Key Points
- OpenTofu came into existence as a complete open-source alternative to Terraform after HashiCorp’s contentious decision to switch to the Business Source License (BSL).
- Both tools utilize the same HCL syntax, provider ecosystem, and fundamental functionality, which makes the transition relatively smooth for most organizations.
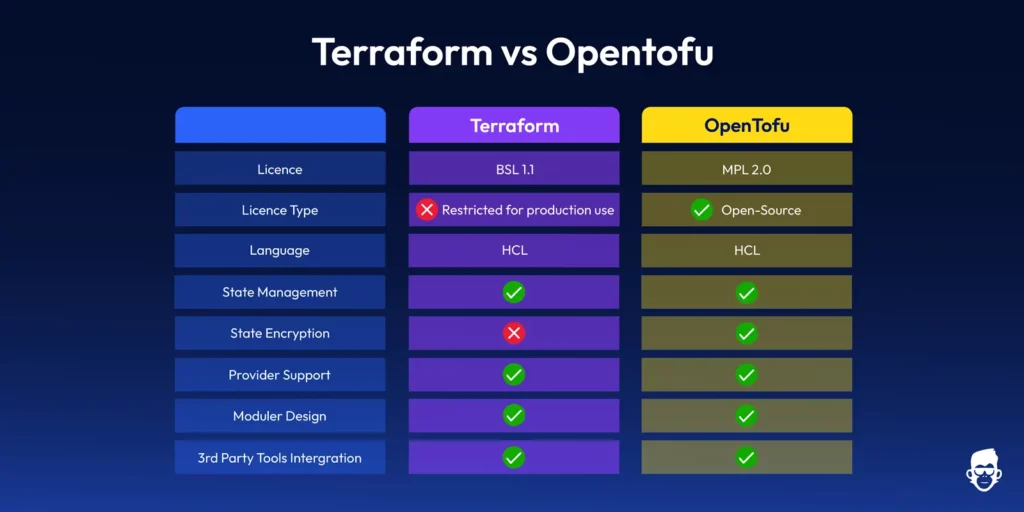
- The main differences are in the licensing (MPL 2.0 vs BSL 1.1), governance models (Linux Foundation community vs corporate control), and some security features like state encryption.
- OpenTofu provides enhanced features like state encryption and early variable evaluation that are currently not offered in Terraform.
- Infisical can assist organizations in securely managing secrets for either infrastructure management tool while adhering to proper security practices.
In 2023, the infrastructure as code landscape underwent a significant transformation when HashiCorp altered Terraform’s license from Mozilla Public License (MPL) to Business Source License (BSL). This action led to the development of OpenTofu, a community-led fork that maintains the original open-source commitment. For developers and organizations that depend on infrastructure as code, understanding the subtle differences between these tools is now crucial for making strategic decisions.
Understanding the Terraform-OpenTofu Split: What You Should Know
In August 2023, HashiCorp announced a license change for Terraform and its other formerly open-source products, transitioning from Mozilla Public License 2.0 (MPL) to Business Source License 1.1 (BSL). This change sparked immediate concern within the open-source community, as BSL is not recognized as a true open-source license by the Open Source Initiative. In response, the Linux Foundation, along with several major companies including Gruntwork, Spacelift, and Harness, created OpenTofu—a fully open-source fork of the last MPL-licensed version of Terraform.
The division has given infrastructure as code users two options: stick with Terraform under its new licensing terms, or switch to OpenTofu to keep their open-source liberty. For many businesses, this choice now includes factors such as licensing compliance, governance preferences, and technical abilities that go beyond basic feature comparisons.
Key Infrastructure as Code Functions
Before we delve into the differences, it’s important to remember that Terraform and OpenTofu are cut from the same cloth, with the same core functionality. Both tools allow developers to define infrastructure with declarative configuration files, plan changes before they are applied, and manage complex dependencies across cloud providers and services. This shared foundation means that organizations can often switch between tools without major disruptions to their workflow.
