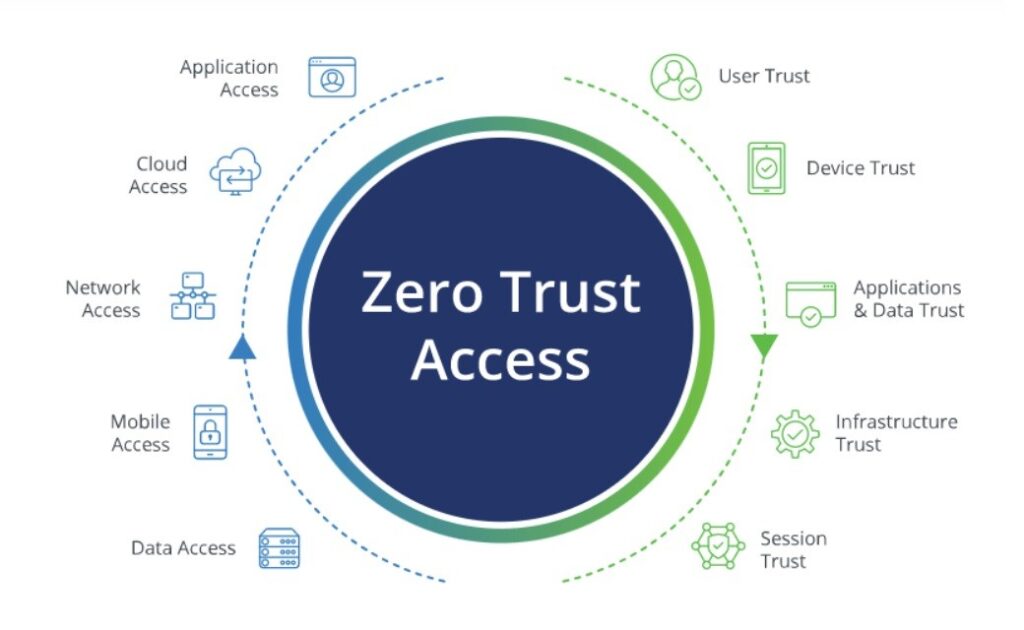
Summary
- Zero trust security is a departure from the traditional perimeter-based security approach as it verifies every access request regardless of origin, thus addressing the distributed nature of the modern cloud
- For a successful zero trust cloud migration, it is necessary to map data flows, identify protection surfaces, and design granular access policies before the migration begins
- Microsegmentation and least privilege access are fundamental principles of zero trust that minimize attack surfaces and significantly reduce the blast radius of potential breaches
- Organizations that use Zero Trust Network Access (ZTNA) see up to a 50% reduction in breach risk compared to traditional VPN solutions during cloud transitions
- Cloud migration presents a critical opportunity to rebuild security architecture around zero trust principles rather than trying to retrofit legacy approaches
Cloud migration offers significant business benefits but also introduces complex security challenges that traditional perimeter-based defenses are not equipped to handle. The distributed nature of cloud environments necessitates a fundamentally different approach to security—one that assumes a breach and verifies everything. Zero trust security provides this critical framework for cloud migration, ensuring protection when traditional network boundaries disappear.
Forrester Research has found that companies that use zero trust during their transition to the cloud see 37% fewer security incidents and are able to recover 44% quicker when breaches happen. This isn’t just about making security better—it’s about making sure businesses can transform securely in the age of the cloud.
Why Traditional Security Measures Aren’t Enough for Cloud Migrations
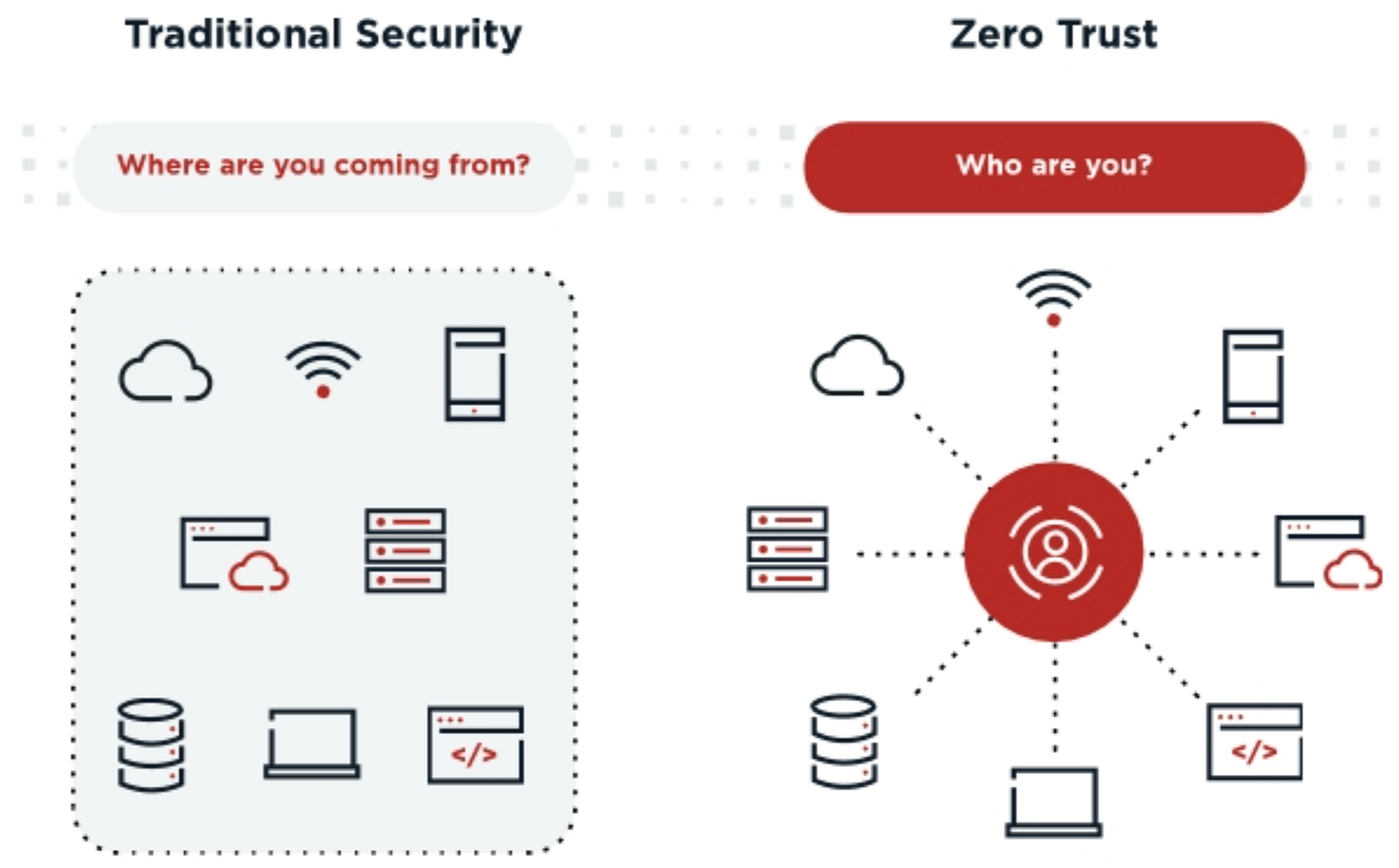
Traditional security models operate under the assumption that anything inside the network can be trusted, while anything outside the network cannot. This approach worked well enough when organizations had clearly defined network perimeters and maintained control over all their infrastructure. However, cloud migrations fundamentally challenge this model, highlighting the critical weaknesses of security that’s focused on the network perimeter.
Understanding the Issue with Perimeter Security
As you move to the cloud, the idea of a network perimeter that you can define becomes a thing of the past. Your data and applications are now spread across multiple cloud providers, data centers, and endpoints. The traditional security perimeter is now porous, distributed, and almost impossible to clearly define. Gartner predicts that by 2025, more than 85% of successful attacks on modern enterprise networks will take advantage of gaps in perimeter security models rather than using advanced malware.
The disappearance of boundaries means that security built on perimeter defense becomes increasingly ineffective. Firewalls, VPNs, and other traditional controls that rely on network location as a primary trust factor can’t adequately protect cloud-based resources that can be accessed from anywhere, by anyone, at any time.
Rapid Increase of Access Points in Cloud Settings
