Key Takeaways
- Consul offers a complete package with integrated service discovery, health checking, and multi-datacenter support, making it perfect for intricate network architectures.
- etcd shines with its simplicity and strong consistency model, acting as the backbone for Kubernetes and other distributed systems that need dependable key-value storage.
- While both tools use the Raft consensus algorithm, their architectural approaches differ significantly—Consul emphasizes service mesh capabilities while etcd focuses on core key-value storage.
- Consul provides more extensive health checking capabilities right out of the box, whereas etcd requires extra tools for comprehensive health monitoring.
- Your specific use case should guide your decision: pick Consul for complex multi-datacenter configurations with service mesh requirements, and etcd for Kubernetes environments or when simplicity is key.
The competition between Consul and etcd has been fierce in the service discovery tools landscape, with both bringing attractive features to the table for modern distributed architectures. Knowing their differences is key to building robust microservices.
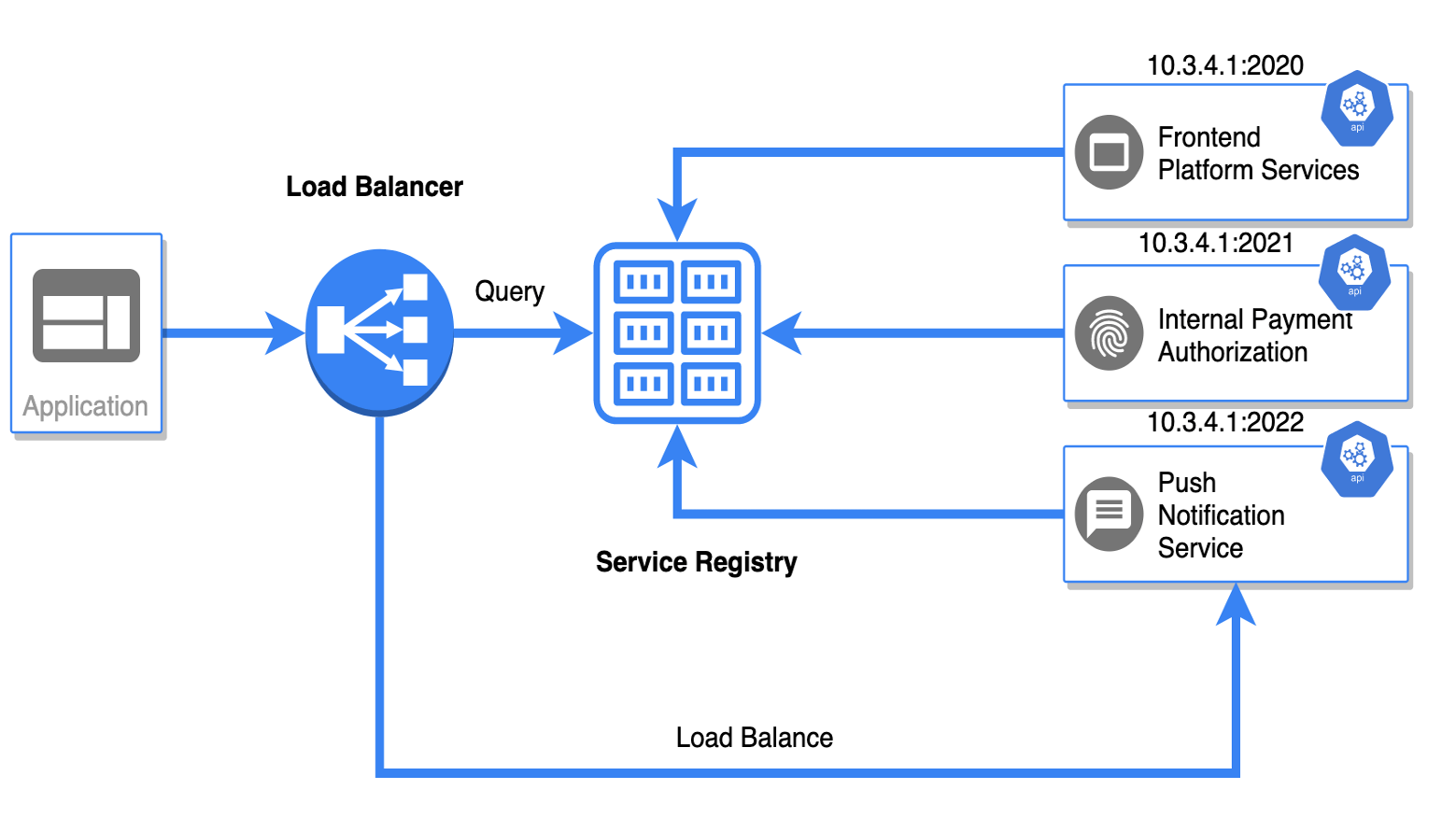
The Importance of Service Discovery in Modern Architecture
As we move towards a cloud-native environment, applications are being divided into smaller services that can be deployed independently. This change in architecture brings up an important question: how can these services locate and interact with each other in dynamic environments where IP addresses and ports are always changing?
