Key Takeaways
- Ingress NGINX is being retired in March 2026, with no security updates after that date, making migration to an alternative solution critical
- Traefik offers the most seamless transition with its NGINX Provider, supporting 80% of common Ingress NGINX annotations without configuration changes
- Alternative options include HAProxy Ingress, Contour, and cloud-specific solutions, each with unique strengths but requiring more configuration changes
- A phased migration approach allows for testing Traefik alongside your existing Ingress NGINX setup before completely cutting over
- Beyond immediate compatibility, Traefik offers enhanced security and better performance
The Kubernetes community received a significant shock when maintainers announced that Ingress NGINX Controller will be retired in March 2026. With just 120 days remaining until no more security updates will be available, finding a suitable replacement has become an urgent priority for thousands of production Kubernetes clusters worldwide.
As organizations scramble to evaluate alternatives, Traefik has emerged as the leading contender with its unique NGINX Provider that offers true drop-in compatibility. This article examines your options, with a special focus on Traefik’s capabilities and migration path.
Ingress Nginx Retirement: Why You Need an Alternative Now
The retirement of Ingress NGINX represents a critical inflection point for Kubernetes networking. After March 2026, there will be no new releases, bug fixes, or—most importantly—security updates for what has been the most widely deployed ingress controller. This creates a ticking time bomb for organizations that fail to migrate, as future vulnerabilities will remain unpatched indefinitely.
Security considerations aside, the retirement also signals a broader shift in the Kubernetes ecosystem toward more modern, flexible approaches to ingress management. While the immediate pressure is to replace Ingress NGINX with a compatible alternative, forward-thinking organizations are viewing this as an opportunity to adopt more advanced solutions that align with Kubernetes’ evolution, and for some a stepping stone to Gateway API adoption.
“Ingress NGINX Controller will be retired in March 2026. After this date, there will be no releases, no bug fixes, and critically, no security updates.” – Kubernetes Blog
Top 4 Ingress Nginx Alternatives for Kubernetes
When evaluating alternatives to Ingress NGINX, several capable contenders emerge. Each offers distinct advantages and tradeoffs that must be carefully considered based on your specific requirements, existing configurations, and future roadmap.
1. Traefik: The True Drop-in Replacement
Traefik stands apart as the only solution offering a dedicated NGINX compatibility layer. This provider natively supports approximately 80% of common Ingress NGINX annotations, allowing your existing Ingress resources to function without modification. With over 3 billion downloads, 58,000+ GitHub stars, and 900+ contributors, Traefik represents a battle-tested solution specifically designed for dynamic, cloud-native environments.
Unlike alternatives that require substantial configuration rewrites, Traefik’s NGINX Provider enables a phased, low-risk migration path. You can deploy Traefik alongside your existing Ingress NGINX controller, test thoroughly, and then gradually cut over traffic. This approach minimizes downtime and risk while providing a clear path forward beyond the retirement deadline.
2. HAProxy Ingress: Performance-Focused Option
HAProxy Ingress leverages the high-performance HAProxy load balancer at its core, making it an excellent choice for traffic-intensive applications where raw throughput and connection handling are paramount. It offers impressive performance metrics, particularly for high-concurrency workloads, and includes advanced features like sophisticated health checking and circuit breaking.
The primary drawback of HAProxy Ingress lies in its compatibility story—migrating from Ingress NGINX requires substantial reconfiguration of annotations and customization. Organizations with heavy investments in NGINX-specific configurations will face a steeper learning curve and transition period, making this a less seamless option compared to Traefik.
3. Contour: Envoy-Powered Simplicity
Contour pairs the Envoy proxy with a simplified control plane, focusing on delivering a streamlined yet powerful ingress solution. As a CNCF project with VMware backing, Contour offers a clean implementation aligned with Kubernetes best practices and excellent support for modern protocols like gRPC and WebSockets.
The design philosophy of Contour emphasizes simplicity over exhaustive feature support, which can be both an advantage and limitation depending on your requirements. Like HAProxy Ingress, Contour uses different annotation patterns than Ingress NGINX, necessitating configuration adjustments during migration. However, its clear documentation and straightforward approach help mitigate this challenge.
