Key Points
- CI/CD pipelines are increasingly being targeted by cybercriminals, with 65% of companies reporting security incidents in their build systems in the last year
- The most common pipeline vulnerabilities can be prevented by implementing least privilege access control, secrets management, and container image scanning
- Ephemeral build environments significantly reduce the attack surface by destroying environments after each build
- Pre-commit hooks and automated security testing can catch 87% of vulnerabilities before they enter your codebase
- SlickFinch’s cloud security solutions provide comprehensive protection across all pipeline stages while maintaining deployment velocity
Why Your CI/CD Pipeline Is Currently a Security Risk
Your CI/CD pipeline could be the weakest link in your infrastructure. While you’ve likely invested heavily in application security, the very systems that build and deploy your code are often left unprotected, creating an attractive target for attackers looking for persistent access to your environment. These automated pipelines hold privileged credentials, source code, and direct paths to production – making them the ultimate prize for sophisticated cybercriminals.
According to a recent study by Crowdstrike, 78% of businesses do not apply the same stringent security measures to their build systems as they do to their production environments. This security loophole creates a vulnerability for supply chain attacks, which could potentially compromise not only your infrastructure but also the systems of your customers. Securing your CI/CD pipeline is not only about protecting your own assets, but also about fulfilling a crucial duty to your entire digital ecosystem.
Latest Attack Trends Aiming at Build Systems
Since 2021, supply chain attacks targeting CI/CD pipelines have increased by a whopping 742%, making them a favourite entry point for advanced threat actors. The notorious SolarWinds breach, where attackers injected malicious code directly into the build process, affected thousands of organisations and highlighted the destructive potential of pipeline compromises. More recently, groups stealing cryptocurrency have moved their focus from direct application attacks to targeting CI/CD infrastructure, where they can quietly modify code to include backdoors that persist across multiple releases.
It’s becoming increasingly apparent that hackers are shifting their focus to the “left” of the development lifecycle. Instead of focusing on exploiting deployed applications, they’re now more interested in compromising the systems that create them. By gaining access to build servers or repository credentials, hackers can inject malicious code that bypasses traditional security controls because it appears to come from a trusted source. These attacks are particularly dangerous because they often remain undetected for months, allowing extensive lateral movement throughout your environment.
Unseen Consequences of Pipeline Security Breaches
If a CI/CD pipeline is breached, the fallout goes far beyond the initial security event. Recent industry reports indicate that companies spend an average of $4.3 million to fix each pipeline breach. This shocking number covers not only the cost of responding to the incident and conducting a forensic investigation, but also the significant work needed to ensure that no lingering backdoors are left in any artifacts that were built earlier.
The greatest expenses usually result from business interruption and damage to reputation. Companies often have to stop deployments completely during remediation, bringing development to a standstill as security teams manually review code and rebuild systems. For companies in regulated sectors, pipeline breaches often lead to compliance violations and potential penalties. A healthcare organization recently reported that it had spent more than 45,000 person-hours rebuilding its entire delivery pipeline after a breach was discovered, which had a devastating impact on their product roadmap and market position.