Moving to the cloud results in a significant increase in access points. Every new cloud service, API integration, mobile app, and remote employee creates possible ways into your environment. An average enterprise cloud setting may have thousands of access points that are constantly changing, compared to the handful of entry points in traditional network structures.
Security teams often find it incredibly difficult to keep track of and secure each possible entry point due to the access explosion. The 2022 IBM Cost of a Data Breach Report discovered that companies with complex security systems spread across multiple clouds had breach costs that were 54% higher than those with simpler, more integrated methods. This emphasizes the risk of attempting to secure too many disconnected access points using traditional tools.
How Cloud Migrations Are Vulnerable to Sophisticated Threats
Cloud migrations are a prime target for attackers due to the temporary security compromises, configuration errors, and visibility gaps that often occur during the transition period. Threat actors are aware that security teams are likely to be overwhelmed during this time and protective measures may be unstable. As a result, they are more likely to target organizations during migration periods.
Perimeter security was not designed to address the threat vectors that have evolved. Sophisticated supply chain attacks, API vulnerabilities, container escape exploits, and identity-based attacks that bypass traditional network controls entirely are faced by cloud environments. These attacks target the expanded attack surface created during cloud migration, exploiting the gaps between old security models and new technology realities.
Key Tenets of Zero Trust for Effective Cloud Migration
The zero trust security model fundamentally reimagines security architecture based on the idea that no user or system should be trusted by default. This model fits well with the requirements of cloud migration, offering a consistent framework that takes into account the distributed nature of cloud resources. Instead of adding security to cloud environments after migration, the entire migration process should be guided by zero trust principles.
“Zero Trust in Cloud Environments. First …” from araji.medium.com and used with no modifications.
The Foundation: Never Trust, Always Verify
Zero trust’s foundation is the removal of trust as an automatic assumption. All access requests must be completely authenticated, authorized, and encrypted before access is granted, regardless of the request’s origin. This principle is consistently applied to all resources, whether it’s the migration of legacy applications or the implementation of new cloud-native services.
Essentially, this involves substituting trust based on the network with verification based on identity at all levels. As workloads are shifted to the cloud, every connection—from user to application, from application to database, from microservice to microservice—must establish its own trust through rigorous verification procedures. This model offers consistent security that is effective in on-premises, hybrid, and multi-cloud settings.