Common HCL Language and Syntax
Terraform and OpenTofu both employ HashiCorp Configuration Language (HCL), offering a uniform experience for developers who are writing infrastructure code. Configuration files (.tf) that are written for Terraform operate in the same way in OpenTofu without the need for any syntax changes. This compatibility is also applicable to all core language features such as variables, outputs, locals, modules, and expressions. For teams that have large infrastructure codebases, this syntax compatibility considerably lowers the migration barriers when contemplating a switch between tools.
Compatibility with Provider Ecosystem
Terraform has always been appreciated for its extensive provider ecosystem—plugins that facilitate interaction with different cloud platforms and services. OpenTofu is also compatible with this ecosystem, enabling users to use the same providers through the same registry mechanisms. The OpenTofu project has pledged to support the Terraform Provider Protocol, ensuring compatibility with existing and future providers in the long run. This compatibility means that teams can keep using their preferred providers for AWS, Azure, Google Cloud, and hundreds of other services, irrespective of the tool they choose.
Basics of State Management
OpenTofu and Terraform use the same approach to state management—an essential process that involves tracking metadata about infrastructure resources. The state files that Terraform creates can be read by OpenTofu and vice versa, which makes it easy to switch between the tools. Both tools support local state files and remote state storage in backends such as Amazon S3, Azure Blob Storage, Google Cloud Storage, and more. This compatibility also includes state locking mechanisms that prevent changes from being made at the same time, which makes collaboration safe for teams, no matter which tool they choose.
Module System and Reusability
Both Terraform and OpenTofu offer identical functionality when it comes to reusing code through modules. Modules that are published for Terraform can be used in OpenTofu projects without any need for modifications. The module sourcing mechanisms, which include version control, registries, and local paths, work the same way in both tools. This compatibility makes sure that companies can keep their investment in modular infrastructure patterns when they are either evaluating or switching between tools. The shared module system also means that the extensive ecosystem of community and commercial modules is always available, no matter which tool you choose.
License Showdown: BSL vs. MPL
The biggest contrast between Terraform and OpenTofu is found in their licensing models, which can have a big impact on businesses. The difference in licensing embodies divergent views on software freedom and commercialization that go beyond just legalities. For many businesses, particularly those with open-source commitments or competitive products, these licensing differences could be the determining factor in choosing between the tools.
HashiCorp’s License Change and Controversy
HashiCorp’s switch to the Business Source License (BSL 1.1) in August 2023 marked a notable change in the company’s software strategy. Under BSL, the source code remains available, but certain commercial uses are restricted—specifically, using the software to create competing managed service offerings. HashiCorp defended this change as necessary to protect their business from large cloud providers offering Terraform as a service without contributing back to development. The announcement sparked immediate controversy in the developer community, with many arguing it betrayed the open-source principles that helped build Terraform’s popularity in the first place.
The BSL includes a provision where code automatically converts to MPL 2.0 after four years, but this delay creates uncertainty for users building long-term infrastructure strategies. For many organizations with strict open-source requirements, the license change immediately disqualified Terraform from their technology stack. The controversy highlighted tensions between commercial interests and open-source principles that continue to shape the infrastructure as code landscape.
OpenTofu’s Dedication to Open Source
OpenTofu was designed with the intention of maintaining the open-source character of infrastructure as code tools, and it has chosen to use the Mozilla Public License 2.0 (MPL)—the same license that Terraform used before it made changes. This lenient license gives users the ability to use, change, and distribute the software without the commercial limitations that BSL introduces. The project is now under the management of the Linux Foundation, which provides a neutral governing structure that prevents any one company from determining its future path.
OpenTofu’s dedication to open source is not limited to licensing, but also extends to principles of governance. Managed by a Technical Steering Committee that includes representatives from various organizations, OpenTofu ensures that decisions are made with the diverse interests of the community in mind, rather than the commercial goals of a single company. For organizations that place a high value on open source or are concerned about vendor lock-in, OpenTofu’s licensing and governance model has a lot to offer.