Core CI/CD Security Basics
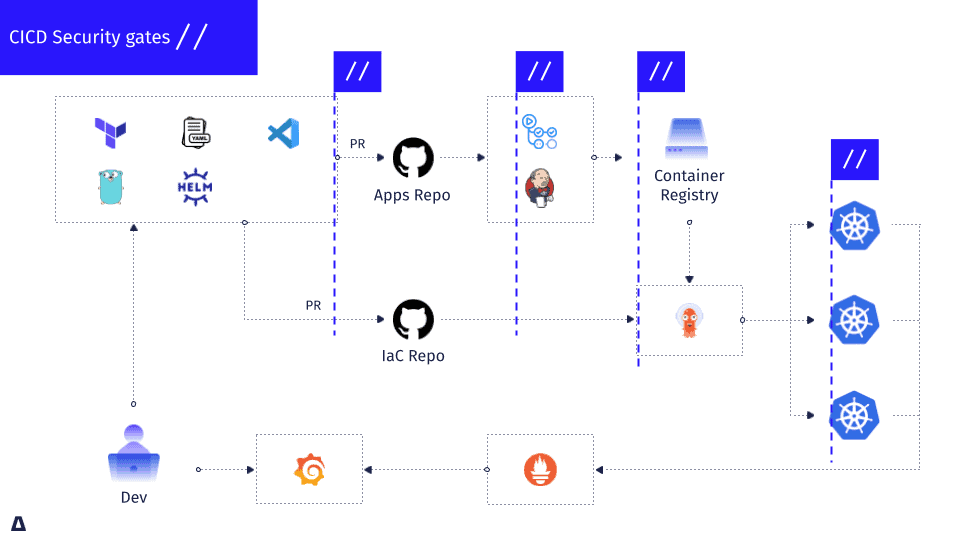
“Securing CI/CD pipelines through …” from www.cncf.io and used with no modifications.
For successful CI/CD security, you need to safeguard every pipeline stage with controls that are specific to the unique risks of each component. Instead of viewing pipeline security as one issue, think of it as a series of linked security areas: safeguarding the code repository, securing the build environment, managing artifacts, and controlling deployment. This multi-layered method creates several security checkpoints that stop a single weakness from putting your whole pipeline at risk.
Building a Security-Centric Pipeline
When setting up a pipeline that prioritizes security, it’s important to keep a strict separation between the different stages and environments. Your build systems should not have direct access to production credentials. Each component should only have the minimum necessary privileges. You can create a clear boundary that limits lateral movement in case of a breach by isolating the build servers from both the development workstations and production environments through network segmentation.
When you’re designing your pipeline, make sure to keep immutability at the forefront of your mind. Once an artifact has been built, it shouldn’t be modified. Instead, it should either be promoted or rejected based on security testing. This will ensure that what you test is exactly what you deploy, which will help to eliminate opportunities for tampering at the last minute. You can also reduce risk by breaking your pipeline into smaller components that each have a single purpose. This will limit what any one system can access. For example, we were able to help a financial services client redesign their pipeline architecture using these principles. As a result, they were able to reduce security incidents by over 90%, while actually increasing the frequency of their deployments.
Comparing DevSecOps and Conventional Security Methods
Conventional security methods often regard security as the final hurdle before production, which can lead to friction and hold-ups between development and security teams. DevSecOps, on the other hand, fundamentally reshapes this relationship by incorporating security practices and automated testing at every stage of the development lifecycle. Rather than being a hindrance, security becomes a facilitator of safe, quick delivery.
The contrast is clear: instead of waiting for days for a manual security review, developers receive instant feedback on potential vulnerabilities during the coding, commit, and build phases. Security tools run automatically at each stage of the pipeline, with the results directly integrated into the familiar workflows and dashboards of the developer. This shift-left approach speeds up delivery while improving security results – organizations that implement mature DevSecOps practices detect 80% of vulnerabilities earlier in the development process, significantly reducing the cost and time to fix compared to traditional models.
Striking a Balance between Speed and Security
The apparent tension between security and speed is mostly a misconception. When pipeline security is implemented effectively, it can actually speed up delivery by avoiding the expensive disruptions and rollbacks that are caused by security incidents. The trick is to choose security controls that meet your development speed needs, integrate them smoothly into developer workflows, and automate wherever you can.
Start with security measures that have a high impact and low friction, such as infrastructure-as-code security scanning. These measures can prevent misconfigurations without adding manual steps. For controls with higher friction, like penetration testing, only use these for critical components instead of applying them universally. Choose security tools with rich APIs that can integrate directly into your existing pipelines, rather than creating separate security processes. This balanced approach keeps the main benefits of CI/CD, while also providing strong protection against the most likely threats to your pipeline.