Minimum Necessary Access Controls
Zero trust essentially limits access rights to only the minimum permissions necessary for users and systems to carry out their necessary functions. During cloud migration, this principle encourages a thorough reevaluation of access requirements instead of just copying existing permissions in the cloud environment.
Minimum Necessary Access Controls
Zero trust essentially limits access rights to the bare minimum permissions that users and systems need to carry out their necessary functions—no more than that. When migrating to the cloud, this principle pushes for a total reevaluation of access needs instead of just duplicating current permissions in the cloud setting.
In cloud environments, the first step to implementing least privilege is to identify the minimum access requirements for each role, application, and service. This often exposes significant over-privileging in current systems. Cloud migration is the perfect time to fix these access control problems instead of moving flawed permission models to your new environment. Studies have shown that 85% of data breaches involve compromised privileges, so this principle is essential for cloud security.
Microsegmentation: Limiting Lateral Movement
Microsegmentation splits your cloud environment into secure zones, establishing small perimeters around individual workloads or even particular applications. This method stops attackers from moving laterally through your environment, even if they manage to breach one element. In cloud environments, microsegmentation becomes even more essential as traditional network boundaries vanish.
Today’s cloud platforms come with built-in microsegmentation features such as security groups, service meshes, and container boundaries. When you’re planning your migration, you should map out how your applications communicate with each other and design segmentation policies that only allow the connections you need. This gives you a way to isolate your workloads, which can help limit the damage if there’s a security breach. A study by the Ponemon Institute found that organizations that used effective microsegmentation were able to reduce the cost of security breaches by 36% compared to organizations that didn’t use segmentation.
Cloud service providers such as AWS, Azure, and Google Cloud offer tools that make microsegmentation implementation much simpler than in on-premises environments. It is crucial to take advantage of these capabilities early in the migration planning process to ensure appropriate isolation is set up from the start.
Regular Checks and Validation
Zero trust isn’t a one-time solution—it demands regular checks and validation of security posture. Every access request, device state, and network flow needs to be recorded, examined, and validated against expected behavior patterns. Cloud environments offer comprehensive telemetry that allows this level of regular validation at scale, which is essential when dealing with cloud, hybrid cloud and multi-cloud architectures.
Make sure you have thorough monitoring in place from the very start of your cloud migration. Security monitoring tools that are native to the cloud can examine patterns across identity, endpoints, networks, and applications to identify any unusual activity that could signal a breach. This process of continuous verification makes sure that even if attackers manage to get hold of credentials or take advantage of vulnerabilities, their abnormal behavior patterns will set off alerts before they can do too much damage.
Developing Your Zero Trust Cloud Migration Plan
Implementing zero trust successfully needs a systematic approach that matches security transformation with your cloud migration path. Instead of considering security as an afterthought of migration, incorporate zero trust principles into every stage of your cloud adoption plan. This procedure starts with thorough discovery and planning long before workloads are transferred to the cloud.
Step 1: Chart Your Assets and Data Flows
Start by building a thorough list of all applications, data storage, and services that will be migrated to the cloud. This list should encompass not only the assets, but also their interconnections, dependencies, and data flows. Grasping how data moves through your systems unveils security needs and aids in spotting possible weaknesses during the migration.
Employ automatic discovery tools to create a network connection map, API calls, and user access patterns across your existing environment. This mapping process often uncovers shadow IT resources and unexpected data pathways that need to be secured during the migration. The accuracy of this mapping directly affects the success of your zero trust implementation, so spend the necessary time and resources on this crucial first step.
If you’re dealing with a complex environment, you might want to think about using data flow diagramming tools. These tools create visual representations of the connections between systems. These visuals can help stakeholders understand the security implications. They can also guide architectural decisions during the planning phase of cloud migration.
Step 2: Determine What Needs Protecting
Once you’ve charted your environment, you need to identify the most important assets that need protecting. Forrester refers to this as your “protection surface.” These high-value targets often include sensitive customer data, intellectual property, financial information, and vital operational systems. The primary goal of zero trust implementation should be to protect these critical assets first and foremost.
Make sure to record the specific security needs for each crucial asset. This should include the needs for regulatory compliance, the sensitivity of the data, and the business impact of a compromise. This analysis will form the basis for the design of the appropriate protection controls during the migration to the cloud. Keep in mind that your protection surface will probably evolve during the migration as you adopt new cloud services and as your data patterns change.
Step 3: Create Access Control Policies
Once you have defined your protection surface, create detailed access policies that follow the principle of least privilege. These policies determine who can access which resources, under what circumstances, and what actions they can take. Good policies take into account multiple contextual factors beyond identity, such as device security posture, geographic location, time of access, and behavior patterns.
Cloud environments allow for dynamic, context-aware policies that traditional on-premises systems could not support. You can design policies that take advantage of these capabilities, like restricting access to sensitive data to managed devices, limiting administrative functions to specific network locations, or requiring additional verification for unusual access patterns. Write these policies into code before migration begins to ensure consistent implementation across your cloud environment.
It’s important to use policy-as-code methods to create machine-readable access rules that can be consistently applied, tested, and updated across cloud environments. This programmatic approach to policy management is essential for maintaining zero trust at cloud scale.
Step 4: Keep an Eye on and Maintain Your Zero Trust Architecture
Set up thorough monitoring that gives you a clear view of your entire cloud environment. Successful zero trust monitoring brings together logs and telemetry from identity providers, endpoint management systems, network flows, and application behaviors to give a full picture of your security. This multi-faceted monitoring makes it possible to pick up on complex attacks that might otherwise slip through single-layer controls.