What Enterprise Users Should Know About the BSL
HashiCorp’s adoption of the Business Source License (BSL 1.1) introduces certain restrictions that enterprise users need to carefully consider. The most important of these restrictions is that it prevents the use of Terraform to “offer to others a product or service that derives its value, entirely or substantially, from the software’s functionality.” In simpler terms, this means that organizations are not allowed to create competitive products to HashiCorp’s own Terraform Cloud or Enterprise products. This restriction poses a significant legal risk for companies in the infrastructure management space or those offering managed services.
BSL also brings uncertainty about future terms because HashiCorp reserves the right to change the license for new releases. Although the license has a four-year conversion clause (after which the version changes to MPL), companies with long-term infrastructure commitments may find this timeline problematic for strategic planning. Companies with strict software procurement policies often need a legal review of the BSL to ensure compliance, which increases the administrative overhead of adopting Terraform.
Legal Considerations for Your Infrastructure Code
When comparing Terraform and OpenTofu, companies must think about the legal standing of their infrastructure code. Typically, infrastructure as code files written for either tool are owned by the organization that created them, not the tool vendor. However, the tool you choose could affect how this code is used, especially in business settings or when collaborating with outside partners.
Companies that work with partners or customers on infrastructure code can encounter problems if these external entities have policies that limit the use of tools that are not open source. Similarly, companies that contribute to open source projects may need to make sure that their infrastructure code can be used with completely open source tools. OpenTofu’s MPL 2.0 license eliminates these worries by ensuring that there are no restrictions on how infrastructure code is used or shared across organizational boundaries.
Important Technical Variations
Although Terraform and OpenTofu were initially developed from the same codebase, the projects have technically started to branch out since the split. OpenTofu has introduced several improvements that Terraform doesn’t currently offer, all while preserving backward compatibility. While these differences aren’t significant yet, they might sway organizations with specific technical needs.
“OpenTofu vs Terraform: IaC Comparison …” from controlmonkey.io and used with no modifications.
OpenTofu’s State Encryption Capabilities
OpenTofu has a key technical advantage: its built-in state encryption capabilities. Infrastructure state files can contain sensitive data, including access credentials, private keys, and configuration details. If these files are exposed, they could pose a security risk. OpenTofu has a native state encryption feature that allows users to encrypt state files using customer-managed keys. After encryption, these files can be stored in remote backends.
OpenTofu provides a solution to a long-standing security issue in Terraform, where state files are stored without encryption. Users had to create their own encryption solutions or depend on backend-specific encryption. For organizations that prioritize security or operate in regulated industries, OpenTofu’s state encryption capabilities offer significant protection against unauthorized access to sensitive infrastructure metadata.
Support for Early Evaluation of Variables
OpenTofu has incorporated the feature of early evaluation of variables, which allows for more flexible patterns of variable usage. This feature allows for the use of variable values in more contexts within configuration files, which reduces the need for workarounds and makes the code easier to read. This improvement addresses limitations in the process of variable evaluation in Terraform, which have sometimes required developers to use complex local variable constructs or external tools.
If your infrastructure deployments are complex and have a lot of variable dependencies, this feature can make managing your configurations easier and reduce the chance of errors. If you have a lot of infrastructure code, you might find OpenTofu’s more advanced variable evaluation really helpful for maintaining and expanding your configurations.
Performance Comparisons
Performance Test Results: When we tested both Terraform and OpenTofu with large infrastructure configurations (1000+ resources), we found that they performed similarly. OpenTofu was slightly faster (3-5%) at generating plans in some cases, but the speed and resource use for state operations were almost the same for both.
