Main Points
- AWS, Azure, and GCP all have strong HIPAA compliance frameworks, but each has unique benefits depending on your organization’s specific requirements and current technology ecosystem
- A signed Business Associate Agreement (BAA) is required for HIPAA compliance, but providers differ in which services are included and how the BAA is executed
- GCP has the most straightforward security configurations by default, while AWS offers the most extensive range of HIPAA-eligible services for complex healthcare workloads
- Azure has better integration with Microsoft 365 applications, making compliance easier for organizations that are already using the Microsoft ecosystem
- HIPAAVault assists healthcare organizations in navigating the complexities of HIPAA compliance on all major cloud platforms with specialized evaluation tools and ongoing monitoring
Basic HIPAA Cloud Compliance for Healthcare Organizations
The healthcare sector’s transition to cloud computing has transformed patient care but has also brought about complicated compliance issues. Compliance is not optional when dealing with Protected Health Information (PHI)—it’s necessary. Choosing the right cloud provider from AWS, Azure, and GCP requires understanding how each platform meets HIPAA requirements and supports your organization’s security needs.
Healthcare organizations can greatly benefit from the scalability and cost-efficiency offered by cloud infrastructure. However, this flexibility needs to be complemented with stringent security measures. The leading cloud providers have made significant investments in compliance frameworks, but it is still up to you to ensure they are properly implemented. Recent research shows that more than 70% of HIPAA violations involving cloud services are due to misconfigurations rather than deficiencies on the part of the provider.
The stakes are high when it comes to HIPAA compliance, with fines up to $1.5 million per violation category each year. It’s not just about protecting patient privacy, it’s about staying in business. The team at SlickFinch has extensive HIPAA architecture experience to guide healthcare organizations through these hurdles on all the major cloud platforms.
HIPAA Requirements for Protected Health Information (PHI)
HIPAA’s Security Rule defines three categories of safeguards that have a direct impact on cloud implementation: administrative, physical, and technical. Cloud environments must have access controls in place to limit access to PHI to authorized personnel, transmission security to ensure that data is encrypted when it is transferred, and integrity controls to ensure that PHI is not improperly altered or destroyed.
It is a requirement that covered entities and business associates keep detailed audit logs that document who accessed PHI and at what time. These logs must be unchangeable and kept for a minimum of six years. Each cloud provider has a different approach to implementing this requirement, with varying degrees of default configuration versus manual setup.
HIPAA’s most crucial requirement is that PHI must be encrypted, whether it’s in transit or at rest. All major cloud providers do support encryption, but the methods of implementation, the approaches to key management, and the default settings can vary greatly. These are details that could make a huge difference to whether you’re compliant or not.
Understanding the Shared Responsibility Model
When it comes to HIPAA compliance in the cloud, it’s a team effort between you and your provider. The provider takes care of the infrastructure security, while you focus on safeguarding your data and applications. This usually means that the provider is in charge of physical security, setting up the hypervisor, and managing the network infrastructure. On the other hand, your organization needs to handle data classification, manage access, implement encryption, and monitor the system.
The division of tasks differs among providers. AWS provides a wide range of configuration options, but requires more security knowledge. Azure offers more pre-set HIPAA-ready templates, while GCP has many security controls already in place. It’s important to understand these subtleties when deciding which provider is the best fit for your team’s abilities.
Understanding Business Associate Agreements (BAAs) and Their Significance
A Business Associate Agreement (BAA) is a crucial legal document required for any HIPAA-compliant cloud deployment. This agreement outlines the responsibilities of the provider in protecting PHI and sets the protocols for breach notifications. If a BAA is not signed, storing PHI on any cloud platform is a clear violation of HIPAA.
Each provider has a unique way of implementing the BAA. AWS requires the BAA to be activated first before storing PHI, Microsoft automatically applies the BAA to Azure, and Google Cloud requires a separate BAA request through its security and compliance console. What’s more, each provider differs in which services are covered under their BAAs. This is a crucial difference we’ll explore for each provider.
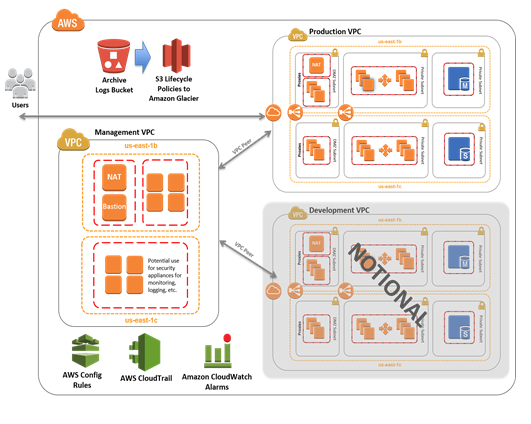
HIPAA Compliance Capabilities of AWS
Amazon Web Services is the frontrunner in terms of HIPAA-eligible services, boasting over 130 services that can manage PHI when set up correctly. With this extensive range, AWS is a prime choice for intricate healthcare workloads that utilize sophisticated services such as machine learning for medical imaging or real-time analytics for patient monitoring.
AWS healthcare clients are provided with comprehensive compliance documentation, such as the AWS HIPAA Compliance Framework and guidelines for implementing specific services. The AWS Shared Responsibility Model is particularly well-documented, offering clear instructions on which security controls are the responsibility of AWS and which are the responsibility of the client.
“Expedite a HIPAA-Compliant AWS Cloud …” from aws.amazon.com and used with no modifications.
Main Security Features for Protecting PHI
AWS shines in the area of detailed security controls with its Identity and Access Management (IAM) system. This system allows for the definition of permissions that align with the HIPAA principle of least privilege. AWS CloudTrail provides audit logging that is detailed enough to meet the accountability requirements of HIPAA, while AWS Config allows for continuous monitoring of compliance. AWS Key Management Service (KMS) provides centralized control over encryption keys and allows for either AWS-managed or customer-managed keys, which meets the encryption requirements of HIPAA in both letter and spirit.