Securing your Code Repository
The code repository is the bedrock of your CI/CD pipeline and is one of the most important areas to secure. If a repository is compromised, attackers can insert harmful code directly into your source, potentially circumventing any security measures further down the line. A good security strategy for your repository should include authentication, access control, and code validation to make sure only legitimate changes are introduced into your pipeline.
Nowadays, risks to code repositories are not just about direct compromise. They also include social engineering attacks that target developers with commit access. If you apply defense-in-depth strategies at this early stage, you’re setting up a secure base for your whole pipeline. This also significantly lowers the chances of supply chain attacks spreading through your delivery process.
Branch Protection Rules That Actually Work
To protect your branches effectively, you need to go beyond basic merge requirements and implement comprehensive safeguards for your critical branches. You should configure mandatory code reviews with a minimum of two reviewers for any changes to main branches. This will prevent single-developer attacks and ensure quality control. You should also enable signed commit verification to cryptographically validate commit authenticity. This will prevent attackers from impersonating legitimate developers even if credentials are compromised.
It’s crucial to make status checks obligatory and include both code quality and security scans that must pass before merging is allowed. To provide the highest level of protection, enforce branch restrictions that prevent force pushes and deletions, even for administrators. The most secure organizations also require a linear history to maintain a clear, auditable record of all changes. This prevents history rewrites that could hide malicious activity.
Why You Need Code Signing
Code signing is like a digital signature for your code. It uses cryptography to confirm that the code is genuine and hasn’t been tampered with. If you make your developers sign all their commits with their personal GPG keys, you’ll know exactly who made what changes. This stops people from injecting unauthorized code into your repository. It’s a really good way to protect yourself from supply chain attacks, where hackers try to pretend to be real developers.
Set up organizational signing requirements by configuring git to reject unsigned commits to protected branches. Whenever possible, keep signing keys in hardware security modules (HSMs) to prevent key theft. For enterprise environments, set up a structured key management process that includes key rotation schedules, revocation procedures, and secure backup practices. When set up correctly, code signing creates an auditable chain of trust from the initial commit to the production deployment that can detect tampering at any stage. For more insights on implementing effective DevOps practices, explore the case study on CI/CD automation.
Dependency Scanning to Ward Off Supply Chain Attacks
Third-party dependencies are one of the most common attack vectors in today’s applications, with the average project having hundreds of direct and indirect dependencies. It’s important to have automated scanning in place that checks dependencies against several vulnerability databases at the time of commit to catch any known security issues before they become part of your codebase. In addition to CVE detection, sophisticated dependency scanning should also include license compliance checks and the ability to detect suspicious packages that could be indicative of typosquatting or dependency confusion attacks.
For applications that are important, it might be a good idea to use a private artifact repository that mirrors and validates approved dependencies, which will stop direct internet downloads during builds. You can set up your scanning tools to enforce security policies based on how severe a vulnerability is, and critical vulnerabilities will automatically stop builds. Organizations that have mature dependency management also use Software Bills of Materials (SBOMs), which provide a full inventory of all components and make it easier to respond to incidents during zero-day events.
Use Pre-commit Hooks for Early Detection
Pre-commit hooks are your first line of defense against security issues. They scan code before it even reaches your repository. These client-side scripts automatically run security checks when developers attempt to commit changes. They provide immediate feedback on potential vulnerabilities, secrets exposure, or policy violations. Pre-commit hooks work on developers’ machines during normal workflow. This can dramatically reduce the number of security issues that reach your shared codebase.
Set up hooks to find standard security problems such as hardcoded credentials, insecure functions, and SQL injection vulnerabilities. To ensure consistent usage throughout your organization, standardize pre-commit hook configurations and distribute them via repository templates. The best implementation combines mandatory hooks for critical checks with optional hooks for style and quality concerns, striking a balance between security requirements and developer experience.