“Service Discovery in a Nutshell …” from smartclide.eu and used with no modifications.
Service Discovery: The Heart of Microservices
Service discovery is the driving force behind today’s microservice architectures. It allows applications to find and interact with each other without the need for hard-coded network details. Without a solid service discovery system, microservices would have trouble with basic connectivity, leading to a domino effect of failures and fragile deployments. Consul and etcd have both risen to the top as solutions to this problem, but they each take a different approach and offer different features. As distributed systems continue to grow in complexity, the need for dependable service discovery mechanisms has gone from being a “nice-to-have” to being a critical piece of infrastructure.
Typical Problems When Expanding Distributed Systems
As distributed systems expand, they encounter a variety of coordination issues that service discovery tools can help resolve. Network partitions, instance failures, and deployment changes all create situations where services need to dynamically adjust to shifting topologies. The problems become exponentially worse as the scale increases—what works for dozens of services often fails with hundreds or thousands. Additionally, communicating across data centers introduces latency and reliability issues that need special attention. Both Consul and etcd offer solutions to these issues, but their methods for addressing these challenges reflect fundamentally different architectural priorities. For those planning a cloud migration strategy, understanding these tools is crucial.
When considering service discovery tools, it’s important to evaluate the features and capabilities of each option. Both Consul and etcd offer robust solutions, but they cater to slightly different needs. Consul is known for its comprehensive service discovery and configuration capabilities, while etcd is often praised for its simplicity and reliability. For those managing Kubernetes environments, understanding the differences between these tools can be crucial. If you’re planning a transition, you might also want to explore Kubernetes upgrade strategies to ensure seamless integration and operation.
Comparing the Architectures and Core Principles of Consul and etcd
While both Consul and etcd are distributed systems that aim to provide reliable coordination services, they take significantly different architectural approaches. These foundational differences are key to understanding their capabilities and the situations in which they are best used.
Consul’s Design Philosophy for Multiple Datacenters
Consul was designed from the beginning to accommodate deployments across multiple datacenters. Its structure is made up of server nodes, which keep a consistent view of the state of the cluster, and client nodes, which pass requests on to the servers. This tiered method allows Consul to scale well across large environments that are spread out geographically. The server nodes in each datacenter form their own Raft consensus group, and a gossip protocol is used to facilitate communication within and between datacenters.
Consul’s architecture is strong because it integrates service discovery, health checking, and configuration. Instead of using different tools for each of these tasks, Consul provides a single solution. This integration is also seen in Consul Connect, the service mesh offering that manages service-to-service communication with automatic TLS encryption and identity-based authorization.
Consul’s architecture is designed with human interaction in mind, thanks to its web UI and DNS interface, making it a more user-friendly option for operations teams who need to keep an eye on the service landscape. However, this user-friendly approach does come with the downside of a more complex core system.
etcd: A Kubernetes-Native Approach
etcd is a reliable distributed key-value store that is designed to be simple. Instead of focusing on having a wide range of features, etcd prioritizes consistency and reliability. It was originally developed by CoreOS, which is now part of Red Hat/IBM, and it became widely adopted as the primary datastore for Kubernetes. This solidified etcd’s place in cloud-native architectures.
Etcd’s flat peer-to-peer model is more straightforward than Consul’s multi-layer architecture. All nodes participate equally in the Raft consensus algorithm, making etcd easier to understand and possibly more resilient in some failure scenarios. However, etcd does not natively support features such as multi-datacenter replication or service health checking without additional components or customization.