Modern cloud-based monitoring tools provide advantages in scalability and integration over traditional security information and event management (SIEM) systems. Many of these tools use AI to enhance their analytics, allowing them to identify anomalies and potential threats without needing manual rule creation. When choosing monitoring tools, it’s important to prioritize those that can integrate natively with your chosen cloud platforms and can correlate events across security domains.
Step 5: Automate Your Security Responses
It’s impossible for manual security measures to keep up with the sheer size and speed of cloud environments. Therefore, it’s crucial to put automated response capabilities into place that can react immediately when threats or policy violations are detected. These automated responses might include isolating compromised workloads, revoking access tokens, requiring additional authentication, or alerting security teams for further investigation.
Cloud security orchestration tools are capable of executing complex, conditional response workflows at machine speed. When designing automated responses, it’s important to balance security needs with operational impact. If you’re not careful, overly aggressive automation can create availability problems. Make sure to document your automated response procedures clearly and ensure that business stakeholders understand the potential operational impacts before implementation.
Identity and Access Management: A Must-Have for Cloud Migration
When it comes to zero trust cloud environments, identity is the main security boundary. A robust identity and access management (IAM) system is the backbone of your zero trust architecture, guaranteeing that only entities that have been authenticated and authorized can access resources. The process of cloud migration offers a chance to update identity systems and introduce more advanced access controls than those available in conventional environments. For more insights on cloud migration strategies, check out this Azure vs Google Cloud migration analysis.
Putting Multi-Factor Authentication to Work
Multi-factor authentication (MFA) is a powerful tool for reducing the risk of attacks that exploit credentials, as it requires more than just a password for verification. When migrating to the cloud, it’s a good idea to use MFA for all user access to cloud resources, administrative interfaces, and critical applications. Today’s MFA solutions offer a variety of authentication factors, including mobile authenticator apps, hardware tokens, biometrics, and contextual signals, to provide a balance of security and user experience.
Framework for Role-Based Access Control (RBAC)
- Instead of individuals, define role templates based on job functions
- For each role, implement the principle of least privilege
- Create separation of duties between sensitive functions
- Establish a regular certification process for role assignments
- Document approval workflows for role changes and exceptions
A well-designed RBAC framework simplifies access management while enforcing consistent security policies across your cloud environment. Start by analyzing existing roles and permissions, then redesign them to align with the capabilities of cloud service and security requirements. Most cloud providers offer native RBAC functionality that can be integrated with enterprise identity systems through federation.
During cloud migration, avoid typical RBAC implementation errors, such as creating roles that are too broad or failing to enforce role boundaries across cloud services. Role definitions should be specific enough to limit privileges but still be manageable at scale. The aim is to create a role architecture that meets business needs while limiting unnecessary access rights.
With cloud environments, there are new things to think about when it comes to role management, such as service accounts, roles that cross different clouds, and programmatic access. Your RBAC framework needs to deal with these cloud-specific identities in the same way it does with human users. Service accounts often get too many privileges during migration to make things work faster, but this is risky and can lead to major security issues.
Provisioning Access Just-in-Time
Provisioning access just-in-time (JIT) takes zero trust to a new level by only granting privileges when they are required and automatically taking them away after use. This method reduces standing privileges, which are one of the most frequent attack vectors in cloud settings. During cloud migration, using JIT access for administrative tasks, emergency access, and third-party integrations can significantly decrease your attack surface.
Securing Data in a Zero Trust Cloud
The primary objective of zero trust security is data protection—keeping sensitive data safe no matter where it’s stored or how it’s accessed. The process of cloud migration often scatters data across several environments, which adds complexity and creates more points of potential exposure. A good data protection strategy must rise to these challenges with uniform controls that follow the data wherever it goes.
Why You Need Full Encryption
Encryption is the cornerstone of data protection in the cloud. It keeps your information private even if someone gets around your access controls. Make sure you encrypt all sensitive data stores at rest. This includes databases, object storage, file shares, and backup repositories. Cloud providers make it easy to implement encryption. They offer native encryption capabilities that provide strong protection against unauthorized access.
It’s just as important to encrypt data in transit, which keeps it safe as it moves from one cloud service to another, to end users, and across hybrid environments. You should enforce TLS 1.2+ for all external connections and use service mesh encryption for internal microservice communications in containerized environments. API gateways can make sure encryption policies are consistently enforced across service boundaries, so no data flows are left unprotected during your cloud migration.
If you’re dealing with highly sensitive data, you might want to think about using application-layer encryption. This kind of encryption keeps your information safe from beginning to end, no matter what kind of infrastructure you’re using. Even if the cloud platform is compromised, your data will still be confidential. It’s a bit more complicated to put into place, but application-layer encryption offers the best protection for your most valuable data, both during and after you migrate to the cloud.
Mapping and Classifying Data
Effective data protection in a zero trust model starts with a thorough classification. All data should be classified according to sensitivity levels, regulatory requirements, and the impact on business. This classification should be consistent across on-premises and cloud environments, creating a unified approach to data protection no matter where it is located. Modern cloud data protection platforms can automate much of this classification process, using pattern recognition and context analysis to identify sensitive information.
Develop a map that pinpoints the location of your protected data within your system and how it moves between systems. This map is crucial for installing the correct controls during the migration process and ensures that no sensitive data is moved to the cloud without the proper protection. Many organizations discover locations of sensitive data that they were previously unaware of during this process, proving the importance of a thorough pre-migration assessment.