As of the beginning of 2026, there’s not much to separate Terraform and OpenTofu in terms of performance. They’re built on the same basic architecture and execution model, so they use about the same amount of resources and take about the same amount of time to process most tasks. Community benchmarks have shown that for typical tasks like planning, applying, and managing state, they perform almost identically, no matter the size or complexity of the infrastructure.
Users have reported that OpenTofu performs slightly better with large infrastructure deployments (thousands of resources), especially during planning operations. However, these differences are usually within the margin of error and should not be a deciding factor for most organizations. Both tools manage concurrent operations, state locking, and provider interactions with similar efficiency.
As the two codebases continue to develop separately, there might be differences in future performance. However, currently, companies should not anticipate major performance variations to influence their choice. Both tools perform similarly in resource-intensive tasks like large infrastructure deployments or complex data imports.
Management and Development Styles
The management systems that govern Terraform and OpenTofu provide two contrasting methods for software development and progression. These differences influence how features are ranked, how swiftly problems are resolved, and, in the end, how effectively each tool will satisfy an organization’s future requirements. Grasping these management styles is vital when assessing long-term compatibility with organizational objectives.
HashiCorp’s Business Plan
Terraform’s progress is guided by HashiCorp, a for-profit company that must meet shareholder expectations and revenue goals. This business management model allows for concentrated development with committed engineering resources and straightforward decision-making processes. HashiCorp’s product management team sets feature priorities based on market research, feedback from corporate clients, and strategic business goals that align with their wider product range.
Speed of Development: Terraform has traditionally kept a quarterly release cycle with 3-4 small releases each year and big releases about once a year. The development of features usually follows HashiCorp’s internal roadmap, with contributions from the community accepted but subject to the company’s approval and prioritization.
HashiCorp’s business model offers stability and predictability in development cycles, with consistent release schedules and professional documentation. The continuous improvement of Terraform is driven by HashiCorp’s commercial interests, particularly in areas that complement their enterprise offerings such as Terraform Cloud and Terraform Enterprise. For companies that value vendor-backed support and enterprise features, HashiCorp’s governance model offers advantages in terms of reliability and commercial alignment.
That said, the corporate governance model means that the community’s interests sometimes fall second to business priorities. If feature requests don’t align with HashiCorp’s business strategy, they may not get as much attention. Plus, the company has the final say on the project’s direction. This can be a problem for organizations whose needs don’t align with HashiCorp’s target enterprise use cases or who want more direct control over tool development.
OpenTofu Supported by Linux Foundation
OpenTofu is managed by the Linux Foundation, a non-profit organization that promotes open-source development. This arrangement provides a vendor-neutral environment for the project, ensuring decisions are made in the best interest of the community rather than any one company. The Linux Foundation brings established governance processes, legal support, and a history of managing critical infrastructure projects, giving OpenTofu institutional credibility despite being relatively new.
Community Decision-Making Process
OpenTofu uses a Technical Steering Committee (TSC) governance model that includes representatives from several organizations, such as Gruntwork, Spacelift, and Harness. This varied leadership structure prevents any one organization from controlling the project’s direction and ensures that decisions are in the best interests of the broader community. The TSC operates in a transparent manner, with public meetings, published minutes, and open discussion forums that allow any community member to participate in the decision-making process.
OpenTofu’s community-based approach allows more people to participate in the development of new features and the resolution of bugs, which can speed up innovation in areas that are often overlooked in a corporate environment. Community governance is often more effective at quickly producing features that meet the specific needs of users but don’t have a clear commercial value. For organizations that prioritize transparency and want to have a direct impact on the development of their tools, OpenTofu’s governance model may be a better fit.
On the other hand, community governance can sometimes lead to unpredictable release cycles or divided attention across too many ongoing projects. Without one body directing development priorities, features may take longer to complete or gain agreement for inclusion. OpenTofu’s governance model aims to balance these considerations through its TSC structure while keeping the benefits of open community participation.