Different Implementations of the Raft Consensus Algorithm
Although both Consul and etcd use the Raft consensus algorithm to ensure distributed consistency, the ways they implement it are significantly different. Consul’s implementation of Raft is adjusted for multi-datacenter environments, with enhancements for WAN gossip protocols and cross-datacenter leadership elections. On the other hand, etcd’s implementation of Raft is more focused on performance within a single cluster, prioritizing operations with low latency and close integration with the key-value store layer.
The way each tool handles network partitions and leader elections is influenced by these implementation differences. In partition scenarios, Consul tends to be more conservative, favoring consistency over availability, while etcd is optimized for quick recovery and leader elections in containerized environments. These differences become especially important in environments with unreliable networks or frequent node failures.
How Data Consistency Models Affect Your Systems
The type of consistency model that a service discovery tool uses will have a direct effect on how your system behaves during failures, network partitions, and concurrent operations. Both Consul and etcd value strong consistency, but they each implement it in different ways and with different tradeoffs.
Consul’s Robust Consistency Mechanism
Consul uses a robust consistency model that is implemented through its server nodes. These nodes form a Raft consensus group in each datacenter. All writes must pass through the consensus protocol to be committed, guaranteeing that once a write is successful, all future reads will return the updated value. For configurations that span multiple datacenters, Consul replicates data asynchronously between datacenters. This creates a model that is eventually consistent across regions while maintaining robust consistency within each datacenter.
Consul provides the option for adjustable consistency for reads, which gives operators the ability to choose between quicker responses with possibly outdated data, or guaranteed current information at the expense of contacting the leader. This adaptability allows application developers to make suitable compromises based on their specific needs for freshness versus performance.
How etcd Ensures Linearizable Consistency
etcd defaults to providing linearizable consistency, which means that all operations seem to be executed in a sequence that is consistent with the order in real-time. This strong guarantee is what makes etcd an excellent choice for storing critical cluster state in systems like Kubernetes, where consistency is of utmost importance. etcd achieves this through its implementation of Raft and its careful handling of read paths, ensuring that even nodes that are not leaders return data that is consistent.
Etcd provides serializable reads that don’t require the Raft protocol for applications that require high performance. Although these reads are quicker, they may occasionally provide outdated data. The option to choose between linearizable and serializable reads provides system designers with the flexibility to balance the needs for consistency and performance.
Tradeoffs Between Consistency and Performance
Both tools’ consistency models have performance implications. Consul’s adjustable consistency allows for optimization in specific situations, but its more complex architecture may add overhead. etcd’s linearizable reads offer robust guarantees but necessitate communication with the leader, which can become a bottleneck in read-heavy workloads. Comprehending these tradeoffs is crucial when building systems that depend on either tool, particularly as the scale expands.
Comparing Key Features
Aside from their different architectures, Consul and etcd each have unique feature sets that make them ideal for different applications. Comparing these features in detail can assist in determining which tool is best for your specific needs.
1. The Ability to Check the Health of a Service
Consul has a robust, built-in system for checking the health of a service. It can monitor services using a variety of methods, such as HTTP, TCP, running a script, and TTL (Time-To-Live). These health checks are directly integrated with Consul’s service discovery mechanism, so if a service is unhealthy, it is automatically removed from the service registry. The health check system is also highly configurable, with options to set the check interval, timeout period, and the threshold for what is considered a failure.
On the other hand, etcd does not come with integrated health checking for external services. It monitors the health of its own cluster members but depends on external tools or custom implementations to check the health of application services. This shows etcd’s emphasis on being a dependable key-value store instead of a full service discovery solution. For Kubernetes environments, this limitation is usually handled by Kubernetes’ own health checking mechanisms that work in conjunction with etcd.
2. Support for Multiple Datacenters
Consul’s unique feature is its built-in support for deployments across multiple datacenters. Clusters of Consul in different datacenters can be federated, which enables service discovery and sharing of configurations across datacenters. This federation is made possible by a WAN gossip pool that links servers across datacenters, facilitating efficient communication without the need for full mesh connectivity. Each datacenter keeps its own Raft consensus group, which minimizes the effect of cross-datacenter latency on operations related to consistency.
Etcd was not built to offer multi-datacenter replication out of the box. If you need to run etcd in multiple locations across the globe, you’ll usually need to establish distinct clusters and create your own synchronization methods. This is because etcd was primarily designed to function as a dependable datastore within a single region or cluster. If your organization needs to deploy etcd across multiple regions, you’ll need to use additional tools and custom solutions to manage cross-cluster replication and maintain data consistency.