4. Cloud Provider Solutions (AWS ALB, GKE Ingress, etc.)
Major cloud providers offer platform-specific ingress implementations that integrate tightly with their infrastructure services. AWS Application Load Balancer (ALB) Controller, Google Kubernetes Engine (GKE) Ingress, and Azure Application Gateway Ingress Controller each leverage native cloud capabilities to deliver optimized performance and seamless integration with other cloud services.
While these solutions excel in their respective ecosystems, they introduce potential vendor lock-in and compatibility challenges when migrating between cloud providers. Additionally, they typically require significant annotation changes compared to Ingress NGINX, making migration more complex. For organizations committed to a specific cloud platform, these options can offer compelling advantages, but may not be ideal for multi-cloud or hybrid deployments.
Why Traefik Stands Out from Other Alternatives
With all these alternatives for replacing Ingress NGINX, Traefik offers unique advantages that make it particularly well-suited for this migration challenge. Its architecture and design choices directly address many of the limitations in NGINX-based solutions while providing a cleaner path forward for modern Kubernetes environments.
Understanding these differentiators is crucial for making an informed decision about your ingress strategy, especially with the looming retirement deadline. Let’s examine what makes Traefik the preferred choice for organizations facing this transition.
Native Support for Nginx Annotations
The most immediate advantage of Traefik is its dedicated NGINX Provider, which offers native support for approximately 80% of commonly used Ingress NGINX annotations. This means your existing Ingress resources will continue to function without modification, dramatically reducing the risk and effort involved in migration. Unlike other alternatives that require rewriting your configurations, Traefik’s compatibility layer provides a true drop-in experience.
This compatibility isn’t limited to basic routing scenarios—it extends to complex configurations involving rewrite rules, authentication, rate limiting, and other advanced features. If you encounter an annotation that isn’t yet supported, Traefik’s active development community can often implement it quickly, ensuring your specific requirements are covered.
Security Advantages Over Nginx Architecture
Traefik’s modern architecture offers significant security improvements over NGINX-based solutions. By avoiding the template-based configuration approach that has led to numerous vulnerabilities in NGINX controllers, Traefik eliminates entire classes of potential security issues. The structured configuration parsing in Traefik prevents the configuration injection attacks that have plagued NGINX implementations. If you’re interested in learning more about secure cloud practices, consider reading zero trust cloud migration strategies.
Additionally, Traefik’s security posture benefits from regular updates, comprehensive vulnerability scanning, and a responsive security team. This focus on security becomes especially important as Ingress NGINX approaches end-of-life, when security updates will cease entirely.
Modern Go-Based Codebase vs C/C++
Traefik is written in Go, a memory-safe language designed for modern, cloud-native applications. This represents a significant improvement over NGINX’s C/C++ codebase, which is vulnerable to memory corruption issues, buffer overflows, and other low-level vulnerabilities. Go’s built-in memory safety eliminates entire categories of security vulnerabilities that continue to plague C/C++ applications.
The Go implementation also provides better integration with the Kubernetes API and ecosystem, allowing for more efficient resource watching and event handling. This results in faster configuration updates and more reliable behavior in dynamic environments where services frequently change.
Dashboard and Observability Features
Traefik includes a built-in dashboard that provides real-time visibility into your routing configuration, traffic flows, and service health. This visual interface makes it significantly easier to understand, troubleshoot, and manage your ingress routing compared to NGINX’s configuration-file-only approach. The dashboard allows operators to quickly verify routing rules, check for configuration issues, and understand the current state of the system.