AWS BAA Coverage and Service Limitations
AWS provides a wide range of HIPAA-eligible services, but their BAA does not cover everything. Notable exclusions include Amazon Chime (unless enterprise support is purchased), certain AWS Marketplace offerings, and some beta or preview services. Healthcare organizations must verify BAA coverage for each service they intend to use and implement compensating controls when using non-covered services alongside PHI workflows.
Tools and Documentation for Compliance
AWS offers robust tools to help maintain ongoing HIPAA compliance. This includes the AWS Security Hub, which centralizes compliance monitoring, and the AWS Audit Manager, which automates the collection of evidence for audits. The AWS Compliance Center provides documents, reference architectures, and white papers with guidance specific to healthcare. These resources can greatly shorten the learning curve for organizations that are new to cloud compliance.
Pros and Cons for Healthcare Providers
AWS’s main advantage for healthcare is its long history and wide range of services, providing solutions for almost any healthcare task while keeping compliance. Its marketplace has many HIPAA-ready partner solutions that speed up the deployment of electronic health records, telehealth platforms, and medical research environments. However, AWS’s flexibility is also its weakness—it’s often complex and organizations usually need specialized knowledge to correctly configure and maintain HIPAA compliance, especially for advanced services or multi-account architectures.
While the AWS pricing model may be beneficial for variable workloads due to its pay-as-you-go structure, it can be less predictable than reserved capacity models. Healthcare organizations often undervalue the continuous operational costs of maintaining compliance across multiple AWS services, especially when it comes to logging and monitoring on a large scale.
Cost Factors for HIPAA Workloads
There are additional costs associated with HIPAA compliance on AWS beyond the standard usage fees. The thorough logging provided by CloudTrail and CloudWatch can result in significant data storage costs, particularly if logs need to be retained for the full six years required by HIPAA. Encryption key management through AWS KMS also comes with a monthly fee as well as per-use charges. Furthermore, maintaining separate environments for development, testing, and production (which is a best practice for compliance) can multiply infrastructure costs.
- Security enhancements like dedicated instances or VPC endpoints can add an additional 10-30% to your basic infrastructure expenses
- Expect to pay anywhere from $0.50-$3 per GB for enhanced monitoring and log aggregation, which can add up quickly for data-heavy applications
- Meeting HIPAA requirements with your backup and disaster recovery configurations can potentially double your storage costs
- Using advanced security services such as AWS Shield, GuardDuty, and Macie can add an additional $1-$4 per resource each month
AWS offers healthcare-specific cost optimization guidance and Savings Plans for predictable workloads to help organizations manage these costs. The AWS Well-Architected Framework also includes a cost optimization pillar that specifically addresses expenses related to compliance.
HIPAA Compliance Framework for Microsoft Azure
Microsoft Azure sets itself up as a complete compliance solution for healthcare organizations, especially for those already using the Microsoft ecosystem. Azure’s integration with Microsoft 365, Power Platform, and Dynamics creates a unified compliance strategy that simplifies management across all data touchpoints. Unlike its competitors, Microsoft includes HIPAA coverage in its standard Enterprise agreements by default, making the legal onboarding process more straightforward.
Microsoft Azure’s compliance framework is built around Azure Policy and Azure Security Center, which provide continuous compliance monitoring against HIPAA benchmarks. Microsoft’s long history with enterprise healthcare customers is evident in their comprehensive implementation guides and compliance blueprints specifically designed for covered entities and business associates.
Compliance Features Included
Azure provides a number of built-in features that are fully compatible with HIPAA’s needs. Azure Information Protection allows for detailed data classification and labeling that extends protection beyond the cloud to endpoint devices. Azure Active Directory offers strong identity management with conditional access policies that limit PHI access based on user location, device status, and risk profiles. For healthcare organizations worried about insider threats, Azure Sentinel provides advanced security analytics that identify unusual behavior patterns that may suggest unauthorized PHI access.
What Azure’s BAA Covers and Doesn’t Cover
Azure’s BAA from Microsoft includes all the main services like storage, networking, compute, and databases. It also includes some platform services like the Azure Healthcare APIs and Azure API for FHIR. But there are some services that aren’t included in the BAA. Some examples of these are some services that are still in preview, some consumer-oriented services, and offerings from the community marketplace. Microsoft keeps a list of all the services included in the BAA in their Trust Center. They update this list often, especially when services move from being in preview to being generally available.
Microsoft, unlike AWS, which requires explicit BAA activation, automatically provides BAA coverage to enterprise customers through their Online Services Terms. While this strategy reduces administrative overhead, it necessitates vigilance to ensure that all deployed services are covered under the agreement. For more insights on cloud providers, you can read about the cloud infrastructure provider market share analysis.
|
Azure Service Category |
HIPAA BAA Coverage |
Notable Exceptions |
|---|---|---|
|
Compute (VMs, App Service) |
Fully covered |
None |
|
Storage & Databases |
Fully covered |
None |
|
Analytics & AI |
Mostly covered |
Some preview features |
|
Healthcare-specific |
Fully covered |
None |
|
Developer Tools |
Partially covered |
Community extensions |
Integration with Microsoft 365 for Healthcare
The greatest competitive edge for Azure is its smooth integration with Microsoft 365. This creates a uniform compliance environment across cloud infrastructure, productivity tools, and communication platforms. Microsoft Teams for Healthcare includes HIPAA-compliant virtual visits, care coordination, and secure messaging. All of these are managed under the same compliance framework as Azure workloads. This integration also extends to Microsoft Cloud for Healthcare, which offers industry-specific templates and workflows. These maintain compliance while speeding up deployment of common healthcare scenarios.