Develop well-defined procedures for dealing with each level of data classification, including requirements for encryption, access limitations, and retention policies. These procedures should be the basis for migration decisions, such as deciding which data needs advanced encryption or whether certain very sensitive information should stay on-premises while related systems are moved to the cloud.
Protecting Data While in Transit, at Rest, and in Use
It’s critical to ensure data protection at all stages of its lifecycle. In addition to the usual encryption at rest and in transit, you should also think about solutions that secure data while in use. This includes confidential computing enclaves that keep data encrypted even while it’s being processed. These advanced security measures are especially beneficial for heavily regulated sectors that deal with sensitive personal or financial data during cloud processing.
Set up data loss prevention (DLP) controls that keep an eye on and limit the movement of sensitive information across cloud boundaries. Cloud-native DLP solutions can spot unauthorized data transfers, stop accidental exposures, and enforce consistent protection policies across hybrid environments. These abilities become especially important during migration when data movement volumes increase dramatically.
When planning your cloud migration strategy, keep in mind the requirements for data residency. Many regulations limit where certain types of data can be stored and processed. Zero trust architecture needs to take these geographic restrictions into account while ensuring consistent security controls across regions. Cloud providers offer services specific to each region and guarantees of data sovereignty that can help meet these requirements.
Revamping Network Security for Cloud Migration
When migrating to the cloud, the network structure undergoes a significant shift. Traditional network-focused security needs to adapt to cater to the changing, distributed cloud environments without compromising robust protection. The principles of zero trust networks lay the groundwork for this security revamp, emphasizing secure connectivity over network location.
Out with the Old: VPNs and In with the New: ZTNA Solutions
For years, Virtual Private Networks (VPNs) have been the go-to for remote access. However, when it comes to cloud environments, VPNs fall short. Once authenticated, VPNs usually provide access to the entire network, which goes against the zero trust principle of least privilege. Zero Trust Network Access (ZTNA) solutions are the answer to these shortcomings. They offer access to specific applications without exposing the underlying network. So, when migrating to the cloud, replace your old VPN infrastructure with ZTNA for remote access needs.
Zero Trust Network Access (ZTNA) establishes direct, authenticated connections between users and specific applications, rather than allowing access to entire network segments. This approach reduces the attack surface and prevents lateral movement, even if credentials are compromised. Cloud-based ZTNA solutions provide scalability benefits for distributed workforces and make it easier to securely access cloud resources without complicated network configurations.
While picking ZTNA solutions, give priority to those that can be integrated with your current identity providers and can support both old applications and new cloud services. The migration period usually requires the support of both traditional and cloud-native access methods at the same time, which makes flexibility a crucial requirement for ZTNA implementation.
Putting Software-Defined Perimeter into Practice
Software-Defined Perimeter (SDP) frameworks take zero trust concepts and apply them to your whole network. They create dynamic, identity-based access controls that replace the static boundaries of your network. SDP creates a “dark” infrastructure that unauthorized users can’t see, which significantly reduces the attack surface that potential threats can target. During a cloud migration, SDP provides consistent security controls in hybrid environments where traditional network perimeters are no longer relevant.
Start implementing SDP by focusing on your most critical applications, then gradually expand to cover all cloud resources. Make sure to include strong device verification so that only managed, compliant endpoints can access sensitive cloud services. The Cloud Security Alliance found that organizations implementing SDP experienced 60% fewer network-based attacks than those using traditional perimeter defenses.
What to Consider for API Security
APIs are the main way services communicate in the cloud, and this presents new security issues that traditional network controls can’t handle. You need to make sure your API security is comprehensive, including authentication, authorization, encryption, and rate limiting for all exposed interfaces. Modern API gateways can give you these security features, and also let you see and control API traffic across your cloud environment.
When you’re planning your migration, make sure you list all your internal and external APIs, and write down what they need in terms of security and what their potential vulnerabilities are. APIs often don’t get as much attention when it comes to security as user interfaces do, which makes them a prime target for people who want to attack your system. Make sure you treat machine-to-machine API communications the same way you would treat communications from human users. Use strong authentication and make sure everything has the least privilege access it needs for all interactions between services.
Equipment and Techniques for Zero Trust Cloud Security
Rolling out zero trust throughout cloud environments necessitates a unified technology stack that covers identity, network, data, and application security areas. The appropriate tools provide the ability to enforce policy consistently at scale and offer the visibility necessary to identify and react to threats rapidly. Concentrate on solutions that provide native cloud integration and support hybrid deployments during the migration process.
Cloud Access Security with CASB Solutions
Cloud Access Security Brokers, or CASBs, are the gatekeepers between cloud services and users. They help control shadow IT and sanctioned cloud applications by providing visibility. During the migration process, CASBs help keep security policies consistent as workloads move to the cloud. This ensures that access controls, data protection, and compliance requirements stay the same across environments. The best CASB solutions offer API-based integration with the biggest cloud providers. This allows for deep visibility without causing performance issues.
Using SASE Frameworks for Wide-Ranging Security
The Secure Access Service Edge (SASE) merges network security and zero trust access services into a cloud-based structure that is ideal for widespread organizations. This combined approach makes managing security during cloud migration easier by bringing together several functions such as ZTNA, SWG, CASB, and FWaaS into a single service model. SASE structures are especially useful for organizations with highly spread out workforces that access cloud resources from a variety of locations and devices.