Securing Your Build Environment
Given that your build environment is a prime target for hackers (as they can inject malicious code into artifacts that will be deployed to production), it’s crucial to protect it. Build systems often have more privileges and direct access to sensitive credentials than production environments, making them a desirable target for attack. A blend of isolation, least privilege, and runtime security controls is necessary to protect your build environment.
You should implement security measures in your build environment that are as rigorous as those in production, if not more so. Keep in mind that a compromised build server can potentially affect all downstream environments, making this phase a critical security boundary in your pipeline.
Temporary Build Environments
Temporary build environments are a great way to secure your CI/CD pipeline. They work by destroying and then recreating clean build environments for each pipeline run. This means that no residual artifacts, credentials, or potential backdoors are left behind between builds, which eliminates persistent attack vectors. Each build starts from a known-good state defined as code, so even if attackers gain temporary access, it’s much harder for them to maintain that access over time.
Use containerization or infrastructure-as-code to create temporary environments that provide fresh build agents for each job. These environments should be configured with only the tools and permissions needed for specific build tasks, which will further decrease the attack surface. Organizations that are more advanced in temporary build practices also use reproducibility validation. This compares artifacts from several independent build environments to find potential tampering.
Securing Container Images
The container images you use in your build environment are key security components, because they underpin your build process. It’s best to use a multi-layered approach that starts with minimal base images from sources you trust, and that only contain the components you need. You should scan all base images for vulnerabilities before you use them, and keep an eye on them for new CVEs, triggering rebuilds automatically when security updates are available.
Make sure you have stringent image signing requirements in place to prevent unauthorized images from running in your environment. Set up your container runtime with security features such as user namespace remapping, seccomp profiles, and read-only filesystems to minimize the potential damage from container escapes. For the highest level of security, you might want to think about using runtime application self-protection (RASP) tools. These can identify and stop unusual behavior within containers during the build process, possibly spotting zero-day attacks before they can impact your artifacts.
Security Checks for Infrastructure as Code
Infrastructure as Code (IaC) templates are responsible for defining the security configuration of your pipeline environments. This makes their security a key control point. You should implement automated security scanning for all IaC templates. This will help you detect common misconfigurations such as overly permissive security groups, unencrypted storage, or missing authentication requirements. These scans should be run during development with pre-commit hooks. They should also be run as part of your CI/CD pipeline. This will help prevent insecure infrastructure from being deployed.
Instead of just basic compliance checking, use policy-as-code frameworks like Open Policy Agent. This will help you apply your organization’s security standards across all infrastructure definitions. You should also create a secure default template library. This should include pre-hardened configurations for common resources. This makes it easier for your teams to adhere to security best practices. The most advanced organizations also use drift detection. This is a continuous comparison of deployed infrastructure against approved templates. It helps you spot unauthorized or potentially harmful changes.
Best Practices for Managing Secrets
Managing secrets is one of the most important security challenges in CI/CD pipelines. This is because these environments need access to sensitive credentials, and they are often the targets of attacks. If an API key or database password is exposed, it could compromise your entire environment. Despite this, many organizations still use insecure practices like hardcoded credentials or unencrypted environment variables. To implement robust secrets management, you need dedicated tools, clear processes, and a change in the way developers handle credentials.
The purpose of managing secrets effectively is not just to encrypt credentials. Rather, it’s to put in place a robust system that limits human access to secrets, enforces the principle of least privilege, and offers full audit trails for all credential use. This strategy significantly cuts down both the chances and possible effects of credential theft.
Why Environment Variables Fall Short
Environment variables may provide a basic level of protection against hardcoded secrets, but they can also create a host of security vulnerabilities in CI/CD environments. These variables often show up in logs, error messages, and debugging output, which can lead to accidental exposure. Even more troubling, environment variables usually stick around for the duration of a build job and can be accessed by any code that’s run in that environment. This includes third-party dependencies that could be compromised.