Companies that use Azure and Microsoft 365 together enjoy the advantage of unified audit logs. These logs offer total transparency across all the places patient data is used, from the first collection in healthcare apps to storage in databases and sharing through collaboration tools. This complete transparency greatly cuts down on blind spots that might result in compliance violations.
Tools for Managing Compliance
Azure’s Compliance Manager is a standout feature, offering a comprehensive dashboard that calculates compliance scores and suggests specific actions for improving HIPAA compliance. The tool uses detailed assessment templates to map Azure’s controls to HIPAA requirements, and it generates documentation that can be shared directly with auditors. Azure’s Policy feature automatically enforces compliance guidelines, which can help prevent common configuration errors, like deploying unencrypted storage accounts or virtual machines without the right network isolation.
Azure Arc extends compliance capabilities to on-premises infrastructure and even other clouds, creating consistent governance regardless of where PHI resides, for organizations maintaining hybrid environments. This flexibility is particularly valuable for healthcare organizations with legacy systems that cannot be fully migrated to the cloud.
Price Structure for HIPAA-Compliant Implementation
When it comes to the cost of implementing HIPAA-compliant workloads, Azure’s pricing model is typically higher than AWS’s base price. However, Azure offers more predictability through its reserved instances and comprehensive licensing packages. Companies can take advantage of Microsoft’s unified licensing approach, which includes compliance features in standard enterprise agreements instead of treating them as premium add-ons.
The Cloud for Healthcare package from Microsoft offers compliance capabilities that are specifically designed for the healthcare industry, and it does so at predictable prices. This helps to lower the so-called “compliance tax” that often comes with healthcare workloads. However, smaller organizations may find that Azure’s focus on enterprise is less cost-effective for simple use cases when compared to the more granular pay-as-you-go models that are offered by competitors.
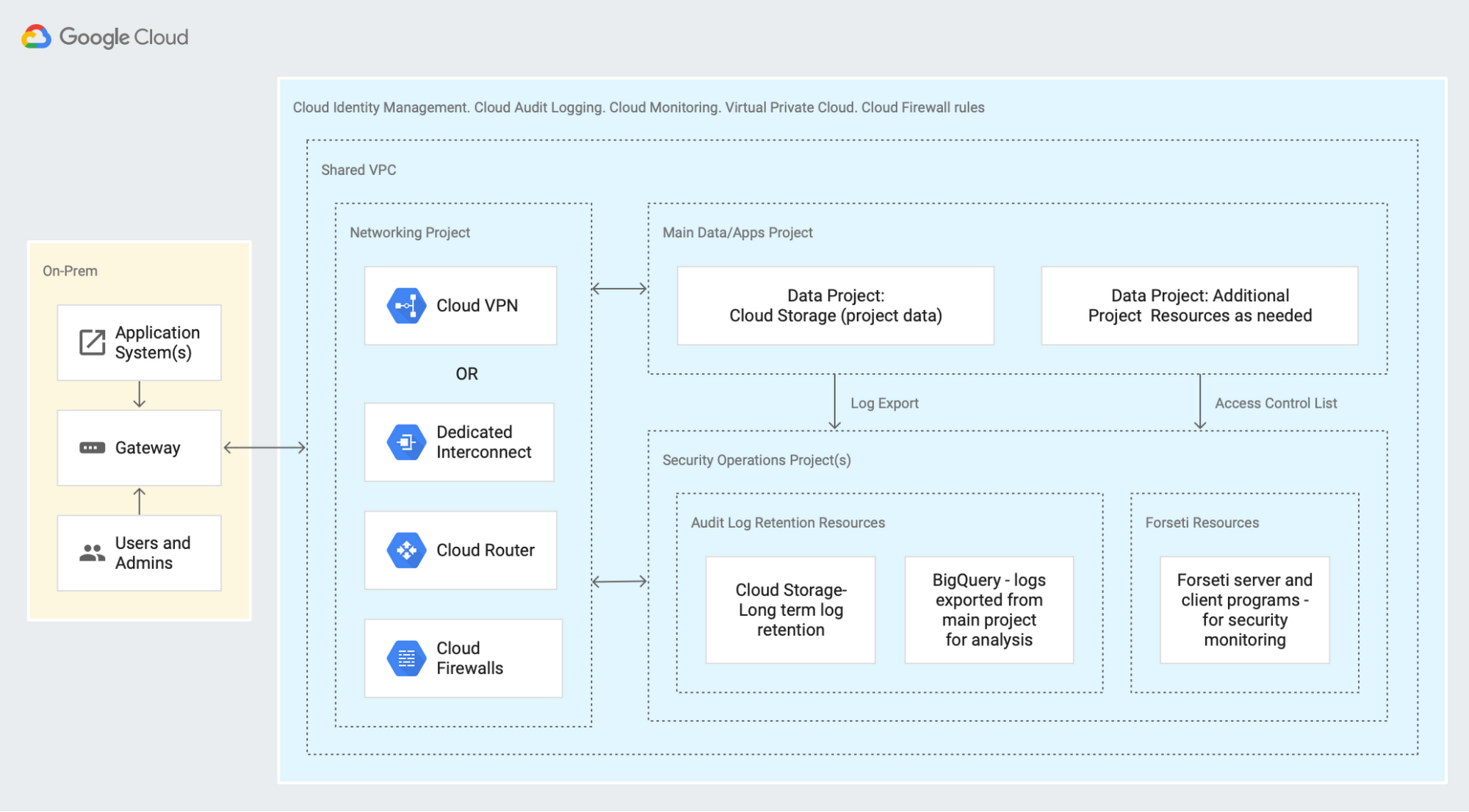
What Google Cloud Platform (GCP) offers in terms of HIPAA Compliance
Google Cloud Platform provides the simplest approach to HIPAA compliance, concentrating on ease of use and default security principles. GCP’s compliance framework highlights automated protections that lower the chance of human mistakes, which are the primary source of HIPAA breaches. For healthcare firms with few dedicated security staff, GCP’s method reduces the amount of specialized knowledge needed to keep a compliant setting. For a comprehensive comparison of Azure vs Google Cloud, you can explore the cost analysis and migration strategies.