When you’re looking at SASE solutions, make sure you’re choosing platforms that will cover all of your planned cloud environment while still supporting your on-premises systems during the migration. The more you deploy SASE, the more consolidation benefits you’ll see, so try to choose solutions that can replace several point products instead of just adding another security layer to manage.
Security Platforms Built for the Cloud
Cloud providers have security services that are built specifically for their own environments. This results in a more streamlined management process and a tighter integration. These security platforms that are built for the cloud usually include network controls, identity management, threat detection capabilities, and data protection that are optimized for the provider’s architecture. During the planning phase of the migration, you should evaluate these built-for-the-cloud offerings and compare them to third-party alternatives. You should consider things like existing security investments, the need for multi-cloud, and specialized compliance needs.
Companies that are implementing multi-cloud strategies can benefit from cloud security posture management (CSPM) platforms. These platforms offer consistent oversight and policy enforcement across different environments. They consistently monitor cloud configurations against security best practices and compliance frameworks. This way, they can identify misconfigurations and vulnerabilities that could lead to security gaps during migration. CSPM tools are especially useful during the migration process. This is when rapid change increases the likelihood of overlooking security measures.
Security Tools That Automate and Coordinate
Security orchestration, automation, and response (SOAR) platforms are like a Swiss Army knife for cloud security. They handle a wide variety of tasks, from automating the mundane to coordinating responses to threats. They also ensure that policies are being followed, no matter how big the cloud gets. When a business is migrating to the cloud, SOAR solutions are particularly helpful. They can handle the increased complexity and alert volume that typically comes with cloud adoption. This frees up the security team to focus on making strategic improvements, rather than getting bogged down in manual processes.
Start using security automation early in your migration process, starting with common scenarios like user access reviews, vulnerability management, and incident triage. As your cloud presence grows, extend automation to include more complex scenarios like cross-cloud security monitoring and coordinated threat response. Organizations with mature security automation report significantly faster threat detection and response times compared to those relying on manual processes.
Breaking Down the Steps: How to Make Zero Trust Migration Doable
When it comes to zero trust implementation during cloud migration, it’s important to take a measured approach that balances enhancing security with operational requirements. Instead of trying to do a sweeping security overhaul all at once, most organizations find it more effective to do a phased implementation that focuses on the most important assets while keeping the business running smoothly. This step-by-step approach lets security teams learn from the initial deployments and fine-tune their strategy before taking on more complicated scenarios.
Start by Protecting Your Most Important Assets
Start your zero trust implementation by focusing on your most important data and applications first. These are the ones that would cause the most damage if they were compromised. This usually includes customer data, financial systems, intellectual property, and main operational platforms. By securing these most important assets first, you are protecting your most sensitive resources and gaining the skills needed for wider deployment. This approach also shows the value of security quickly, building organisational support for the zero trust initiative.
Considerations for User Experience During Rollout
Security enhancements that cause significant disruption to user workflows often face resistance and potential circumvention. It’s important to design your zero trust implementation with the user experience in mind, balancing the need for security with the need for operational efficiency. Techniques such as step-up authentication, contextual access policies, and transparent security controls can provide strong protection while minimizing friction for legitimate users. Keep in mind that if security is too difficult to use, it often gets bypassed, which can create greater risks than well-designed controls that users will actually use.
Ensure that users are aware of any security changes by explaining the reasons for new controls and how they protect the organization and individuals. Before implementing major changes, provide sufficient training and support resources, particularly for security-critical teams such as developers and administrators. Many organizations have found that a well-communicated security enhancement is met with much less resistance than a poorly explained one, even if the actual change is the same.
Procedures for Testing and Validation
Before you fully deploy zero trust controls, it’s important to test them thoroughly. This will help you identify any potential issues and make any necessary refinements to your implementation. Start with a small pilot group that represents different types of users. Gather feedback on how effective the security measures are and how they impact operations. Use this feedback to make adjustments to your policies and technologies before you roll them out on a larger scale. This can help prevent widespread disruption from unforeseen problems. It’s also important to continue testing throughout the implementation process. This will help ensure that your security controls continue to be effective as your cloud environment changes.
As part of your validation process, incorporate adversarial testing. This could involve red team exercises or penetration tests, which will help you pinpoint possible bypasses or weak spots in your zero trust setup. These aggressive security evaluations can offer useful information that tests focused on compliance might overlook. They can show you how skilled hackers might be able to get around your controls. Make sure to deal with any vulnerabilities that are identified right away. Use these as chances to learn and enhance your overall security framework.
How to Evaluate the Success of Zero Trust in Your Cloud Environment
Security is not a one-and-done deal. It requires ongoing measurement and enhancement. Set clear metrics that show how well your zero trust implementation is working in technical, operational, and business areas. These metrics give you insight into security improvements, help you decide where to allocate resources, and prove the value to the organization’s leaders. Without metrics, you’re just pouring money into security without knowing what you’re getting back.
|
Metric Category |
Example Metrics |
Target Improvements |
|---|---|---|
|
Access Control Effectiveness |
Unauthorized access attempts, privilege escalation incidents, access policy violations |
Reduction in successful unauthorized access events, faster detection of credential misuse |
|
Threat Protection |
Mean time to detect/respond, incidents contained at initial access point, lateral movement attempts |
Shorter detection and response times, increased containment of threats before lateral spread |
|
Data Protection |
Data exfiltration attempts, DLP policy violations, encryption coverage |
Reduction in data exposure events, increased visibility of sensitive data movements |
|
Operational Impact |
User experience ratings, help desk tickets for security issues, authentication success rates |
Reduced friction for legitimate users while maintaining strong security posture |
Track these metrics over time to demonstrate security improvements and identify areas requiring additional attention. Effective measurement requires establishing a pre-implementation baseline, setting realistic improvement targets, and regularly reviewing progress against those goals. Cloud environments provide rich telemetry that enables more sophisticated security measurements than were possible in traditional infrastructure.