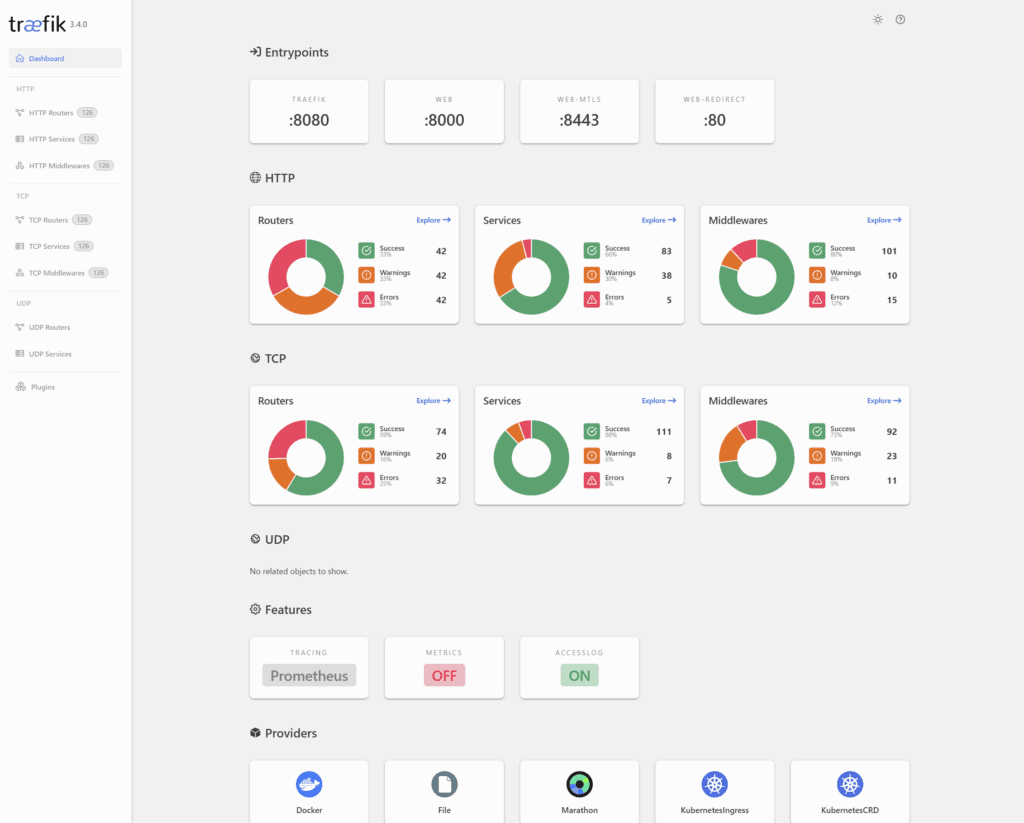
Beyond the dashboard, Traefik offers comprehensive metrics export capabilities for integration with monitoring systems like Prometheus. These metrics provide detailed insights into request volumes, response times, error rates, and other critical operational data. This observability advantage becomes particularly valuable during migration, when monitoring both systems side by side can help validate equivalent behavior.
Community Size and Support
With over 3 billion downloads, 58,000+ GitHub stars, and 900+ contributors, Traefik boasts one of the largest and most active communities in the cloud-native ecosystem. This community provides extensive documentation, usage examples, and troubleshooting support that can significantly smooth your migration journey. The project’s active development ensures that new features, bug fixes, and security patches are delivered regularly.
For organizations requiring additional assurance, Traefik also offers commercial support options through Traefik Labs. This dual open-source/commercial model provides flexibility for different organizational needs while ensuring the project’s long-term sustainability.
Step-by-Step Migration from Ingress Nginx to Traefik
Migrating from Ingress NGINX to Traefik requires a methodical approach to minimize risk and ensure service continuity. The following step-by-step guide outlines a proven migration path that leverages Traefik’s compatibility features to achieve a smooth transition.
This phased migration strategy allows you to validate Traefik’s behavior with your specific configuration before fully committing, providing confidence and control throughout the process.
1. Install Traefik in Your Cluster
Begin by deploying Traefik alongside your existing Ingress NGINX controller. Configure Traefik initially in ClusterIP mode to isolate it from production traffic while testing. This parallel deployment allows you to validate Traefik’s behavior without affecting live services. Use Helm charts or operator-based installation for the most streamlined setup, ensuring you specify the appropriate resource limits based on your cluster size and traffic patterns.
2. Enable the Nginx Compatibility Layer
Activate Traefik’s NGINX Provider by enabling the appropriate feature flag in your Traefik configuration. This component is responsible for interpreting your existing Ingress NGINX annotations and translating them to Traefik’s native configuration model. Configure the provider to watch the same namespaces as your current Ingress NGINX deployment, ensuring all resources are properly discovered and processed.