Google’s expertise in securing large-scale consumer platforms results in strong safeguards for healthcare workloads, particularly in the areas of machine learning security and data analytics compliance. Their dedication to healthcare is evidenced by their purpose-built offerings such as the Cloud Healthcare API and collaborations with major healthcare systems.
“Healthcare data management systems tips …” from cloud.google.com and used with no modifications.
Security and Encryption Capabilities
What sets GCP’s security model apart is that it automatically encrypts all data at rest and in transit, without any need for customer configuration. Google’s proprietary cryptographic libraries and hardened infrastructure have been developed from decades of experience in protecting consumer data on an unprecedented scale. Unlike competitors where encryption may require explicit setup, GCP automatically secures PHI with AES-256 encryption, which is managed through Cloud Key Management Service. This service supports both Google-managed and customer-managed encryption keys, allowing it to meet a range of compliance requirements.
What’s Covered and What’s Not in GCP’s BAA
The Business Associate Agreement from Google Cloud includes core infrastructure services such as Compute Engine, Cloud Storage, and BigQuery, as well as services specifically for healthcare. You have to specifically request the BAA through the Google Cloud console; it isn’t automatically included in the standard terms. Once you activate it, it applies to all projects within the organization you specify.
GCP has tighter restrictions on what services are eligible for HIPAA compared to AWS, focusing on services with specific use cases in healthcare rather than trying to cover their entire portfolio. This approach provides clarity but may limit options for specialized healthcare applications that require niche cloud services.
Healthcare API and Other Healthcare-Related Features
Google Cloud’s Healthcare API is its most significant healthcare-related product, offering a managed solution for storing and accessing healthcare data in FHIR, HL7v2, and DICOM formats. This specialized service automatically addresses many HIPAA compliance requirements, including appropriate access controls, audit logging, and encryption specifically designed for healthcare data formats. The API integrates seamlessly with BigQuery for analytics and AI Platform for machine learning, creating compliant pathways for advanced healthcare applications such as clinical decision support and population health management.
Google has invested in healthcare-specific services, including Apigee Healthcare APIx. This service allows for secure interoperability between healthcare systems while also ensuring compliance. For research purposes, Google Genomics offers a specialized infrastructure for processing genomic data within environments that are HIPAA-compliant. This addresses the unique challenges of managing both protected health information (PHI) and genetic information under the necessary safeguards.
Tools for Monitoring and Auditing
Google Cloud Platform’s Cloud Audit Logs have the ability to automatically record administrative activities, data access, and system events without the need for extensive configuration. These unchangeable logs are kept for the appropriate amount of time according to HIPAA and include the necessary details for compliance reporting, such as user identity, timestamp, and action details. Google Cloud Security Command Center offers continuous security monitoring that can identify misconfigurations, suspicious access patterns, and potential vulnerabilities across all GCP resources that contain Protected Health Information.
For those organizations that need a more advanced level of monitoring, Google’s Operations suite (formerly known as Stackdriver) offers advanced log analysis and alerting capabilities that can identify possible compliance issues in real-time. The platform’s machine learning capabilities can spot unusual access patterns that may suggest inappropriate PHI exposure, offering an extra layer of protection beyond the standard rule-based monitoring.
AWS vs Azure vs GCP: A Direct Comparison
The top three cloud providers, AWS, Azure, and GCP, all have their unique strengths when it comes to HIPAA compliance. While they all meet the basic HIPAA requirements, their methods of implementation, default security measures, and special features can make one more suitable than the others depending on your organization’s specific needs.
Default Configurations and Security Controls
When it comes to security-by-default configurations, Google Cloud Platform is ahead of the game. It provides robust baseline protections that don’t need a lot of customer configuration. This strategy greatly minimizes the chances of misconfiguration errors that often result in HIPAA breaches. GCP’s VPC Service Controls set up secure boundaries around sensitive data resources, preventing data leakage while still preserving usability.
With Azure, you get a balanced approach. The Azure Security Center offers security recommendations and compliance monitoring. However, many controls require explicit activation. The platform is integrated with Microsoft Defender for Cloud, which offers threat protection capabilities specifically designed for healthcare environments. It also has predefined security policies that are aligned with HIPAA requirements.
Although AWS provides the most flexible security model, it requires the most configuration expertise. This approach allows for highly customized security implementations, but it also introduces a greater risk of misconfiguration. AWS Control Tower can help reduce this risk by implementing guardrails across multi-account environments, but it requires additional setup compared to the more automated approaches of its competitors.
Reviewing and Monitoring Features
Each of the three providers has HIPAA-compliant review logs, but they each have a unique approach to retention, searchability, and integration. Azure’s unified review logs provide the smoothest experience for organizations that use Microsoft’s broader ecosystem, as they capture activities across infrastructure, applications, and productivity tools in one interface. The platform’s integration with Sentinel provides AI-powered analysis of these logs to identify potential security incidents that affect PHI.
While AWS CloudTrail offers impressively in-depth logs, it does require some extra setup to pull them together across services and accounts. To properly analyze these spread-out logs, companies often have to use additional solutions like Amazon OpenSearch or other SIEM tools. AWS’ logging capabilities are second to none in terms of depth, but you’ll have to put in a bit more work to get the most out of them.