Keeping a Log of All Pipeline Activities
It is essential to have a detailed record of all pipeline activities for security purposes, both for detection and for forensic investigation. Make sure you implement detailed logging that captures every pipeline event, including when builds are initiated, when code is checked out, when tests are executed, and when deployments are made. These logs should include key contextual information such as who triggered the event, the source commit, the execution environment, and timestamps that allow security teams to reconstruct the complete sequence of events during an incident.
Store logs in a secure, tamper-proof storage system that prevents any changes even if attackers manage to access your build systems. Set up log retention policies that balance the needs for security with the requirements for performance and compliance – usually a minimum of 90 days for standard environments and up to a year for high-security or regulated workloads. The best logging implementations also include integrity checks using cryptographic signatures or blockchain-based methods that can definitively show that logs have not been altered.
It’s important for security teams to frequently review pipeline logs. This allows them to determine what the standard activity patterns are and see if there are any potential security gaps. Things to watch out for include unusual build timing, unexpected environment variables, or unauthorized configuration changes, all of which could suggest a compromise.
- User activity logs – these keep track of all hands-on interactions with pipeline systems
- Build activity logs – these provide in-depth information about each build process
- Configuration adjustment logs – these monitor all changes to pipeline definitions
- Deployment event logs – these record all artifact promotions between environments
Combine these logs with your security information and event management (SIEM) system to correlate pipeline activities with other security events throughout your infrastructure, giving a comprehensive view of possible threats.
Finding Odd Build Patterns
Advanced attacks on CI/CD systems usually appear as subtle irregularities in build patterns, not clear invasions. Use behavioral analytics to set baseline metrics for regular pipeline operation, such as normal build times, resource use, network traffic patterns, and execution trends based on time of day. These baselines act as a basis for anomaly detection systems that can spot possible security incidents even when attackers are using valid login information.
Set up automatic notifications for high-risk anomalies like builds started outside of regular working hours, unusually long-running jobs that could signal data theft, or builds that access network resources not typically linked to their function. Keep a close eye on changes in artifact sizes or contents that don’t match code changes, as this could suggest tampering during the build process. These subtle signs often offer the first hint of complex supply chain attacks.
High-end detection systems should include machine learning models that are trained on your particular pipeline patterns to decrease false positives while keeping a high sensitivity to real threats. Over time, these systems become more effective as they learn the unique traits of your development workflow, ultimately detecting even the most complex attacks that try to blend into regular operations.
Automated Security Protocols
In the event of a security breach in your CI/CD pipeline, it’s crucial to respond quickly to limit the possible harm. Design automated security protocols that can carry out preset security measures without the need for human involvement, significantly shortening the time between detection and containment. These protocols should include immediate containment measures such as isolating affected build agents, revoking compromised credentials, and stopping ongoing deployments until the security team can investigate.
For various pipeline security incidents, you should establish layered response strategies based on the severity and confidence level. Low-confidence detections may cause increased monitoring and alerts to security teams, while high-confidence detections of critical issues should automatically put containment measures into action. Make sure to document these automated responses clearly so developers know why builds might be halted or credentials revoked during security incidents.
Continually put your response playbooks to the test through tabletop exercises and simulated incidents to ensure they operate as they should during real security events. These tests should include scenarios that are specific to CI/CD environments, such as compromised build agents, poisoned dependencies, and leaked pipeline credentials. By continually refining these playbooks based on test results and evolving threats, you create a resilient security response capability that can contain incidents before they affect production systems.
Protecting Common CI/CD Platforms
Every CI/CD platform comes with its own unique security design, setup options, and potential weaknesses that need special hardening techniques. Most CI/CD platforms are configured by default to be easy to setup, but this can also make them insecure if not hardened correctly. It’s important to understand the security model of your specific platform so you can implement the right protections for the risks it presents.