Communicate security metrics to business stakeholders in a language they understand and in a way that shows the value to the business rather than just the technical details. For instance, instead of saying “reduced privilege escalation events,” say “decreased risk to customer data” to help non-technical leaders understand why investing in zero trust is important. This kind of reporting, which is aligned with business goals, helps maintain support for security initiatives during and after the migration to the cloud.
Crucial Performance Metrics for Zero Trust
Establish a balanced scorecard of performance metrics that gauge both leading indicators (like policy compliance and control coverage) and lagging indicators (like incidents and recovery times). Leading indicators give early warning of possible security gaps, while lagging indicators show actual security outcomes. Combined, these metrics provide a complete picture of your zero trust effectiveness. Crucial performance metrics include the percentage of access requests authenticated with MFA, time taken to revoke access for departed employees, the percentage of traffic protected by encryption, and the average time to detect security incidents.
Tools for Assessing Security Posture
Use automated tools that will consistently assess your security posture against zero trust principles and industry standards. Cloud security posture management (CSPM) platforms can find misconfigurations, compliance gaps, and security risks in complex cloud environments. These tools give you objective measures of how your security has improved over time and will show you areas that need remediation before they result in breaches.
Supplement automated evaluations with regular manual checks by in-house security groups or outside professionals. These more in-depth assessments can uncover structural flaws, procedural deficiencies, and new threats that automated systems may overlook. To ensure that quick change doesn’t lead to unexpected vulnerabilities, many businesses perform security checks on a quarterly basis during cloud migration.
Framework for Continuous Improvement
Form a systematic method for turning security metrics into tangible enhancements. This framework should incorporate routine review periods, distinct responsibility for security discoveries, and ways to prioritize correction efforts based on risk. Zero trust is not a goal but a continuous process that requires consistent refinement as threats, technologies, and business requirements change. Organizations with advanced improvement processes usually review security metrics weekly at operational levels and monthly with leadership, making sure that insights lead to action instead of just producing reports.
Staying Ahead: Adapting Your Zero Trust Model
Cloud tech and security risks are always changing, so your zero trust model needs to be able to change with them. When you’re designing your model, make sure it’s flexible and can be extended if needed. Try to avoid anything too rigid that might limit what you can do in the future. Looking ahead like this makes sure that the money you put into security will still be worth it as your cloud environment gets more advanced and your business needs shift.
Getting Used to New Cloud Services
Cloud providers are always launching new services that can be beneficial to businesses, but might need some changes to the security model. Set up governance processes that will look into the security implications before taking on new cloud capabilities, making sure that zero trust principles apply to these services too. This approach of designing security prevents the build-up of security debt that often happens when business teams take on new technologies without the right controls.
Wherever possible, you should create abstraction layers between your security policies and the specific technologies you’re using to implement them. This abstraction will enable you to replace underlying tools and services without having to redesign your entire security model. For instance, you should define authentication requirements independently of specific identity providers. This will allow you to switch providers or add new ones without having to change your fundamental approach to security.
Zero Trust Cloud Migration Security with Best Practices and Strategy
“Zero trust is a necessary move from complex, bolted-on solutions to an integrated, intelligent, and proactive approach, focusing on key technologies like ZTNA and AI for adaptive security” — Gartner Research Note on Zero Trust Evolution
Emerging technologies such as artificial intelligence, quantum computing, and advanced biometrics will have a significant impact on security capabilities and threats. Security analytics driven by AI can improve threat detection and automate complex policy decisions. At the same time, quantum computing may eventually necessitate fundamental changes to encryption methods. Keep an eye on these technological trends and their security implications. Adjust your zero trust roadmap to incorporate beneficial innovations and prepare for new threat vectors.
Instead of focusing solely on specific technological expertise, invest in security teams with a wide range of skills and a willingness to learn. Security professionals who can adapt to changing technologies and threat landscapes are often more valuable in the long run than those who are narrowly specialized in current tools. This human ability is often the most important factor in maintaining effective security as environments change.
Think about how edge computing, 5G networks, and Internet of Things (IoT) technologies could widen the boundaries of your cloud environment. These technologies pose new security challenges by spreading out processing and data over an even larger landscape. Zero trust principles become even more crucial in these expanded environments, but the ways they’re implemented might need to be tweaked to account for devices with limited capabilities and spotty connectivity. If you’re considering a move to the cloud, it’s essential to understand the potential risks, such as cloud vendor lock-in, and how to mitigate them.
Stay connected with security communities, keep up to date with your cloud provider’s plans, and stay informed with industry research to predict major changes before they affect your environment. This forward-thinking approach lets you make strategic modifications instead of reactive changes when new technologies or threats appear.