GCP’s Cloud Audit Logs offer a balance between easy setup and robust built-in analysis capabilities. The logging function is designed to capture only the information needed for HIPAA compliance without overloading storage or analysis resources. Google’s BigQuery integration allows for advanced compliance reporting against these logs with little extra setup.
Options for Data Encryption
Data encryption is one of the most crucial technical safeguards for HIPAA compliance, and each provider has a unique approach. GCP provides encryption by default for all data, eliminating the risk of unintentionally storing PHI without protection. Their Customer-Managed Encryption Keys (CMEK) and Cloud External Key Manager (Cloud EKM) options offer regulatory-compliant control over encryption while keeping it user-friendly.
When it comes to encryption options, AWS provides the most variety with AWS KMS and CloudHSM. These options range from basic AWS-managed keys to complex customer-managed hardware security modules. However, this flexibility does come with increased complexity. Different AWS services implement encryption in different ways, each of which must be configured separately.
Azure’s strategy is built around Azure Key Vault, a centralized key management system that integrates seamlessly with other Azure services. The platform includes built-in encryption for storage accounts and databases, which can be easily configured. Azure’s Bring Your Own Key (BYOK) and Hold Your Own Key (HYOK) models meet even the most stringent regulatory interpretations of encryption requirements.
Notification Process for Breaches
When a breach occurs, HIPAA mandates that business associates inform the entities they cover. The way this requirement is handled varies among cloud providers in their BAAs. Microsoft, for instance, offers the most thorough terms for notifying about breaches. They promise to alert customers within 72 hours of a confirmed PHI breach. Their notification includes comprehensive details about the data affected and suggestions for how the customer should respond.
The breach notification process of AWS adheres to regulatory minimums, though their standard BAA lacks specific timeframes. They pledge to notify “without unreasonable delay,” but the exact interpretation of this timeline can fluctuate. Organizations with specific notification requirements may have to negotiate custom BAA terms.
Google Cloud finds a sweet spot, offering explicit notification promises while keeping their investigation process adaptable. Their security team’s proactive breach detection skills are the best in the business, often spotting potential problems before they affect customer data. However, it’s essential to thoroughly examine their standard BAA terms to make sure they match your organization’s needs.
Availability of Services in Different Regions
The availability of services in different regions is a significant factor for healthcare organizations that have to comply with geographic regulations or have disaster recovery needs. AWS has the most comprehensive coverage globally, which is perfect for multinational healthcare organizations that need to keep PHI in certain jurisdictions. The consistent availability of their services in different regions ensures that architectures that comply with HIPAA can be deployed globally with little variation.
Azure has a strong regional presence, especially in government cloud regions that meet regulatory requirements beyond HIPAA. Azure Government offers a specialized environment for healthcare organizations that work with federal agencies or handle sensitive health information.
While GCP has fewer regions in total, it makes sure that services specific to healthcare are available in the main healthcare markets. Their regional strategy is more about depth than width, offering strong compliance certifications and specialized healthcare capabilities in existing regions instead of quick geographical growth.
Approaches to HIPAA Compliance Implementation
No matter which cloud provider you opt for, effective HIPAA compliance demands a systematic implementation method that takes into account both technical controls and organizational processes. An all-encompassing approach should synchronize cloud configurations with your current compliance framework while using provider-specific tools to optimize security and reduce administrative overhead.
1. Framework for Assessing Risk
Start with a comprehensive risk assessment that determines where PHI will be located in your cloud environment and assesses possible vulnerabilities. Each cloud provider has assessment tools that can speed up this process: AWS Security Hub, Azure Security Center, and GCP Security Command Center. These tools should be set up to specifically identify security gaps relevant to HIPAA instead of using general-purpose security benchmarks.
Record your risk assessment methods and results for audit purposes and to set your initial security stance. This assessment should be updated whenever significant changes are made to your cloud architecture or when new services are deployed that interact with PHI.
2. Implementing Access Control
Use the principle of least privilege to implement access control across all resources containing PHI using the identity and access management tools specific to each provider. AWS IAM, Azure Active Directory, and GCP IAM each offer role-based access controls that can be finely tuned to job functions. Set up access boundaries to limit the scope of credentials, even in the event of a compromise, such as AWS Permission Boundaries, Azure Custom Roles, or GCP Access Boundaries.
Ensure that all PHI access is protected by robust authentication requirements. This includes multi-factor authentication and conditional access policies that take into account factors such as device, location, and risk. It may be worthwhile to consider implementing just-in-time access for administrative functions instead of maintaining standing privileges.
3. Setting Up Encryption
Make sure you have complete encryption for PHI that is both in transit and at rest across all provider services. Set up TLS 1.2 or higher for all external connections and service-to-service communications within your environment. For data at rest, set up the right key management practices based on your risk assessment: provider-managed keys for standard scenarios, customer-managed keys for higher security requirements, or customer-supplied keys for the most strict control environments.
Include your encryption architecture in your compliance evidence, with key rotation policies, key management access controls, and any exceptions with compensating controls. Keep in mind that encryption is directly addressed in the HIPAA Security Rule and is one of the most scrutinized areas during compliance assessments.
4. Establishing Audit Controls
Set up thorough audit logs to monitor all PHI access, including successful and unsuccessful login attempts, changes to data, and administrative activities. Implement suitable log retention policies that keep records for a minimum of six years to meet HIPAA standards. Set up automated alerts for any suspicious activities that could suggest unauthorized access attempts or possible data breaches.
Set up log integrity controls that block changes to audit records by using unchangeable storage options such as AWS CloudTrail with S3 Object Lock, Azure Immutable Blob Storage, or GCP Cloud Audit Logs with retention policies. Implement frequent log review procedures that can spot patterns of unauthorized access or possible security vulnerabilities.