When you’re looking at CI/CD tools, make sure you’re choosing ones that have up-to-date security features. This includes things like detailed permissions, secrets management integration, and thorough audit logging. If your organization already uses specific platforms, you should concentrate on finding and fixing any known security issues with those tools. You can do this through configuration hardening and compensating controls.
How to Make Jenkins More Secure
As Jenkins is one of the most popular CI/CD platforms, it presents a number of security challenges due to its plugin architecture and powerful automation capabilities. The first step to making it more secure is to implement the principle of least privilege throughout your Jenkins environment. This means running the Jenkins controller with a dedicated service account that has minimal system permissions, configuring agents to run jobs as unprivileged users, and implementing job-specific credential scoping that prevents jobs from accessing credentials not explicitly granted to them. You should also enable built-in security features like CSRF protection, agent-to-controller access control, and script security sandbox mode to prevent common attack vectors.
Securing GitHub Actions
When it comes to GitHub Actions, you should ensure that repository permissions are configured to avoid unauthorized changes to workflows. Also, consider implementing branch protection rules to prevent direct commits to protected branches. You should also use environment protection rules to limit which workflows can deploy to production environments. If you’re using actions from the marketplace, you should have an internal approval process in place. You might also want to consider forking approved actions to your organization’s repositories. This way, they can be audited and version-pinned to prevent supply chain attacks. Always use GitHub’s encrypted secrets storage for credentials and use OpenID Connect for cloud provider authentication instead of long-lived access keys.
Securing GitLab CI
For GitLab CI, you should increase security by isolating runners. This means using different runners for various projects or trust levels. Projects with a high level of security should run on dedicated infrastructure. You should also configure network segmentation for runners. This limits their access to only the necessary systems and services. It’s also important to implement proper runner authentication. This should be done using strong tokens that are regularly rotated. GitLab’s protected environments feature should be used to limit which branches can deploy to production. All CI/CD variables that contain sensitive information should be marked as “protected” and “masked”. This helps to prevent disclosure.
If your organization uses a self-hosted GitLab, you should put in place extra security measures at the infrastructure level. This includes regular security patching, network filtering to restrict access to the GitLab instance, and system log monitoring to detect any unusual access patterns. You might also want to consider using GitLab’s premium security features, such as dependency scanning and container scanning. These features will add automated security checks to your pipelines.
Securing Your CircleCI Environment
When it comes to CircleCI, you can enhance security by setting up context restrictions to control which projects can access sensitive environment variables, setting up approval jobs for production deployments, and using restricted execution environments for jobs that handle sensitive data. Make sure to enable the organization’s security features such as the IP ranges feature to control which IP addresses can trigger builds, two-factor authentication for all users, and audit logging for full visibility into all activities. If your projects use orbs (CircleCI’s reusable configuration components), set up a strict approval process and version pinning to protect against supply chain attacks through malicious orb updates.
Putting CI/CD Security into Practice
- Start with high-value, easy-to-implement security measures like managing secrets and controlling access
- Roll out security in stages, starting with the most important systems and gradually moving on to others
- Track your progress in improving security with tangible metrics like the rate at which you detect vulnerabilities
- Strike a balance between security controls and the developer experience to ensure that your team adopts them
- Make sure to document and clearly communicate any changes in security to everyone involved
To successfully put CI/CD security into practice, you need to strike a balance between best practices in theory and what is feasible in practice. Most organizations can’t put all security controls into place at once, so it’s essential to prioritize. Start by dealing with the parts of your pipeline that pose the greatest risk – usually managing secrets, controlling access, and securing the build environment – which together address the most common ways attackers get in with relatively little effort needed to implement.
Take a step-by-step approach that lets teams adjust to new security practices without slowing down delivery. Start by introducing security controls in non-critical pipelines so you can fine-tune configurations and workflows before implementing them in business-critical systems. This measured approach builds confidence and provides chances to tweak implementation details based on actual feedback from development teams.