Common Questions
When companies are going through the process of migrating to the cloud, there are some questions that often come up about zero trust implementation. These questions are valid and reflect real concerns about the complexity of implementation, the impact on the business, and the challenges that might be faced. By clearly answering these questions, it helps to get everyone in the organization on the same page and sets realistic expectations for what the journey to zero trust will look like.
- How does zero trust impact legacy applications during cloud migration?
- What are the financial implications of deploying zero trust security?
- Do we require specialized staff to manage a zero trust architecture?
- How do we calculate ROI from zero trust investments?
- Can zero trust be deployed incrementally or is it an all-or-nothing approach?
These questions underscore important considerations in your zero trust planning. While there’s no universal answer to these concerns, understanding the principles and adapting them to your unique environment allows you to effectively address these challenges. The following sections delve into the most common implementation questions in more detail.
Keep in mind that zero trust is a major change in security thinking, not just technology. Cultural and procedural shifts often pose more problems than technical execution. Put resources into change management, education, and transparent communication to assist your company in adjusting to this new security method during cloud migration.
Switching to zero trust often introduces a temporary layer of complexity as businesses move away from traditional models and towards more contemporary security structures. This complexity should be recognized and accounted for, with the understanding that the final product will provide better security and often simpler operations than maintaining older methods in cloud environments.
What is the typical timeline for implementing Zero Trust for cloud migration?
Implementing zero trust can take different amounts of time depending on the size of the organization, the complexity of the technology, and the availability of resources. Most businesses are able to establish the basic foundations of zero trust for their most important assets within 6-12 months. However, it usually takes between 18-36 months to fully implement zero trust across all systems. Organizations that are cloud-native or have up-to-date technology stacks are usually able to implement zero trust more quickly than those with a lot of legacy infrastructure. Instead of thinking of zero trust as a single project with a set end date, the most successful organizations see it as an ongoing process of improving security capabilities.
Is it possible to apply Zero Trust in hybrid cloud settings?
Zero trust principles are just as applicable to hybrid environments that span on-premises infrastructure and multiple cloud providers as they are to any other setting. In fact, zero trust is even more critical in hybrid deployments where maintaining traditional perimeter security is not possible. The implementation approach may require additional integration work to establish consistent identity, policy enforcement, and monitoring across diverse environments. Cloud security brokers, identity federation, and unified policy frameworks are key to extending zero trust consistently across hybrid architectures. Many organizations find that implementing zero trust during cloud migration actually simplifies hybrid security by creating a consistent model that works across all environments.
What are the main obstacles in Zero Trust cloud migration?
The biggest obstacles usually involve managing legacy applications that were not built for zero trust models, integrating various identity systems, maintaining performance while incorporating security verification steps, and shifting organizational security culture from perimeter-focused to verification-focused thinking. Technical debt in existing systems often complicates implementation, necessitating additional adaptation layers or fast-tracked modernization of essential applications.
Security teams often struggle with resource constraints, especially when they are tasked with managing current security operations while also introducing new zero trust capabilities. Organizations often fail to properly assess the operational impact of changes to security, which can lead to pushback when users find their workflows disrupted. The key to successful implementations is to carefully manage changes, communicate clearly, and roll out changes in phases to minimize disruption while gradually improving security.
How does Zero Trust influence the performance of cloud applications?
If correctly applied, zero trust should have a negligible effect on application performance while significantly enhancing security posture. Modern cloud-based security services distribute the workload of verification across global points of presence, reducing latency impacts compared to centralized security models. Techniques such as token caching, risk-based authentication, and parallel processing can further decrease performance overhead while maintaining robust security verification.
Adding new security layers during implementation can cause some initial performance impact, especially for legacy applications that weren’t designed with zero trust principles. These impacts can usually be mitigated through optimization, caching strategies, and architectural adjustments. Cloud-native applications designed for distributed verification generally experience minimal performance penalties from zero trust implementation.
In your zero trust planning, you should consider performance, establish baseline measurements before implementation, and monitor regularly throughout the process. This focus on performance ensures that security enhancements do not compromise crucial application responsiveness or user experience.
- Before putting new security controls into place, set performance benchmarks
- Carry out load testing with security controls turned on
- Put caching strategies into place for access patterns that are verified frequently
- Think about the geographic distribution of security services to keep latency to a minimum
- Make performance-sensitive applications a priority when optimizing
How does Zero Trust differ from traditional cloud security?
Traditional cloud security often mirrors the approaches used on-premises, with a heavy reliance on perimeter defenses, network segmentation, and trusted zones. This model operates on the assumption that, once initial authentication has taken place, traffic within certain boundaries can be trusted. This creates opportunities for lateral movement once perimeters have been breached. Zero trust rejects this assumption completely, requiring every access request to be verified continuously, regardless of where it originates or its network location.
Traditional models concentrate on safeguarding network boundaries, but zero trust shifts the focus to safeguarding the resources themselves. This is done through robust identity verification, least privilege access, and ongoing monitoring. This resource-focused approach is a better fit for cloud architectures, where traditional network boundaries are either fluid or non-existent. Zero trust also emphasizes end-to-end encryption and protections at the data level, rather than relying solely on network transport security.
What’s most important about zero trust is that it represents a strategic change in thinking. Instead of viewing a breach as an exception, it is viewed as the starting point. This change in perspective results in fundamentally different security design decisions. The focus becomes minimizing the potential for damage rather than just preventing initial access. When organizations fully embrace this change in thinking, they often find security weaknesses in their existing cloud implementations. These weaknesses were previously hidden under traditional security assumptions.