5. Planning for Disaster Recovery
Create and record disaster recovery protocols that guarantee the availability and integrity of PHI in the event of service interruptions. Put in place suitable backup strategies that include encryption and access controls that are equivalent to those in your production environment. Regularly test recovery protocols to confirm their efficacy and adjust them based on the results.
For crucial healthcare applications, think about employing multi-region architectures, and use disaster recovery services specific to each provider, such as AWS Backup, Azure Site Recovery, or GCP Backup and DR Service. Make sure to record recovery time objectives (RTOs) and recovery point objectives (RPOs) for systems that contain PHI, and ensure that these align with the business continuity requirements of your organization.
Choosing Your Cloud Provider
When AWS is the Best Choice
AWS is a great choice for healthcare organizations that have a lot of different tasks to manage and need a wide range of services. If your organization has a lot of technical know-how and a dedicated team for cloud security, you can take advantage of AWS’s flexibility to create a HIPAA-compliant system that’s tailored to your needs. AWS is also a great choice if you need to work with a lot of different healthcare applications from third parties, thanks to its large network of partners and the options available in its marketplace.
Healthcare research institutions can take advantage of AWS’s high-performance computing options and specialized research capabilities, which allow them to maintain HIPAA compliance while carrying out advanced computational workloads. AWS’s consistent service availability across international regions is a boon for organizations with global operations, as it simplifies compliance across multiple regulatory frameworks.
For companies transitioning their legacy healthcare applications to the cloud, AWS is the best choice. AWS is especially useful for companies that need to maintain strong operational control and specific security requirements. AWS’s maturity and extensive documentation make it easier for traditional healthcare IT organizations to make their first cloud migrations. For those interested in a step-by-step guide for migrating legacy applications, this resource can be invaluable.
- Large healthcare systems with diverse application portfolios and varied compliance requirements
- Healthcare research organizations that require specialized high-performance computing
- Organizations with existing AWS expertise or investment in the AWS partner ecosystem
- Multinational healthcare operations that require consistent global deployment
Consider AWS when your priority is maximum flexibility and service breadth, with the resources to properly configure and maintain complex environments. The platform’s extensive marketplace and partner network provide pre-validated solutions for numerous healthcare scenarios.
Why Azure is the Best Choice
Azure is the best choice for healthcare organizations that are already using Microsoft. Azure infrastructure and Microsoft 365 applications work together seamlessly to create a consistent boundary around all PHI touchpoints. Healthcare providers who use Microsoft Teams for telehealth, SharePoint for document management, and Dynamics for patient relationships will benefit from having the same security controls across all of these platforms.
Companies that use a combination of cloud and on-premises infrastructure often find Azure’s hybrid capabilities to be particularly useful. Azure Arc provides consistent governance across traditional data centers and multiple clouds. The platform puts a strong focus on compliance management, with features like Compliance Manager and Microsoft Purview that significantly cut down on the administrative overhead associated with maintaining documentation and collecting evidence.
Azure’s balanced approach to automation and control is particularly beneficial to healthcare organizations with limited security personnel. This is because Azure provides clear implementation guidance and healthcare solutions that are purpose-built. The platform also offers a simplified licensing model for healthcare compliance features, which allows for more predictable budgeting compared to the complex pricing structures of other providers.
- Healthcare providers who use Microsoft 365 extensively for clinical and administrative workflows
- Organizations that manage hybrid environments with a substantial on-premises infrastructure
- Healthcare organizations with stringent compliance documentation requirements
- Providers that implement telehealth solutions integrated with electronic health records
Azure is the best choice when your organization values integration across productivity tools, clinical applications, and infrastructure under a unified compliance framework. Its strength lies in creating a seamless experience that maintains compliance throughout the patient data lifecycle.
When to Choose GCP
Google Cloud Platform is a top choice for healthcare organizations that value simplicity in security and want to leverage advanced analytics capabilities. Organizations that don’t have a lot of dedicated security personnel will appreciate GCP’s security-by-default approach, which reduces the chance of configuration errors while still offering strong protection. The platform’s Healthcare API provides ready-made interfaces for working with healthcare data formats like FHIR, HL7v2, and DICOM, eliminating the need for a lot of custom development.
Healthcare companies that use artificial intelligence and machine learning for clinical decision support, medical imaging analysis, or population health management will find GCP’s AI Platform very useful. The integration between these advanced analytical capabilities and HIPAA-compliant data storage creates streamlined workflows for healthcare innovation.
Using Multiple Clouds for Optimal Security
Many healthcare organizations are now using a multi-cloud strategy that uses the best parts of different providers while avoiding being locked into one vendor. This strategy can improve resilience and security when it is implemented with careful planning and consistent governance. A good multi-cloud strategy lets organizations choose the best provider for each workload while staying compliant across environments.
Ensuring HIPAA compliance across multiple clouds can be achieved by implementing standardized security protocols, centralizing identity management, and consolidating monitoring. This can be done using tools like Terraform for infrastructure as code, Okta or Azure AD for cross-cloud identity, and multi-cloud management platforms like Anthos or Azure Arc to ensure consistency across different environments. It is also important to implement cloud-agnostic security frameworks like NIST or HITRUST that can be applied consistently regardless of the underlying infrastructure.
- Always use the same encryption standards and key management practices in all cloud environments
- Set up centralized identity providers with federation to each cloud platform
- Bring security monitoring and logging together in a unified dashboard
- Create standardized deployment pipelines with compliance checks built in
- Keep clear documentation of where PHI is located in each environment
When done correctly, a multi-cloud approach provides defense in depth and environmental diversity that can improve your overall security posture. However, this approach requires more expertise and can make compliance more complex if it is not carefully managed with the right tools and processes.