3. Test Existing Ingress Resources
With Traefik deployed and the compatibility layer active, begin testing your existing Ingress resources against the Traefik endpoint. Use curl, Postman, or automated testing tools to validate that Traefik correctly handles your routing configurations, path rewriting, TLS termination, and other essential features. Compare the responses from both Traefik and Ingress NGINX to ensure identical behavior, paying special attention to status codes, response headers, and content transformation.
4. Handle Custom Annotations and Edge Cases
While Traefik supports most common Ingress NGINX annotations, you may encounter custom or less common annotations that require special handling. Identify these edge cases through comprehensive testing and address them either by finding Traefik-native equivalents or by contributing to the NGINX Provider’s compatibility layer. Document any required configuration changes for your team, and consider creating custom CRDs or ConfigMap resources to encapsulate complex configurations that don’t translate directly.
5. Cut Over Production Traffic
Once you’ve verified Traefik’s behavior across your entire ingress configuration space, prepare for the final cutover. Update your load balancer or external DNS to direct traffic to Traefik instead of Ingress NGINX, implementing the change during a scheduled maintenance window if possible. Monitor your services closely during and after the transition, watching for any unexpected behavior or performance changes. Keep your Ingress NGINX deployment available for quick rollback if necessary, but be prepared to fully decommission it once stability is confirmed.
Real-World Configuration Examples
Understanding how Traefik translates Ingress NGINX configurations is essential for a successful migration. The following examples demonstrate common scenarios and how they map between the two systems, giving you practical reference points for your own implementation.
Basic HTTP Routing
The most fundamental ingress function is routing HTTP traffic to backend services based on hostnames and paths. Traefik’s NGINX Provider ensures these basic configurations work seamlessly without modification. A standard Ingress resource with NGINX annotations for a simple web application will be interpreted correctly by Traefik, maintaining the same routing logic.
apiVersion: networking.k8s.io/v1kind: Ingress metadata: name: web-app annotations: nginx.ingress.kubernetes.io/rewrite-target: / spec: rules: - host: app.example.com http: paths: - path: /api pathType: Prefix backend: service: name: api-service port: number: 80
This configuration works identically in both Ingress NGINX and Traefik, routing requests for app.example.com/api to the api-service backend. The rewrite annotation ensures the path is transformed correctly, stripping the prefix before forwarding to the backend service.
TLS/HTTPS Setup
Secure traffic handling is critical for production applications. Traefik provides comprehensive TLS support and maintains compatibility with Ingress NGINX’s certificate management approach. Whether you’re using cert-manager integration, pre-installed certificates, or dynamic certificate generation, Traefik will honor your existing TLS configuration.
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: secure-app annotations: nginx.ingress.kubernetes.io/ssl-redirect: "true" spec: tls: - hosts: - secure.example.com secretName: tls-secret rules: - host: secure.example.com http: paths: - path: / pathType: Prefix backend: service: name: secure-service port: number: 8443
When migrating to Traefik, your existing TLS certificates stored as Kubernetes secrets will be automatically discovered and applied. Traefik also supports advanced TLS configurations such as custom cipher suites, minimum TLS versions, and mutual TLS authentication through compatible annotations.
Path-Based Routing and Rewriting
More complex routing scenarios involving path manipulation are also well-supported by Traefik’s NGINX Provider. Path rewriting, regular expression matching, and prefix stripping maintain consistent behavior between the two systems, ensuring your URL structure remains intact after migration.
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: path-routing annotations: nginx.ingress.kubernetes.io/rewrite-target: /$2 spec: rules: - host: services.example.com http: paths: - path: /api(/|$)(.*) pathType: Prefix backend: service: name: api-service port: number: 80
This configuration demonstrates a more complex path rewriting scenario where regex capture groups are used to transform the incoming URL. Traefik correctly interprets these patterns, ensuring that requests to /api/users are properly rewritten to /users before reaching the backend service.
