tools like HashiCorp Vault, AWS Secrets Manager, Azure Key Vault, and Google Cloud Secret Manager can further enhance your secret management capabilities, providing additional features and security for your sensitive data.
By implementing these best practices and utilizing the right tools, you can empower your DevOps teams to manage Kubernetes secrets effectively, ensuring the security and integrity of your applications and data.
Frequently Asked Questions (FAQ)
To wrap things up, let’s address some common questions about Kubernetes secret management:
What types of sensitive data can Kubernetes Secrets store?
Kubernetes Secrets can store various types of sensitive data, including database credentials, encryption keys, API tokens, SSL/TLS certificates, and configuration files.
How can I create and use Kubernetes Secrets?
You can create Kubernetes Secrets using YAML definitions, environment variables in pods, or volume mounts. The Kubernetes CLI provides commands for creating and managing secrets, making it easy to store and access sensitive data securely.
Why is encrypting Kubernetes Secrets important?
Encrypting Kubernetes Secrets is crucial for protecting sensitive data from unauthorized access. By encrypting secrets at rest and in transit, you ensure that even if an attacker gains access to your storage or communication channels, they cannot read the sensitive data without the encryption keys.