3. Implementation of Key-Value Store
Consul and etcd both offer distributed key-value stores, but their implementation details and features vary greatly. The key-value store of Consul is designed as an additional feature to its service discovery capabilities. It offers hierarchical storage with support for CAS (Compare-And-Swap) operations, sessions, and blocking queries that allow efficient watching for changes. Although it is fully functional, Consul’s KV store is usually not as performance-optimized for high-throughput scenarios as dedicated solutions.
4. Service Mesh Integration
|
Feature |
Consul |
etcd |
|---|---|---|
|
Native Service Mesh |
Yes (Consul Connect) |
No |
|
Traffic Encryption |
Automatic mTLS |
Requires external solution |
|
Service-to-Service Authorization |
Built-in intentions system |
Requires external solution |
|
L7 Traffic Management |
Supported with proxies |
Requires external solution |
|
Integration with Istio |
Limited |
Good (via Kubernetes) |
Consul stands out with Consul Connect, its built-in service mesh solution. Connect offers automatic TLS encryption between services, identity-based authorization, and integration with proxy solutions for layer 7 traffic management. This integrated service mesh feature makes Consul especially useful for organizations that want to secure and manage communication between microservices without needing additional tools.
etcd has a fundamentally different approach, focusing solely on being a reliable datastore without built-in service mesh features. In Kubernetes environments, service mesh functionality is typically provided by dedicated solutions like Istio, Linkerd, or Cilium, which can use etcd indirectly (through Kubernetes) for their configuration storage. This separation of concerns aligns with the Unix philosophy of having tools do one thing well, but requires integration of multiple systems to achieve comprehensive service networking capabilities.
Choosing between these two often depends on whether the organization prefers an integrated or composable architecture. Consul’s all-in-one approach lessens the complexity of integration but might offer less flexibility, while etcd’s focused approach demands more integration work but gives the freedom to choose the best of the best for each component.
5. DNS Interface
Consul has a built-in DNS interface. This means that services can be found using standard DNS queries. This is especially useful for legacy applications that can’t be changed to use Consul’s HTTP API. Service instances can be found using DNS names in the format service.datacenter.consul. This makes service discovery transparent to applications. The DNS interface supports A records for IP addresses and SRV records for IP:port combinations. This provides flexibility for different service communication patterns.
On the other hand, etcd does not have a built-in DNS interface. To use DNS-based service discovery with etcd, you need to deploy extra components such as CoreDNS (with its etcd plugin) or SkyDNS. This shows that etcd is more focused on being a key-value store than a full service discovery solution. In Kubernetes settings, this issue is usually solved by Kubernetes’ own DNS service (based on CoreDNS or kube-dns) that uses etcd indirectly via the Kubernetes API server.
Having a built-in DNS interface can greatly affect how it is adopted, particularly in environments that use a combination of modern and older applications. Consul’s DNS interface often makes it easier to transition to microservices because it allows for gradual adoption without needing to make immediate changes to all applications.
Compatibility with Integration Ecosystem and API
A service discovery tool’s success is largely dependent on how well it can integrate with the broader technology ecosystem. Both Consul and etcd have robust integration options, but they each focus on different parts of the technology landscape. This reflects their unique approaches to distributed systems.
Consul has an extensive ecosystem that is centered around its robust service discovery and configuration capabilities, with integrations that cover traditional infrastructure, cloud-native environments, and monitoring tools. On the other hand, etcd has become the go-to standard for Kubernetes and has fostered a thriving ecosystem around container orchestration and cloud-native technologies.
Language Support and Client Libraries
Consul offers official client libraries for Go, Ruby, and Node.js, with community-maintained libraries available for Python, Java, PHP, and many other languages. These libraries abstract the details of communicating with Consul’s HTTP API and implement features like automatic connection pool management, caching, and retry logic. HashiCorp also maintains Consul SDK, which provides a unified interface for developers across languages, simplifying integration across polyglot environments. The broad language support makes Consul accessible to diverse development teams regardless of their technology stack.