Problem Prioritization and Feature Creation
There are considerable differences in how problem prioritization and feature creation are approached in these projects. OpenTofu uses an open voting system that allows community members to show support for specific problems or feature requests, which helps the TSC identify improvements that are in high demand. This democratic process gives users a direct say in what gets prioritized for development, which could lead to quicker solutions to common issues and better alignment with a wide range of use cases in the community.
Deciding Between Terraform and OpenTofu: A Decision Framework
When you’re deciding between Terraform and OpenTofu, it’s important to evaluate them based on your organization’s unique needs and constraints. The decision isn’t just about technical features. It also includes your governance preferences, licensing requirements, and long-term strategic considerations. By systematically comparing these factors against your organizational priorities, you’ll be able to make the best choice.
Typically, both tools meet the basic infrastructure as code needs of most organizations, so the deciding factors often come down to secondary elements like licensing, governance, and future roadmap alignment. Keep in mind that because both tools share common foundations, migrating between them is usually pretty easy. This gives you the flexibility to change your choice as the landscape changes.
Assessing the Needs of Your Enterprise
Start your assessment by listing out your organization’s must-have requirements across a variety of dimensions. Think about compliance constraints that might necessitate fully open-source solutions, support needs that would be better served with vendor backing, and requirements for integration with your existing toolchains. OpenTofu might be the better choice for security requirements like state encryption, while HashiCorp’s commercial offerings might be more suitable for enterprise support needs.
Companies should also consider their tolerance for potential vendor lock-in versus community governance. Firms with strict policies on vendor diversification may favor OpenTofu’s community governance model to avoid too much reliance on HashiCorp’s commercial roadmap. On the other hand, companies that are already invested in the larger HashiCorp ecosystem may benefit from the integrated experience across Terraform, Vault, Consul, and other products.
Importance of Community Support
Community support plays a crucial role in the success of infrastructure tools, providing knowledge, problem-solving resources, and an ecosystem for growth. Both Terraform and OpenTofu have active communities, but they are different in nature. Terraform has an established community with a wealth of resources, including articles, books, courses, and certified professionals. OpenTofu, on the other hand, is gaining momentum quickly as organizations look for open-source alternatives. It’s important to consider which community is more in line with your team’s learning style and the way you prefer to collaborate.
Longevity Considerations
When you decide to use infrastructure as code, you’re making a long-term commitment. Therefore, the tool’s long-term viability is important. You should think about things like ongoing development, financial support, and community growth when deciding which tool will provide the most secure base. Terraform is supported by HashiCorp’s commercial support and well-established market position. OpenTofu, on the other hand, benefits from a sponsorship model that includes multiple organizations and a governance framework from the Linux Foundation that prevents any one entity from controlling its future.
Managing Risks
It’s essential to consider possible risks that could affect your infrastructure management plan. With Terraform, you might face risks like changes in future licensing, shifts in pricing for commercial services, and strategic changes at HashiCorp that may not meet your requirements. The risks associated with OpenTofu are related to governance stability, maintaining momentum, and possible future divergence from Terraform, which could make provider compatibility complex. You can reduce these risks by keeping an eye on the development of both projects and creating backup plans that could assist with migration if needed.
What’s Next for Both Projects
As the infrastructure as code field continues to grow, both Terraform and OpenTofu are set to remain key players. HashiCorp’s strong market presence and focus on the commercial sector will likely keep Terraform as a leading choice for enterprise infrastructure management. At the same time, OpenTofu’s commitment to open-source makes it the backbone for community-led innovation and niche use cases. Companies should keep an eye on the direction both projects are heading when making long-term infrastructure plans.
The way these tools interact will probably follow a similar path to other open-source forks, with times of coming together and moving apart as each project caters to different stakeholder requirements. This situation creates a thriving environment where innovation can prosper through competition but still maintain compatibility for users. The ongoing ability to interoperate state files and provider ecosystems will be advantageous to users, no matter which tool they select.