Usual HIPAA Compliance Mistakes and How to Dodge Them
Despite the strong capabilities of cloud providers, healthcare organizations often run into usual compliance mistakes that can cause violations. Knowing these common points of failure is crucial for creating preventative controls and verification processes that guarantee continuous compliance.
Risks from Misconfiguration
When it comes to HIPAA violations in the cloud, the most common culprit is misconfiguration of security controls. The most frequent issues found in breach investigations are public-facing storage buckets, network security groups that are too permissive, and encryption features that have been turned off. These problems typically come about when security controls are configured manually or when development cycles are accelerated and security reviews are skipped.
Avoid these hazards by using infrastructure as code with built-in compliance checks, automated configuration validation, and ongoing compliance monitoring. AWS Config Rules, Azure Policy, and GCP Security Command Center are tools that can automatically detect and fix common misconfigurations before they result in exposures. Make peer reviews for infrastructure changes mandatory and conduct regular configuration audits using compliance frameworks specific to the provider.
Dependence on Supplier Compliance
Many companies are under the false impression that choosing a HIPAA-compliant cloud provider will automatically make their implementation compliant. This misunderstanding of the shared responsibility model results in serious security control gaps that are still the customer’s responsibility. It’s important to remember that the provider is responsible for securing the underlying infrastructure, while you’re responsible for correct configuration, access control, and data protection.
Insufficient BAA Coverage
Companies often introduce new cloud services without checking their coverage under current BAAs, resulting in compliance gaps for PHI processed via these services. This problem is especially prevalent in development environments where new services are trialed before a formal security review, or when using marketplace offerings from third parties.
Make sure you keep a current list of all the cloud services your organization is using, including shadow IT and development environments. You should also have service control policies in place that stop non-BAA-covered services from being deployed in environments that are authorized for PHI. There should be clear architectural boundaries between workloads that contain PHI and non-covered services, and you should have the right controls in place to stop data from leaking across these boundaries.
Lack of Proper Staff Training
Even with technical controls in place, HIPAA compliance cannot be achieved without the right staff training on both regulatory requirements and particular cloud implementation practices. Many organizations spend a lot of money on advanced security tools but overlook the human factor. This leaves them highly vulnerable to social engineering, poor credential management, and unintentional configuration errors.
How to Maintain HIPAA Compliance in the Cloud Over the Long Term
Staying HIPAA compliant in the cloud isn’t about getting certified once and forgetting about it. It requires ongoing attention. As cloud providers roll out new services and features, healthcare organizations need to update their compliance frameworks to include these changes, all while maintaining a consistent level of security. By practicing sustainable compliance, healthcare organizations can ensure that PHI stays protected throughout its lifecycle.
Top healthcare organizations view compliance as a continuous process, not a one-off project. By incorporating security and compliance factors into everyday operations, development practices, and strategic planning, they foster an environment where HIPAA requirements are the norm, not the exception.
Consistent Security Evaluations
Establish a formal evaluation program that measures your cloud setting against current HIPAA rules and emerging hazards. These evaluations should include both automated scanning for known vulnerabilities and manual inspection of security architecture by qualified staff. Consider hiring external specialists to provide unbiased evaluation of your compliance stance, identifying blind spots that internal teams might overlook.
Alongside technical assessments, you should also conduct process evaluations that check procedural controls such as access reviews, incident response capabilities, and change management practices. Regular assessments are necessary, as well as when you make significant changes to your cloud architecture or implement new services that interact with PHI.
Real-Time Monitoring Solutions
Use a comprehensive monitoring solution that provides real-time visibility into potential compliance issues across your cloud environment. The tool should not only monitor the infrastructure configuration, but also the user activities, and should be able to identify anomalies that may indicate security incidents or compliance drift. Automate the remediation for common issues and escalate complex issues to the appropriate personnel.
Set up alerting thresholds that balance sensitivity against alert fatigue, focusing on high-risk activities involving PHI. Implement context-aware monitoring that considers user roles, access patterns, and data sensitivity when evaluating potential incidents. Integrate monitoring across multiple cloud environments to provide consistent visibility regardless of where PHI resides.
- Implement real-time infrastructure compliance scanning with tools like Prisma Cloud, Lacework, or native provider solutions
- Deploy data loss prevention tools that identify inappropriate transmission of PHI
- Configure user and entity behavior analytics to detect anomalous access patterns
- Implement continuous validation of encryption status for all PHI repositories
- Monitor privileged user activities with heightened scrutiny
Regularly review monitoring effectiveness by testing detection capabilities against simulated compliance violations and emerging threat patterns. Update monitoring rules and alerting thresholds based on these findings to ensure continuous protection against evolving risks.
Gathering Documentation and Evidence
Keep detailed records of your compliance controls, which can include things like technical configurations, policy implementations, risk assessments, and remediation activities. This documentation can be used as proof in case of audits, and it can also be used as a reference for maintaining consistent compliance practices. Use compliance documentation tools that are specific to each provider, like AWS Artifact, Azure Compliance Manager, and GCP Compliance Reports, to supplement your internal documentation.
Common Questions
Many healthcare organizations looking to migrate to the cloud often have similar questions about HIPAA compliance across the major providers. The answers to these questions can help address their most urgent concerns and provide useful advice for making implementation decisions. For those concerned about potential cloud vendor lock-in, understanding these strategies can be particularly beneficial.
Is it possible to achieve HIPAA compliance without a BAA from my cloud provider?
Unfortunately, it is not. According to the HIPAA Omnibus Rule, it is mandatory for covered entities to have a signed Business Associate Agreement from any service provider that handles, transmits, or stores Protected Health Information for them. Cloud providers are included in this category because they provide the infrastructure where PHI is stored, even if they do not directly interact with the data.