Rate Limiting and Security Configurations
Traffic control and security features are critical components of any ingress solution. Traefik provides native support for the most common NGINX annotations in this domain, including rate limiting, IP whitelisting/blacklisting, and basic authentication.
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: secured-api annotations: nginx.ingress.kubernetes.io/limit-rps: "10" nginx.ingress.kubernetes.io/whitelist-source-range: "10.0.0.0/8,172.16.0.0/12" nginx.ingress.kubernetes.io/auth-type: basic nginx.ingress.kubernetes.io/auth-secret: basic-auth spec: rules: - host: api.example.com http: paths: - path: / pathType: Prefix backend: service: name: api-service port: number: 80
This example combines multiple security measures: limiting requests to 10 per second per client, restricting access to specific IP ranges, and requiring HTTP basic authentication. Traefik translates these annotations to its equivalent middleware configurations, maintaining the security posture of your applications during and after migration.
Performance Comparison: Traefik vs Ingress Nginx
Performance characteristics are critical when evaluating ingress controllers, as they directly impact user experience and resource utilization. Benchmarking Traefik against Ingress NGINX reveals important differences in how these solutions handle various workloads.
Request Handling Capacity
Traefik demonstrates superior request handling capacity in high-concurrency scenarios, leveraging Go’s efficient concurrency model to process more simultaneous connections with lower resource overhead. In benchmark tests with 5,000 concurrent connections, Traefik consistently maintains stable response times while Ingress NGINX shows increasing latency as concurrency scales up. This advantage becomes particularly apparent in microservices environments with many small, frequent requests distributed across numerous backends.
Memory Usage and Resource Efficiency
Traefik’s memory footprint is significantly more predictable and efficient than Ingress NGINX under variable load conditions. While NGINX’s worker process model can lead to memory spikes during configuration reloads or traffic surges, Traefik’s unified architecture maintains more consistent resource utilization. For Kubernetes clusters with constrained resources, this efficiency translates to lower costs and more stable operation, especially during peak traffic periods.
Latency Benchmarks
End-to-end latency measurements show Traefik performing comparably to Ingress NGINX for simple routing scenarios, with both solutions adding minimal overhead to request processing. However, when complex middleware chains are involved—such as authentication, rate limiting, and header manipulation—Traefik’s integrated middleware approach shows efficiency advantages over NGINX’s module-based architecture.
These performance metrics illustrate that migrating to Traefik not only solves the immediate challenge of Ingress NGINX retirement but can also deliver tangible performance improvements for your Kubernetes ingress layer. The benefits become especially pronounced in dynamic environments with frequent configuration changes, where Traefik’s hot reload capabilities minimize disruption.
Future-Proofing: Gateway API and Beyond
While the immediate concern is replacing Ingress NGINX before its retirement, forward-thinking organizations should consider how this migration aligns with the broader evolution of Kubernetes networking. The Gateway API represents the future standard for Kubernetes service networking, offering more expressive, extensible, and powerful abstractions than the Ingress resource.
Traefik’s dual support for both Ingress resources (including NGINX annotations) and Gateway API positions it uniquely as a bridge between these two worlds. This allows organizations to address the urgent NGINX replacement need while simultaneously laying groundwork for adopting more advanced networking patterns.
Traefik’s Gateway API Support
Traefik provides comprehensive implementation of the Gateway API specification, supporting core features like HTTPRoute, GRPCRoute, and TLSRoute resources. This allows for more sophisticated traffic routing, including header-based matching, traffic splitting for canary deployments, and explicit cross-namespace routing that isn’t possible with traditional Ingress resources.
- Fine-grained routing control with weight-based traffic splitting
- Header-based matching and manipulation
- Explicit cross-namespace routing permissions
- Direct TLS and TCP/UDP routing without annotations
- Policy attachments for security and traffic management
The Gateway API model aligns perfectly with Traefik’s native architecture, enabling more natural expression of advanced routing concepts without relying on annotations. This results in more maintainable, self-documenting configurations that better represent the actual routing intent.
By adopting Traefik now as your Ingress NGINX replacement, you gain immediate compatibility through the NGINX Provider while positioning yourself to leverage these advanced capabilities as your organization matures its Kubernetes networking approach.