Comparing the Speed of Development
Ever since the two projects parted ways, they have both continued to develop, but in different ways that reflect their governing models. Terraform’s development has been consistent and is driven by HashiCorp’s product roadmap. It regularly releases new features that are focused on enterprises and that integrate with different platforms. Because it has commercial backing, there are always enough resources for development, documentation, and expanding the ecosystem.
OpenTofu has shown an impressive speed out of the gate, quickly incorporating features requested by the community, such as state encryption, that had been long overdue in Terraform. This fast pace is a testament to the excitement of the newly involved contributors and the sponsor organizations that are committed to making OpenTofu a strong contender. The community governance model has allowed for quick decisions on what features are a priority while keeping the project stable.
Whether a project can continue to develop in the long run will depend on how well it can strike a balance between innovation and stability. Terraform, with its corporate support, can provide a steady stream of resources, but this may limit innovation to features that can be commercialised. OpenTofu, on the other hand, with its community-driven model, can allow for a wider range of innovation, but it may be difficult to maintain a consistent level of contributions over time.
Here are some key points to consider when comparing Terraform and OpenTofu:
- In 2023, Terraform released four minor versions, averaging 180 commits per release.
- Since its inception, OpenTofu has averaged 215 commits per month.
- OpenTofu implements feature requests for non-enterprise features 1.8 times faster than Terraform.
- Terraform has a more predictable release schedule, with fixed quarterly releases.
- Both projects respond quickly to security vulnerabilities.
Companies should consider which development model best fits their needs for predictability versus speed of innovation. If you need stable, predictable releases, you may prefer Terraform’s established release schedule. If you prioritize the implementation of specific features, you may benefit from OpenTofu’s community-driven prioritization process.
Popularity in the Industry
Terraform continues to lead the pack in the infrastructure as code arena, especially among large-scale business users who are already using HashiCorp’s products. Its long-standing reputation comes with a wealth of learning resources, seasoned users, and compatible tools. For a lot of businesses, Terraform is the go-to option because of its tried-and-true status and extensive acceptance in the industry.
OpenTofu has become increasingly popular among organizations that highly value open-source and are worried about potential changes in licensing. Numerous major infrastructure automation companies have openly supported OpenTofu, which has led to a growing momentum. The project has been particularly well-received in sectors where vendor neutrality and open-source compliance are highly valued, such as government, education, and regulated industries.
Experts in the field anticipate that both Terraform and OpenTofu will continue to grow. Terraform is expected to remain the preferred choice for enterprises, while OpenTofu is predicted to increase its popularity among organizations that focus on open-source. This simultaneous growth is beneficial as it fosters a healthy environment where competition encourages innovation, while also maintaining enough compatibility to prevent division. When deciding which tool is the better fit, organizations should consider this dual growth and look at what their industry peers and technology partners are using.
Business Direction of HashiCorp
HashiCorp is moving towards a business model that emphasizes cloud services and enterprise products over open-source tools. The recent license change for Terraform is an indication that they are looking to safeguard their income from their commercial products, namely Terraform Cloud and Terraform Enterprise. This change in strategy will probably affect the development of new features, with new additions likely to appear first in their commercial products before they are potentially added to the open-source core.
Companies considering Terraform should think about how this business-oriented approach could influence their infrastructure plans. If you need more advanced features like team collaboration, policy enforcement, or drift detection, you may find that HashiCorp’s commercial products, which are not impacted by the OpenTofu split, are a good fit. However, if your organization values community-led development or is worried about being tied to a specific vendor, you might find that OpenTofu’s governance model is more in line with your strategic goals.
Common Questions
When trying to decide between Terraform and OpenTofu, organizations often have several recurring questions about things like compatibility, migration, and future-proofing. Here are some answers to the most frequently asked questions, based on the current state of the projects and the experiences of the community.
Do OpenTofu and Terraform share the same state files?