Regardless of the security measures you have in place, using cloud services without a BAA is a direct violation of HIPAA. Without a BAA, your organization is at risk of legal exposure, including potential civil penalties and the requirement to take corrective action from regulatory authorities.
For those who are using a cloud provider that does not provide a HIPAA BAA, the only options are to either switch to a provider that does or to create a technical architecture that ensures PHI never reaches the provider’s systems. This could mean encrypting the data with keys maintained by the customer before the data leaves your controlled environment. However, this type of architecture can be complex and limiting.
“The fastest way to fail a HIPAA audit is to store PHI with a provider that hasn’t signed a BAA. No amount of security controls can compensate for this fundamental compliance requirement.” — Healthcare Compliance Officer
Which cloud provider has the most services eligible for HIPAA?
Currently, AWS is the frontrunner in the range of HIPAA-eligible services, with more than 130 services included in their BAA. This wide-ranging coverage allows for intricate healthcare workloads that use advanced features such as machine learning, IoT integration, and specialized analytics while still maintaining compliance. AWS’s approach prioritizes maximizing options while clearly outlining which services can handle PHI.
- AWS: 130+ HIPAA-eligible services covering infrastructure, platform, and specialized capabilities
- Azure: 90+ covered services with strong integration across Microsoft’s healthcare ecosystem
- GCP: 80+ covered services with particular strength in healthcare-specific APIs and analytics
- Oracle Cloud: 40+ covered services focused primarily on infrastructure and database offerings
- IBM Cloud: 35+ covered services with emphasis on enterprise integration and security
However, raw numbers don’t tell the complete story. Azure offers deeper integration across its covered services, while GCP provides more healthcare-specific functionality within its eligible service portfolio. The ideal provider depends more on which specific services align with your technical requirements rather than simply maximizing the number of available options.
Companies must identify the exact features they require for their healthcare applications and confirm that those specific services are included in the provider’s BAA. A provider with a smaller overall service offering may still be the best option if those services align perfectly with your technical needs and offer superior capabilities specific to healthcare.
What is the cost of a HIPAA-compliant cloud implementation?
Generally, HIPAA compliance increases baseline cloud costs by 20-40%. However, this additional cost can vary widely depending on the method of implementation and the current security practices. The cost of compliance includes the addition of logging infrastructure, improved encryption capabilities, network isolation controls, and administrative overhead for maintaining proper documentation and monitoring.
The biggest cost contributors are the comprehensive audit logs with extended retention periods, redundant implementations for high availability, encryption key management infrastructure, and additional security services such as threat detection and vulnerability scanning. Companies can often reduce these costs through reserved capacity commitments, right-sized compliance implementations, and automated governance tools that reduce manual overhead.
The way cloud providers structure their compliance-related costs varies. GCP includes many security features in their base pricing, whereas AWS and Azure often offer them as premium add-on services. For enterprise customers, these differences often disappear through negotiated agreements that bundle compliance capabilities. However, smaller organizations may find significant variation in effective compliance costs across providers.
Do I need to change my compliance measures for each cloud provider?
Even though HIPAA requirements are the same no matter which cloud provider you use, the ways you meet these requirements can differ a lot between platforms. Each provider has different security services, compliance tools, and default configurations that need unique approaches. You’ll need to adjust your compliance frameworks to use the capabilities of each provider while still keeping your security consistent.
Start by creating a compliance framework that isn’t tied to any specific provider. This should outline the necessary controls and outcomes. Then, use technical solutions specific to your provider to meet these requirements. This way, you keep your security consistent while also recognizing the differences in architecture between platforms. Keep track of these implementations in a centralized compliance registry. This will map controls to specific configurations in the cloud across different environments.
What if my cloud provider has a data breach?
If a security incident occurs with your cloud provider that affects your PHI, their responsibilities will be determined by the terms of your Business Associate Agreement. All major providers pledge to notify customers of confirmed breaches, but the exact timeframes and notification procedures can vary. These notifications usually contain information about the services affected, when the breach happened, and what actions customers should take.
When it comes to notifying affected individuals and regulatory authorities of a breach, your organization is still ultimately responsible. Even if the breach is on the cloud provider’s end, it doesn’t absolve you of these obligations. However, provider documentation can help with your investigation and response. It’s important to have an incident response plan in place that specifically addresses cloud provider breaches. This should include procedures for assessing the impact, verifying containment, and coordinating with provider security teams.
It’s exceedingly rare for provider breaches to affect the underlying infrastructure instead of specific customer environments among major cloud providers. The majority of “cloud breaches” are actually due to customer misconfigurations rather than provider security failures. This fact highlights the need for correct configuration, monitoring, and access controls within your cloud environment.
|
Provider Responsibility |
Customer Responsibility |
|---|---|
|
Notify customers of confirmed breaches |
Determine if breach affected PHI |
|
Provide breach timeline and affected services |
Notify affected individuals |
|
Implement corrective actions for infrastructure |
Report to HHS Office for Civil Rights |
|
Support customer investigation |
Document incident response actions |
|
Maintain evidence of security controls |
Implement additional safeguards if needed |
In selecting your cloud provider, review their security track record, compliance certifications, and transparency regarding past incidents. Major providers publish detailed security information including SOC 2 reports, penetration testing procedures, and infrastructure security practices that can inform your risk assessment.
In the end, there isn’t a one-size-fits-all cloud provider for every healthcare organization. The best choice will depend on your unique technical needs, current technology investments, security capabilities, and compliance requirements. By knowing how each provider handles HIPAA compliance and putting the right controls in place in your chosen environment, you can safely move healthcare workloads to the cloud while still ensuring strong protection for sensitive patient data.
The SlickFinch team has extensive experience deploying and maintaining HIPAA compliant solutions on all three of these cloud platforms, and are on hand should you or team need help or guidance.