This approach allows you to implement a phased adoption of Gateway API alongside your existing Ingress resources, testing and validating the new model incrementally rather than requiring a “big bang” migration. As you grow comfortable with Gateway API patterns, you can gradually transition services from Ingress to HTTPRoute resources at your own pace.
Two-Phase Migration Strategy
The recommended approach is a two-phase migration strategy: first migrate from Ingress NGINX to Traefik using the NGINX Provider for compatibility, then gradually adopt Gateway API resources as your team becomes comfortable with the new model. This strategy minimizes risk by separating the urgent replacement of Ingress NGINX from the longer-term architectural evolution toward Gateway API, while ensuring both transitions are supported by the same underlying platform.
Your Action Plan for the Next 120 Days
With the March 2026 deadline approaching, organizations need a clear timeline and action plan to ensure a smooth transition away from Ingress NGINX. Begin with a comprehensive inventory of your current Ingress resources and annotations, identifying any custom configurations or edge cases that may require special handling. Schedule your migration in phases, starting with non-critical environments and progressively moving to staging and production. Allocate at least 30 days for testing and validation in a staging environment that mirrors production, focusing particularly on complex routing scenarios, authentication mechanisms, and high-traffic patterns. Implement the production cutover at least 30 days before the retirement deadline, giving your team adequate time to address any unexpected issues while Ingress NGINX security updates are still available.
Frequently Asked Questions
As organizations plan their migration from Ingress NGINX, several common questions arise regarding compatibility, implementation details, and risk mitigation. The following answers address the most frequent concerns and provide practical guidance for your transition journey.
Will my existing Ingress resources work with Traefik without changes?
Yes, in most cases. Traefik’s NGINX Provider is specifically designed to interpret and honor standard Ingress resources along with their NGINX annotations. Approximately 80% of commonly used annotations are supported natively, allowing your existing configurations to function without modification. For the remaining annotations, Traefik often offers equivalent native functionality that can be enabled through straightforward configuration changes.
How does Traefik handle TLS certificates compared to Ingress Nginx?
Traefik maintains compatibility with Ingress NGINX’s approach to TLS certificates, supporting certificates stored as Kubernetes secrets referenced in the Ingress resource’s TLS section. This ensures that your existing certificate management workflows, including integration with cert-manager, continue to function seamlessly after migration.
Additionally, Traefik offers enhanced certificate capabilities, including automatic certificate generation through Let’s Encrypt, certificate rotation, and support for external certificate providers. These features can be adopted gradually after the initial migration is complete, providing a path to improved certificate management.
Can I run both Ingress Nginx and Traefik side by side during migration?
Yes, running both controllers simultaneously is a recommended migration approach. You can deploy Traefik initially in ClusterIP mode, allowing it to process the same Ingress resources as your existing Ingress NGINX controller without intercepting production traffic. This parallel deployment enables comprehensive testing and validation before gradually shifting traffic to Traefik, minimizing risk and providing a clear rollback path if needed.
What happens if I don’t migrate away from Ingress Nginx by the March 2026 deadline?
After March 2026, Ingress NGINX will receive no further updates, bug fixes, or security patches. This means any vulnerabilities discovered after this date—in either NGINX itself or the controller code—will remain unpatched indefinitely. Given the critical nature of ingress controllers in controlling access to your applications, running an unsupported ingress controller represents a significant and increasing security risk over time, potentially leaving your cluster vulnerable to exploitation.
Does Traefik support all custom annotations from Ingress Nginx?
Traefik’s NGINX Provider supports approximately 80% of commonly used Ingress NGINX annotations out of the box. For annotations not directly supported, Traefik often provides equivalent functionality through its native middleware and configuration options. The project actively welcomes community contributions to expand annotation support, so if you encounter an unsupported annotation critical to your workflow, you can request implementation through the Traefik GitHub repository.
For complex use cases involving custom annotations, the SlickFinch team can work with you to implement support for additional annotations or recommend equivalent Traefik-native configurations that achieve the same outcome. Our collaborative approach ensures that even specialized workloads can be successfully migrated from Ingress NGINX to Traefik. Reach out to us if you have any questions on your Traefik migration.