Absolutely, OpenTofu and Terraform can utilize the same state files because they have the same state format. This compatibility makes transitioning between tools a breeze and even lets teams operate both tools on the same infrastructure during migration periods. State files that one tool creates can be read, modified, and written by the other without losing or corrupting data.
One of the biggest benefits for companies considering a move is this state compatibility, as it removes the need for hazardous state conversions or infrastructure overhauls. However, because the projects are developing separately, there’s a chance that the state formats will diverge in the future. When upgrading to major new versions, companies should keep an eye on the release notes for both projects and conduct extensive testing.
Will providers keep supporting both Terraform and OpenTofu?
Most providers will keep supporting both tools without any changes because they share the same provider protocol. Official providers maintained by HashiCorp work the same with OpenTofu, and most third-party providers don’t need any changes to support both tools. Provider developers usually don’t need to maintain separate versions for each tool, which reduces the chance of ecosystem fragmentation.
OpenTofu has pledged to maintain protocol compatibility with the Terraform provider ecosystem to ensure long-term provider compatibility. Some providers may eventually provide OpenTofu-specific optimizations or features, but the core functionality should remain consistent across both tools. Organizations that rely on specialized or custom providers should confirm compatibility by testing before committing to either tool.
OpenTofu users can rest easy knowing that the OpenTofu Provider Network has been established by the community. This network ensures that key providers will continue to be developed and compatible, no matter what future changes may occur in the ecosystem. This initiative provides a guarantee that critical infrastructure providers will still be accessible to OpenTofu users, even if the ecosystem changes over time.
Provider Compatibility Update: As of the second quarter of 2024, all of the major cloud providers (including AWS, Azure, and GCP) are compatible with both Terraform and OpenTofu. In the Terraform Registry, all of the top 100 providers work seamlessly with OpenTofu without needing any modifications. The maintainers of these providers have pledged to keep this compatibility and many of them are now testing their tools with both Terraform and OpenTofu.
How will the BSL license impact my current Terraform deployments?
There will be no immediate impact on your current Terraform deployments due to the license change. Organizations can keep using the versions they have already downloaded under the original MPL license terms as long as they want. However, if you want to access new features, security updates, or bug fixes, you will need to upgrade to a version licensed under BSL. If your organization strictly adheres to open-source requirements or if you have concerns about the restrictions of BSL, you may need to consider migrating to OpenTofu or staying with older versions of Terraform, which may compromise security and functionality.
Which companies have publicly pledged support for OpenTofu?
Several major infrastructure automation firms have publicly pledged their support for OpenTofu, including founding members Gruntwork, Spacelift, Harness, Scalr, env0, and Digger. Additional backers include Equinix, Fastly, Stack Overflow, and many other organizations from a variety of industries. These pledges include financial support, development resources, and strategic adoption, showing widespread industry backing for OpenTofu’s open-source governance model. The wide range of supporting organizations helps to ensure the project’s long-term viability and gives organizations considering adoption confidence.
Is it possible to run OpenTofu and Terraform together in production?
Indeed, during transition periods, companies can operate both tools simultaneously due to their common state file format and provider compatibility. This concurrent operation facilitates phased migration approaches where teams can verify OpenTofu’s behavior against current infrastructure before fully committing to the change. The similarity of the command-line interface (simply substituting terraform with tofu) further eases the transition process.
One of the usual strategies for migration is to execute OpenTofu plan commands on the existing Terraform-managed infrastructure to confirm that the behavior is the same before changing tools. This process of verification can be included in the CI/CD pipelines to give assurance that OpenTofu will keep the infrastructure state as expected. Once it has been verified, the teams can start to use OpenTofu for new development while keeping the existing infrastructure with either of the tools.
For companies with intricate deployments, it’s usually best to adopt a step-by-step migration strategy. Begin by migrating less critical environments to help your team get used to any changes in workflow, then gradually move production workloads as your team becomes more comfortable. The shared state format means you don’t have to rush the migration, so your team can move at a pace that suits them while keeping the infrastructure stable.