Integration with Other Tools
Both tools have excellent integration capabilities, but they work with different ecosystems. Consul works seamlessly with other HashiCorp products like Vault for secrets management, Nomad for scheduling, and Terraform for infrastructure provisioning. It also has ready-to-use integrations with monitoring tools like Prometheus and Grafana, load balancers such as NGINX and HAProxy, and CI/CD platforms. On the other hand, etcd is closely integrated with Kubernetes and the broader CNCF ecosystem, including projects like CoreDNS, Prometheus, and various service mesh implementations. Its role as the backing store for Kubernetes has led to its widespread adoption and integration across the cloud-native landscape.
API Stability and Versioning Approaches
Consul and etcd take different approaches to API stability and versioning, which impacts long-term maintenance and upgrade strategies. Consul follows semantic versioning with clearly documented API versions and deprecation policies. Its HTTP API includes version information in the URL path, allowing multiple API versions to coexist. This approach provides stability for operators and developers while allowing the introduction of new features. etcd’s API versioning is closely tied to its gRPC interface, with major version changes typically requiring client updates. While etcd maintains backward compatibility within major versions, its evolution is more closely tied to Kubernetes release cycles, reflecting its primary use case.
How to Decide Which Tool is Right for You
Choosing between Consul and etcd will depend on your specific needs, your current technology stack, and your operational model. There’s no one-size-fits-all answer here, as each tool is better suited to different situations and environments. Knowing what each tool is good at can help you make a decision that aligns with your business needs and architectural goals.
When is Consul the Ideal Choice?
Consul is a strong contender in environments where there is a variety of application types and multiple datacenters. If your organization has a blend of legacy applications and microservices, you may find Consul’s DNS interface beneficial. It allows you to migrate gradually without the need for immediate changes to all systems. With its built-in health checking and service mesh capabilities, it is a good fit for organizations looking for a comprehensive solution for service networking. This is especially true for those organizations that do not use Kubernetes as their main orchestration platform.
Consul is particularly useful for multi-datacenter deployments. It has built-in federation capabilities that allow service discovery and configuration sharing across datacenters without needing extra tools or custom synchronization mechanisms. If your organization has strict compliance or security needs, you’ll also appreciate Consul’s built-in ACL system and Consul Connect’s service-to-service authorization features. These make it easier to put zero-trust networking principles into practice.
When etcd is the Better Choice
etcd is the preferred choice for environments that are Kubernetes-centric, where it already functions as the cluster’s backing store. Its emphasis on providing a reliable, simple key-value store with strong consistency guarantees makes it the perfect choice for storing critical configuration data and cluster state. Organizations that prefer a composable, modular architecture—adhering to the Unix philosophy of specialized tools combined to create a complete system—often prefer etcd’s specialized approach over Consul’s all-in-one solution. Additionally, for projects that require the absolute lowest latency for key-value operations, etcd’s optimized storage engine and simpler architecture can offer performance advantages.
Combined Approaches and Strategies for Transition
Many companies adopt combined approaches, using etcd for Kubernetes clusters while using Consul for broader service discovery and service mesh capabilities. This combination allows each tool to use its strengths. Transitioning between the tools requires careful planning but can be done through gradual transition strategies. For example, when transitioning from etcd to Consul, services can be registered in both systems during a transition period, with traffic gradually shifted from one to the other. On the other hand, transitioning from Consul to etcd typically involves introducing additional components like CoreDNS to replace Consul’s DNS interface and service mesh solutions like Istio to replace Consul Connect.
Common Questions
When comparing service discovery tools, architects, operators, and developers often ask the same questions. Answering these questions can help teams choose the right tool for their needs and limitations.
Is it possible to use Consul and etcd together in the same architecture?
Indeed, Consul and etcd can function effectively together in the same architecture, each managing different aspects of service coordination. It is common to use etcd as the datastore for Kubernetes clusters and Consul for service discovery across non-Kubernetes workloads and for cross-datacenter coordination. This approach takes advantage of the strengths of each tool: etcd’s close integration with Kubernetes and Consul’s wider service networking capabilities.
Companies that opt for this hybrid method usually use Kubernetes’ built-in service discovery (supported by etcd) for communication within the cluster, while Consul is used for communication between services that goes beyond the cluster or data center boundaries. Thanks to its Kubernetes integration, Consul can discover and register Kubernetes services, offering a unified service registry that covers both environments.
What are the differences in the way Consul and etcd manage network partitions?