Keep everyone in the loop about security changes during implementation, why they’re happening, and how they’ll impact workflows. This openness will foster trust and make it more likely that people will adhere to new security rules, especially if these changes will affect existing development practices.
A Month-Long Plan to Enhance Your CI/CD Security
Upgrade your CI/CD security in just 30 days by following a well-structured plan that addresses the most critical vulnerabilities first and builds momentum for a comprehensive security adoption. Start with a quick risk assessment on the first three days to spot the most dangerous pipeline vulnerabilities. Focus on the security of credentials management, access controls, and the build environment. From the fourth to the tenth day, concentrate on quick wins such as the implementation of secrets management tools, enabling MFA for all pipeline systems, and setting up basic branch protection rules that can be deployed quickly with minimal disruption. The middle phase, from the eleventh to the twentieth day, should be used to implement the core security controls, including pipeline activity logging, container image scanning, and dependency analysis. The final phase, from the twenty-first to the thirtieth day, should focus on automation and monitoring. This includes the integration of automated security testing, anomaly detection, and response playbooks to ensure a sustainable improvement in security.
Creating a Program for Security Champions
For CI/CD security to be sustainable, it’s essential to have security expertise within development teams, instead of relying only on centralized security organizations. By setting up a program for security champions, you can identify and empower developers with an interest in security to become advocates for security within their teams. You should give these champions specialized training in pipeline security, access to advanced security tools, and direct lines of communication with the security team to raise concerns or ask for guidance.
Design the system to regularly include sessions where champions can discuss new threats, share successful security implementations, and work together to solve common challenges. Create incentives that reward and acknowledge security champions for their contributions, such as opportunities for certification, conference attendance, or visibility with leadership. When properly supported, these champions become powerful force multipliers that can speed up security adoption across the organization while ensuring security controls remain compatible with development workflows.
Important Security Metrics
For your CI/CD security to be effective, you need to have significant metrics that show your current security position and how it has improved over time. Don’t just focus on activity metrics, concentrate on outcome-based metrics. Instead of just measuring the number of scans you’ve done, measure the rate at which you’ve fixed security findings. Instead of just counting vulnerabilities, measure the average time it takes to fix critical vulnerabilities. Instead of just counting the number of security tools you’ve deployed, measure the percentage of your pipeline that is covered by security. These outcome-focused measurements give you actionable insights into your real security position and help you prioritize your improvement efforts towards the areas that will have the biggest impact. Before you implement new security controls, establish a baseline for each metric. Then, track trends over time to show concrete security improvements that can justify continued investment in pipeline security.
Secure Your Pipeline Today
Don’t wait for a security breach to start focusing on your CI/CD pipeline security. Start by evaluating your current pipeline against the practices listed in this guide, and identify the highest-risk gaps in your security posture. Implement quick wins like secrets management and access control improvements that provide immediate security benefits while building momentum for your broader security program. Remember that CI/CD security is a continuous journey rather than a destination – start with manageable improvements today and build toward comprehensive protection over time. CI/CD automation can help you implement robust pipeline security controls while maintaining the speed and agility that make CI/CD valuable to your organization. Reach out to SlickFinch today if you have any questions on CI/CD pipeline security.
Common Questions
Here are some questions that most organizations have when they start thinking about CI/CD pipeline security. These practical insights will help you understand the usual challenges and make better decisions about your security strategy.
What makes CI/CD pipeline vulnerabilities different from application vulnerabilities?
CI/CD pipeline vulnerabilities pose a different kind of risk than application vulnerabilities because they can affect every application that is built through the compromised pipeline. Application vulnerabilities usually only affect one system, but pipeline vulnerabilities allow attackers to inject malicious code into multiple applications at the same time or to establish persistent access that survives application updates. Pipeline vulnerabilities are also usually less visible to traditional security tools because they exist in the build and deployment infrastructure, not in the application code itself. This combination of wide-ranging impact and reduced visibility makes pipeline vulnerabilities especially dangerous and something that security should focus on.