Consul and etcd both use the Raft consensus algorithm, which gives preference to consistency over availability during network partitions (adhering to the CP aspect of the CAP theorem). However, they have different approaches to dealing with partition scenarios. The architecture of Consul, which separates server and client nodes, allows clients in a partitioned segment to continue to operate using cached data, although they cannot write until connectivity is restored. Consul also offers adjustable consistency for reads, enabling applications to choose between strong consistency and increased availability.
etcd has a more stringent approach to consistency, maintaining linearizable guarantees for all operations as standard. In the event of a network partition, only the etcd cluster members in the majority partition can proceed, while nodes in minority partitions completely reject write requests. This stringent consistency model simplifies the understanding of system behavior but may decrease availability during network problems compared to Consul’s more flexible approach.
What are the memory and CPU requirements for each tool at scale?
Both Consul and etcd have resource requirements that heavily depend on the characteristics of the workload, including the number of services, key-value pairs, read/write ratios, and update frequencies. As a general rule, Consul server nodes typically require more resources than etcd nodes due to their broader feature set. In production environments, Consul servers often need 2-8GB of RAM and 2-4 CPU cores, while Consul clients can run with minimal resources (0.5-1GB RAM and fractional CPU cores).
etcd is less demanding in terms of resources, usually requiring 2-4GB of RAM and 2 CPU cores for production deployments. The resources it uses are mainly determined by the size of the data stored and the rate of requests, with memory being especially important for performance. The more straightforward architecture of etcd means it has a smaller resource footprint, making it a good fit for environments where resources are limited.
Both tools are greatly improved by fast storage, and solid-state drives (SSDs) are highly recommended for production deployments. The performance impact of disk I/O is especially significant for etcd, which relies heavily on storage performance for its write-ahead log and snapshot mechanisms.
- For Consul: Plan for 2-8GB RAM and 2-4 CPU cores per server node, with increased memory requirements as service count grows
- For etcd: Allocate 2-4GB RAM and 2 CPU cores per node, scaling based on data size and operation rate
- Both systems: SSD storage is essential for production workloads
- Network latency: Both tools are sensitive to inter-node latency, with sub-millisecond latency ideal for optimal performance
- Monitoring: Implement comprehensive monitoring for both tools to detect resource constraints before they impact performance
Is it possible to migrate from one tool to the other without downtime?
Zero-downtime migration between Consul and etcd is challenging but achievable with careful planning and execution. The most effective approach involves running both systems in parallel during a transition period, with services gradually shifted from one to the other. For migrating from Consul to etcd, services can continue using Consul for discovery while incrementally adopting etcd for new configuration data. External proxy layers or service meshes can be configured to read from both systems during the transition, routing traffic based on the migration state.
When you switch from etcd to Consul, you usually use Consul’s API together with your current etcd integrations. You also need a way to sync data between the two systems while you’re moving. You should be ready to do a lot of testing in staging environments before you try to move to production. The specific problems you’ll run into depend on how much you’re using each tool in your current systems and workflows.
What are the differences between cloud providers’ managed services and self-hosted deployments for these tools?
Many of the major cloud providers have managed services that include features from both tools. AWS App Mesh and Cloud Map offer service discovery and mesh features that are similar to Consul. On the other hand, Google Cloud’s GKE and Azure’s AKS have managed etcd as part of their Kubernetes services. These managed services can lower operational overhead, but they usually offer less flexibility than self-hosted deployments.
When you deploy your own infrastructure, you have complete control over configuration, version selection, and integration options. However, this requires a significant amount of operational expertise. You need to weigh the convenience of managed offerings against the flexibility of deploying your own infrastructure based on your specific needs and operational capabilities.
In comparing Consul and etcd, it’s important to consider not only their technical features but also how well they fit with your company’s operational model and future technology plans. Both tools have demonstrated their reliability and scalability in production settings, but they shine in different situations.
If your organization is adopting a microservices architecture with a variety of applications and multiple datacenters, you’ll likely find that Consul’s extensive feature set provides the most straightforward route to successful service networking. On the other hand, if you’re developing around Kubernetes and containerized workloads, you may find that etcd’s simplicity and close integration with the Kubernetes ecosystem are more beneficial. If you’re finding it hard to know which is best for your current setup, then reach out to one of our experts at SlickFinch for a free consultation.