What is the basic security requirement for a CI/CD pipeline in regulated industries?
Regulated industries such as finance, healthcare, and critical infrastructure should at the very least implement: strong access controls with multi-factor authentication and fine-grained permissions, comprehensive secrets management using a dedicated vault solution, complete activity logging with at least 12 months retention, signed commits and artifacts with hardware-protected keys, container and dependency scanning integrated into the pipeline, and network segmentation that isolates build systems. These controls address the core security requirements found in most regulatory frameworks including PCI-DSS, HIPAA, and SOC2.
In addition to these technical measures, organizations that have to comply with regulations also need to implement process controls. These include the separation of duties for changes to pipeline configuration, regular security testing of pipeline components, and documented procedures for responding to incidents that are specific to CI/CD security events. These process controls make sure that technical security measures stay effective over time and can adapt to changes in compliance requirements.
Is it possible to secure our CI/CD pipeline without sacrificing speed?
Yes, when done right, CI/CD security measures can actually increase reliability and confidence while keeping or even speeding up deployment cycles. The secret is to weave security into your existing workflows rather than creating separate security stages. Concentrate on automated security controls that operate concurrently with existing pipeline steps, scanning tools that are optimised for speed even for large codebases, and policy-as-code methods that enforce security requirements without the need for manual reviews. If you catch security issues early in the development process using tools like pre-commit hooks and IDE integrations, you can fix them quickly with little effect on delivery timelines, which is much better than finding the same issues later on.
What are the most cost-effective CI/CD security tools for small teams?
For small teams that have limited security resources, it’s important to prioritize tools that can address a wide range of security issues and that require minimal setup and maintenance. Start by implementing a secrets management solution, such as HashiCorp Vault or AWS Secrets Manager, to prevent the most common cause of pipeline compromises. Then, add a dependency scanning tool, such as OWASP Dependency-Check or Snyk, to catch vulnerable components before they make it into your codebase. Lastly, think about adding a container security solution to scan images for vulnerabilities and enforce security policies during builds.
- Secrets management: HashiCorp Vault (open-source core), AWS Secrets Manager, or Azure Key Vault
- Dependency scanning: OWASP Dependency-Check (free), Snyk (free tier available), or GitHub Dependabot (free for public repositories)
- Container security: Trivy (free), Clair (open-source), or Docker Scout (included with Docker subscriptions)
- Infrastructure as Code scanning: Checkov (open-source), tfsec (free), or Snyk IaC (free tier available)
These tools deliver substantial security improvements with relatively modest implementation effort, making them ideal starting points for resource-constrained teams. As your security program matures, you can expand to more specialized tools that address specific risk areas in your environment.
Think about using security as code practices for team collaboration. This embeds security configurations directly in your repositories. This lessens the maintenance burden by treating security controls as part of your usual development workflow. It is not a separate security process.
How frequently should we check our CI/CD pipeline security?
Adopt a layered audit strategy with ongoing automated compliance checks for basic security controls, manual reviews of access controls and security configurations every month, and full security evaluations of your entire pipeline every quarter. This tiered approach combines regular verification with resource efficiency by focusing detailed manual reviews on the components with the highest risk.
Complement the regular rhythm with audits that are driven by events and are triggered by significant changes to your pipeline architecture, tools, or team composition. These reviews that are focused ensure that security controls remain effective as your environment evolves. For organizations with mature security programs, consider annual third-party penetration testing that specifically targets your CI/CD infrastructure to identify vulnerabilities that internal processes might miss.
Put all audit findings in a central security backlog, clearly indicating what needs to be fixed first based on risk. Keep an eye on how long it takes to fix security findings to make sure you’re dealing with problems quickly and thoroughly. This structured way of auditing your pipeline gives you a continuous view of your security while focusing your security resources where they’re needed most.